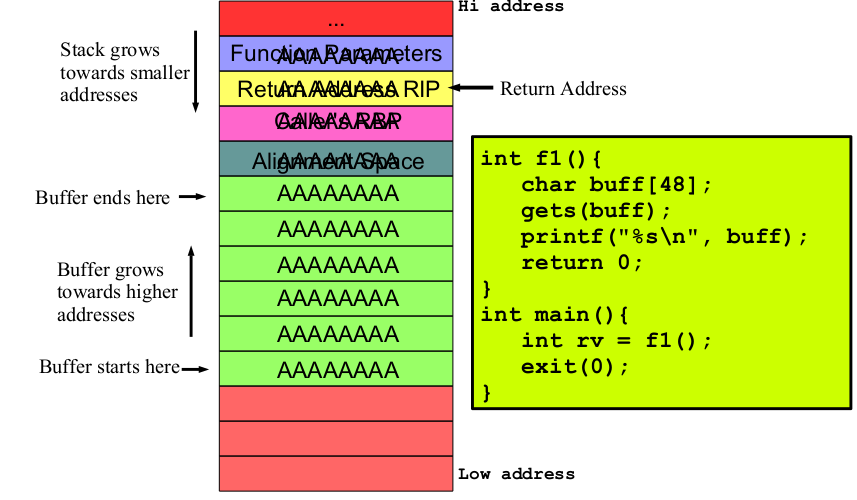
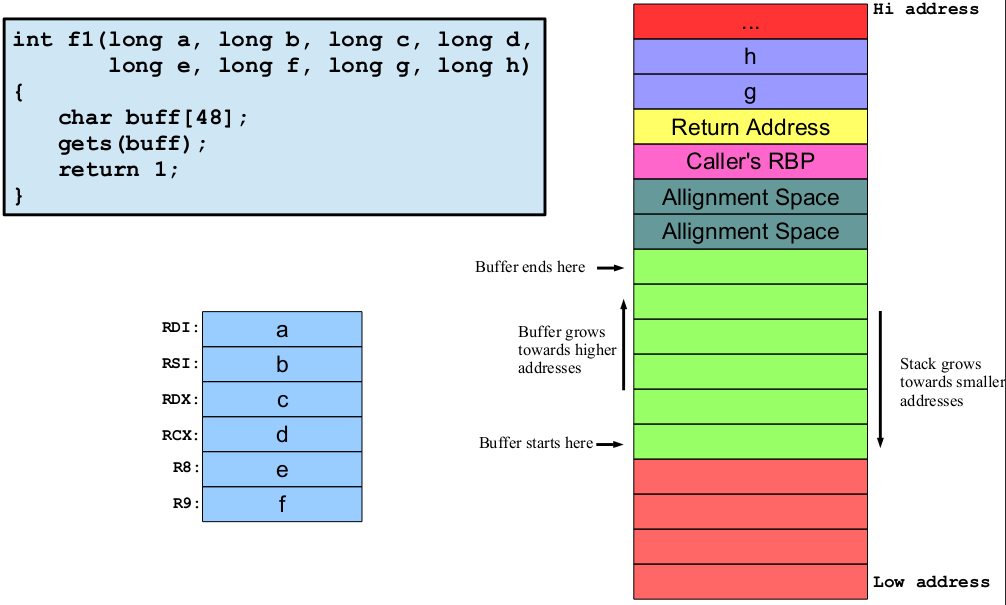
A buffer overflow is a bug in a program, which occurs when more data is written to a block of memory than it can handle. This can be stack based, heap based, integer overflow, off-by-one, and a format string.
Cyber-security encompasses all the techniques for protecting computers, networks, programs, and data from unauthorized access or attacks that are aimed for exploitation.
A vulnerability is a flaw/weakness in a system design, implementation or security procedure that could be exploited resulting in notable damage. Example is a house with a weak lock on the main door. A zero- day vulnerability is a vulnerability that has been disclosed but is not yet patched. An exploit that attacks a zero-day vulnerability is called a zero- day exploit.
An exploit is a software that take advantage of a vulnerability leading to privilege escalation on the target. Example of an exploit is the duplicate key with the robber using which he/she can enter the house.
A payload is actual code which runs on the compromised system after exploitation. Example is the task that the robber will perform inside the house, i.e., stealing jewelry and cash.
- Stack overflow
- Shellcode
- Exploit
- Buffer Overflow
- Bypassing Non-eXexcutable bit
-
The first published paper on this vulnerability was published in 1996 by Aleph One with the title of “Smashing The Stack For Fun And Profit”, and later revived by Avicoder in 2017.
-
Buffer overflow exploit was first used by Morris Worm in 1988, followed by Code Red Worm in 2001 and Slammer worm in 2003. It is still one of the top vulnerability which cover a wide range of computer applications, libraries, operating systems and networking
-
Hackers mostly use buffer overflows to corrupt the execution stack of a web app. By transferring fully crafted input to a web app, a hacker can make the web app to execute arbitrary code and probably taking over the server.
