- Adrien Wu, Hsiang-Jui Lin: Tor Onion service storage and virtual file system
- Hsing-Yu Chen: Data block API
- Chih-Hao Wang, Yang Han Li: Reports and documentation
The TorFS project was initiated as a final project in NTU Cryptography and Network Security course. It was motivated by dnsfs and pingfs. We explored the similar idea, which exploits storage from protocols which was not intended for this purpose. We discovered Tor hidden services can be regarded as reliable and retrievable data storage.
Before involving into TorFS, it's better to understand Onion services (formerly, hidden services). It provides anonymity to websites and other services beneath Tor's Onion network. Tor website already has a good explanation on Onion services. A 10-minute reading is worthwhile for those who want to know about it.
To setup an Onion service, we generate a private/public long-term key pair as our service indentity. Currently Tor allows Ed25519 or RSA1024 keys. We advertise our service named XYZ.onion or some by asking introduction points, basically Tor relays, to store our public keys. Whoever client visiting our service should learn about our public key, and setups up a rendezvous point for futher contact.
However, we only need to store data without an actual Onion service. It turns out the introduction points, along with our public keys, can survive even the actual service is absent. As you can figure out, we put the stuffs into public keys and retrieve them back using .onion addresses! That's basically how TorFS works.
In detail, we derived an algorithm to generate 1024-bit RSA keys, where 800 out of 1024 bits in n component (product of two primes) can contain arbitrary data. We manipulate the remaining bits to satisfy RSA's constraints. Then, we build a virtual file system that slice the files into 800-bit blocks, distribute them to introduction points, and keep track of the replicas by .onion addresses.
Since the our code uses async features, it requires Python 3.7 minimum.
Install depent pacakges using pip or other package manager:
pip3 install -r requirements.txtMake sure you start the Tor daemon and configure it to allow Onion services.
Run python3 ./src/main.py to start TorFS shell.
torfs> help # Ask help to learn about command usages
torfs> cp @demo/demo.jpg demo.jpg # Upload our demo.jpg to Tor network
torfs> ls . # List directory in virtual fs
demo.jpg
torfs> cp demo.jpg @demo_copy.jpg # Download the file back
torfs> exit
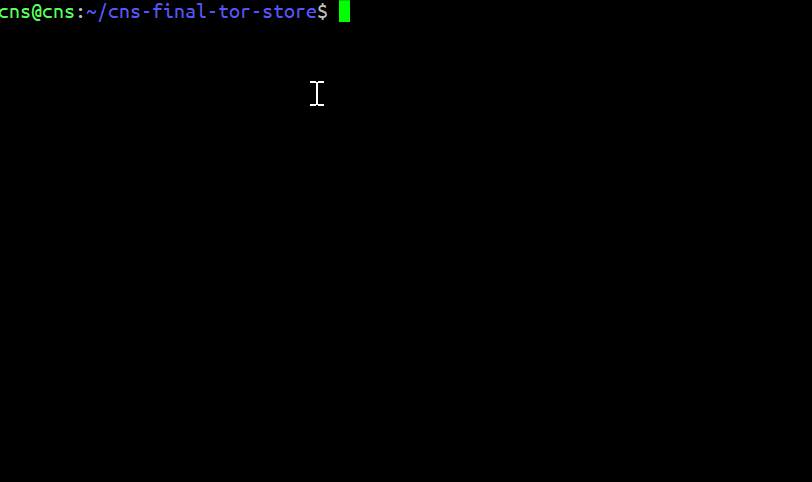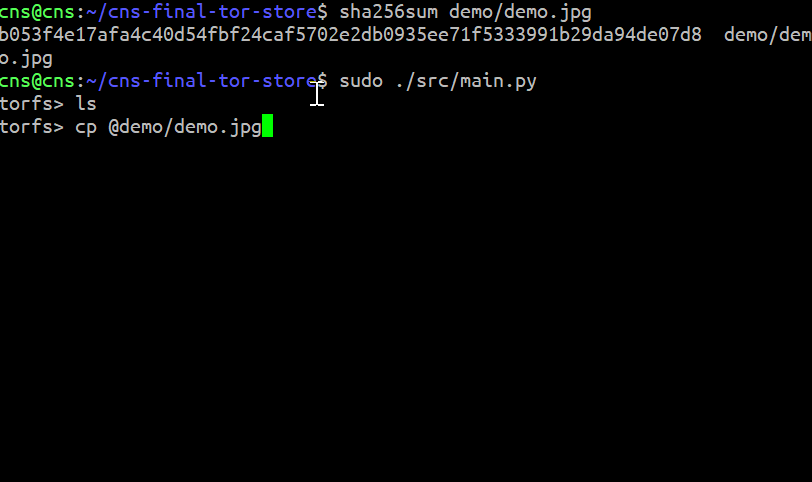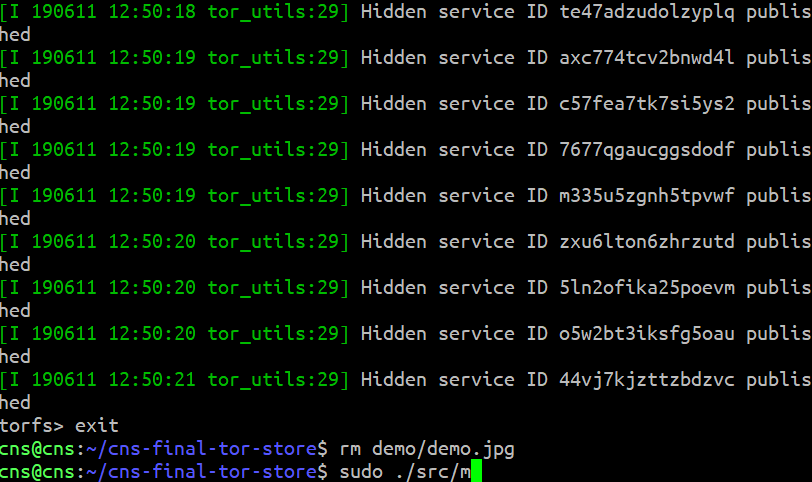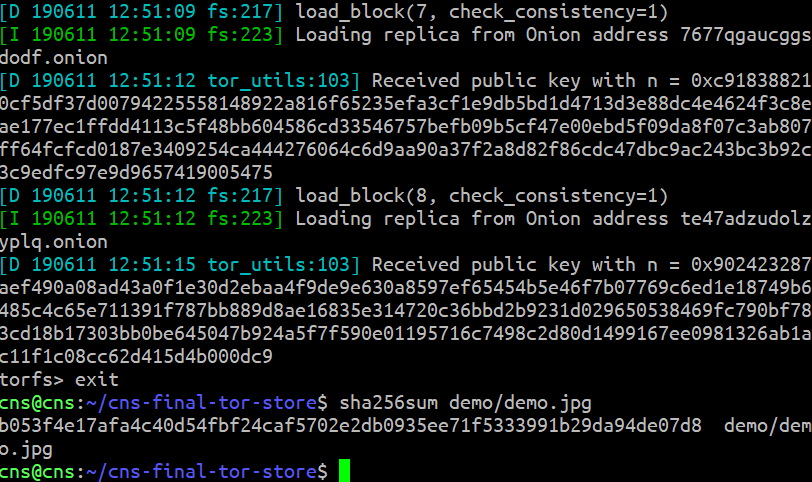
Following the demo above, we expect identical file contents.
$ sha256sum demo_copy.jpg demo/demo.jpg
b053f4e17afa4c40d54fbf24caf5702e2db0935ee71f5333991b29da94de07d8 demo_copy.jpg
b053f4e17afa4c40d54fbf24caf5702e2db0935ee71f5333991b29da94de07d8 demo/demo.jpg
- The project is intended to as a proof-of-concept and for educational purpose. Do NOT distribute it for malicious means.
- We have limited time to complete our project. The code is not guaranteed to be bug-free, and thus not suggested for production use.
MIT