With the rise of Machine Learning IT Security might look different in a few years. This repository is a CTF challenge, showing a security flaw in most (all?) common artificial neural networks. They are vulnerable for adversarial images.
This challenge not only requires from you to analyse the website, but also some data handling and number crunching is required.
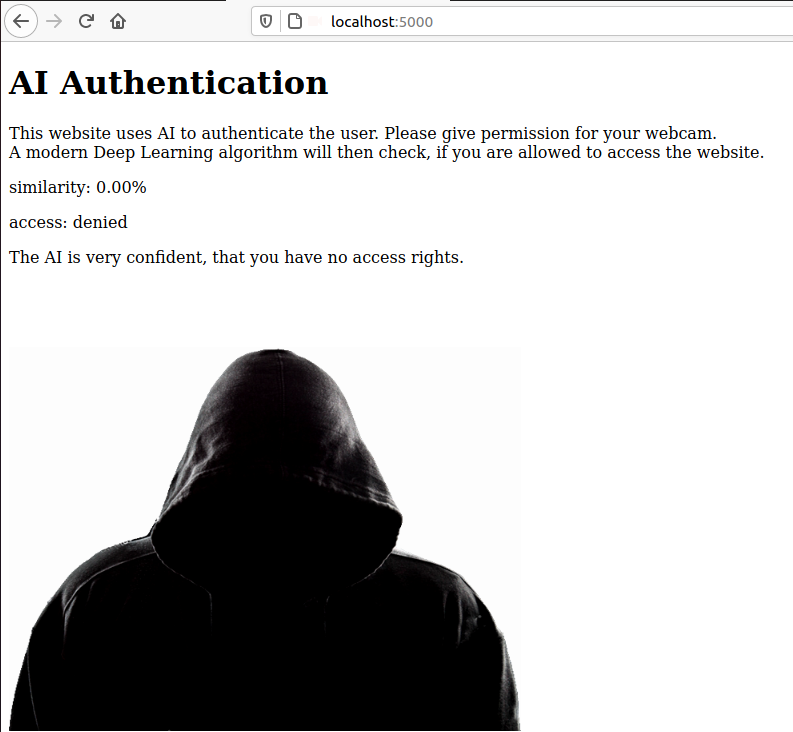
The challenge is to login into the website. The authentication is done by a Machine Learning model in the backend. It is able to identify valid users by an image from your webcam. You have solved the challenge when the website says "You are authenticated".
This challenge is similar to existing challenges, e.g. hackmit-puzzle-2017-tinbot and UTCTF-19-facesafe. However in this one you won't have access to the model parameters, which makes it black box in regards to the Machine Learning model.
The easiest way to install and run the webserver is by using docker. Just pull and run the docker image.
docker pull arturmiller/adversarial_ml_ctf
docker run -it -p 5000:5000 --name=adversarial_ml_ctf arturmiller/adversarial_ml_ctfNow you can access the website locally (http://localhost:5000) with any browser. I recommend to access the website from the same machine, where the container is running. For security reasons most browsers block opening the webcam if the connection is not secure (http instead of https). The only exception localhost.
You actually don't need a webcam to solve this challenge. On Ubuntu you can create a fake webcam with v4l2loopback and pyfakewebcam.
sudo apt-get install -y v4l2loopback-dkms
pip3 install pyfakewebcamRunning v4l2loopback should create a fake device "/dev/video0".
sudo modprobe v4l2loopback exclusive_caps=1Now you can stream images with pyfakewebcam.
If you want to build the Docker image on your, download the source code and build it with docker.
git clone https://github.com/arturmiller/adversarial_ml_ctf.git
cd adversarial_ml_ctf
docker build -t adversarial_ml_ctf .You can run the image with:
docker run -it -p 5000:5000 --name=adversarial_ml_ctf adversarial_ml_ctfIf you want to run the webserver without Docker you need Python3 on your machine.
Then download the source code and install the dependencies:
git clone https://github.com/arturmiller/adversarial_ml_ctf.git
cd adversarial_ml_ctf
pip3 install -r /requirements.txtRun the webserver with:
python3 main.pyYou can find the solution of this challenge in the adversarial_ml_ctf repository.