-
Although there are many h/w and s/w based techniques and tools that have been proposed and developed to detect and protect from buffer overflow vulnerability, but based on the trend it look likes this problem will continue to happen.
Certainly, let's dive into the details of a classic Buffer Overflow (BOF) vulnerability and how hackers exploit it step by step
Hackers identify a software component (such as a function) that doesn't properly validate input size. This component allocates a fixed-size buffer (e.g., an array) to store user-provided data.
The hacker crafts input data that exceeds the buffer's allocated size. The extra data overflows into adjacent memory, potentially overwriting other variables or control structures.
The hacker's goal is to manipulate the function's return address, stored on the stack, to point to their malicious code (shellcode). They craft the payload so that the buffer overflows and overwrites the return address.
The stack frame of the vulnerable function includes local variables and the return address. By controlling the return address, the hacker can redirect the program's execution flow.
The hacker places their shellcode in the payload, often represented by assembly instructions. The payload could be a sequence of instructions to spawn a shell, download malware, or perform other malicious actions.
When the vulnerable function returns, the manipulated return address points to the shellcode, not the legitimate caller. This redirection leads to the execution of the hacker's shellcode.
The shellcode executes, granting the hacker control over the compromised system. The attacker can issue commands, access files, or exploit further vulnerabilities.
If the exploited function has elevated privileges (e.g., runs as administrator), the hacker gains the same privileges.
Hackers may use NOP sleds to increase the chance of hitting the shellcode precisely. They may also modify the payload to avoid detection by intrusion detection systems.
The hacker might set up backdoors or exploit other vulnerabilities to maintain access or pivot to other systems.
To cover their tracks, attackers erase logs, manipulate system settings, or deploy anti-forensics techniques.
The NX (No-eXecute) bit, also known as the XD (eXecute Disable) bit, is a hardware-based security feature found in modern computer processors. It is designed to prevent the execution of code stored in certain memory regions, primarily as a defense against various types of malicious software attacks, including Buffer Overflow (BOF) attacks and code injection.
gcc -z execstack programname.c- The NX bit doesn't prevent all types of code execution attacks, such as those that involve abusing legitimate code sequences.
Before calling a function, the program places a random value (the stack canary) between the local variables and the return address on the stack. After the function executes, before it returns, the program checks if the canary value has been modified.
gcc -fno-stack-protector programname.c- Stack canaries cannot prevent all types of buffer overflows or attacks that don't target the return address.
ASLR randomizes the starting addresses of various memory segments, including the stack, heap, libraries, and executable code, in a process's address space. This randomization is applied when the process starts, making it challenging for attackers to predict memory locations.
echo 0 | sudo tee /proc/sys/kernel/randomize_va_spacePIE is an extension of ASLR that focuses specifically on the executable code and data of an application.In a non-PIE executable, the base address of the program's code is fixed, making it easier for attackers to predict and target specific memory locations. With PIE, the base address of the executable's code is randomized each time the program is executed.
gcc -no-pie programname.c- Like ASLR, PIE is not foolproof and doesn't prevent all possible exploitation scenarios.
- PIE may introduce a small performance overhead due to the need to adjust relative offsets during runtime.
Fortify Source is integrated into the software development lifecycle, helping developers find and fix issues early in the development process. It can be integrated into integrated development environments (IDEs) or run as part of automated build processes. Fortify Source allows organizations to define their own security rules and policies based on industry best practices, compliance requirements, and internal security standards.
gcc -D_FORTIFY_SOURCE -O2 programname.c#include <stdio.h>
#include <stdlib.h>
int main(){
printf("I am High level Language C\n");
exit(0);
}SECTION .data
message db "I am High level Language C", 0
SECTION .text
global main
extern printf, exit
main:
push message
call printf
add esp, 4
push 0
call exit| Assembly Code | Hexadecimal Machine Code |
|---|
push message | 68 xx xx xx xx
call printf | E8 xx xx xx xx
add esp, 4 | 83 C4 04
push 0 | 6A 00
call exit | E8 xx xx xx xx
Assembly language plays a crucial role in buffer overflow exploits. Buffer overflow exploits involve manipulating the memory contents of a vulnerable program to overwrite critical data, such as function return addresses, and redirect the program's execution flow to malicious code. Assembly language is used to craft the shellcode or payload that will be injected and executed in the compromised system's memory.
- Check
Assembly languagefrom my intelx86-64 repository where I explained assembly from zero with examples in detail. - Endianness
- Flag Registers
- General Purpose Registers
- Functions
- Function calling conventions
- Stack Behind the Curtain from system programming.
- Basic Assembly Instructions
- GDB
- BOF01
- BOF 02
- BOF in detail
- Buffer Overflows
- Binary Exploitation
- Buffer Overflow Attack
- Buffer Overflow Defenses
- Bypass defenses
- Stack Guard
- Learning C
- Operating System
- System Programming
- Socket Programming
- Linux Utilities
- Programming Concepts
- Resources
Best Regards - Mehar Ehsaan