This content pack install a pipeline (with pipeline rules) and a grok pattern.
This pipeline parse fail2ban log received with a GROK pattern to create fields such as clientip to use with Graylog Geolocation.
2020-03-27 20:16:27,162 fail2ban.actions [2667]: NOTICE [sshd] Ban 1.1.1.1
f2b_timestamp: 2018-02-09 10:05:21,431
action: Ban
clientip: 1.1.1.1
digit: 2667
log_level: NOTICE
method: actions
service: sshd
src_app: fail2ban
I personally use filebeat to collect logs.
To better filter logs this pipeline rule search for specific additional field called log_application with the value of fail2ban.
You can customize this field as you want editing content-pack.json
"source": {
"@type": "string",
"@value": "rule \"Is Fail2ban\"\nwhen\n has_field(\"log_application\") and to_string($message.log_application) == \"fail2ban\"\nthen\nend"
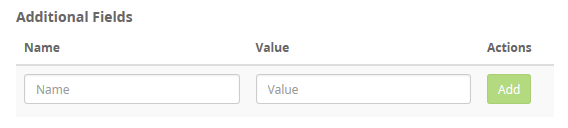
}You can add additional custom fields directly from Graylog Beats Input Configuration
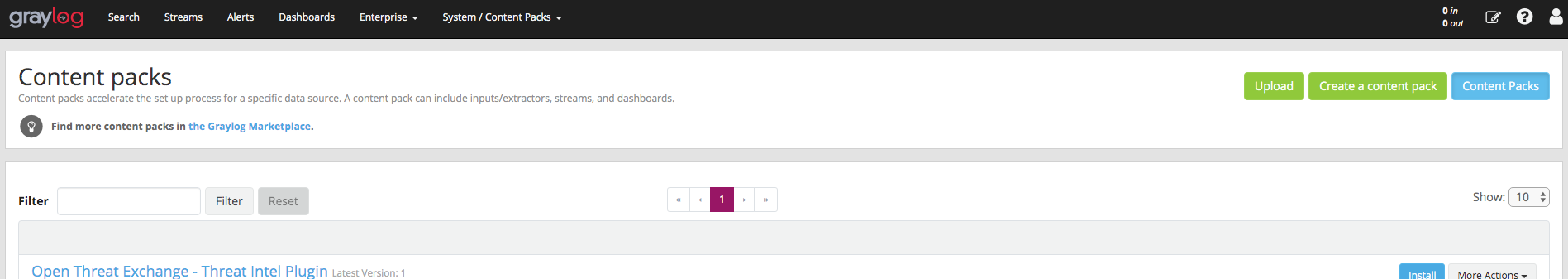
Go to Graylog Admin Interface -> System -> Content Packs then click Upload button and select content-pack.json file.
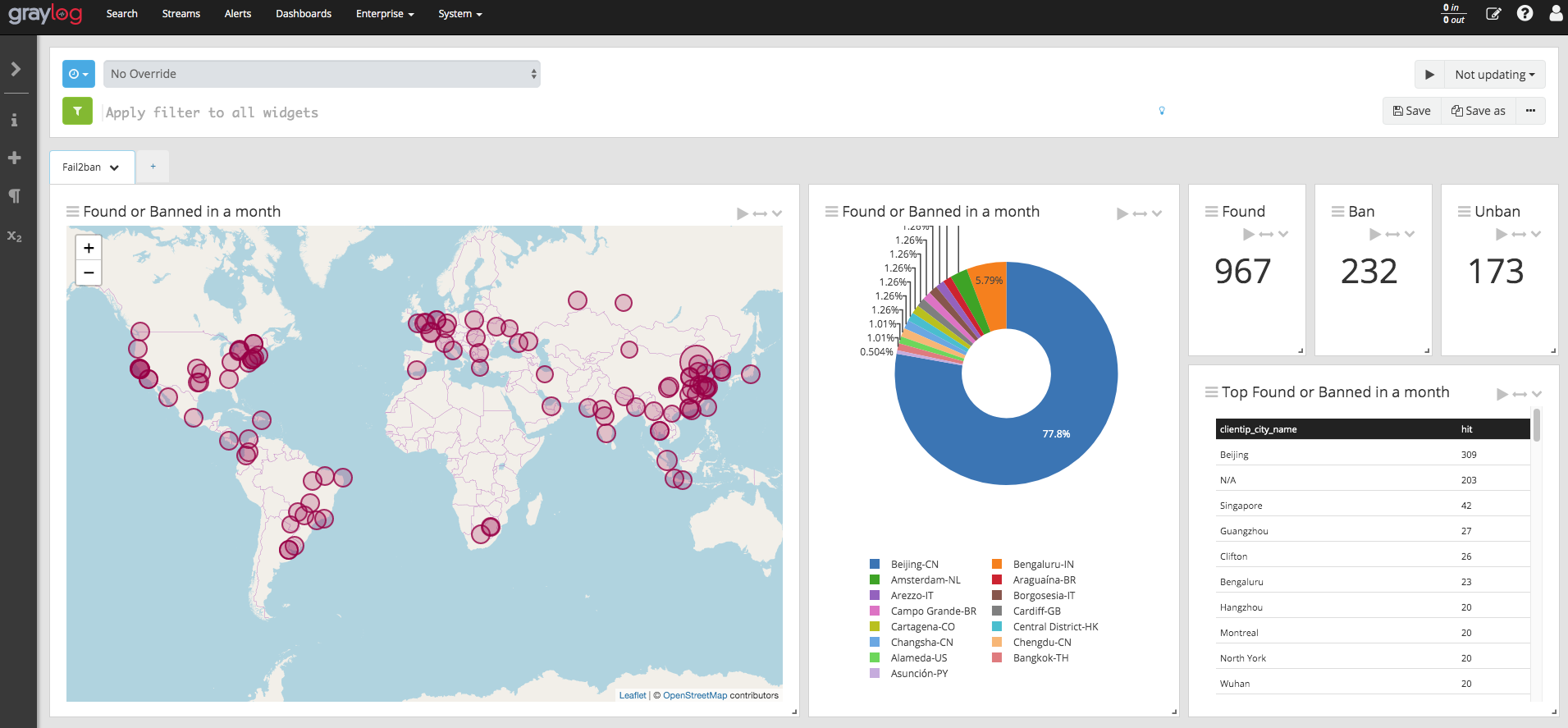
Follow the instructions to enable Graylog Geolocation and you will be able to create your dashboard.
GROK pattern was inspired from https://github.com/kurobeats/Fail2ban-GROK-Log-Pattern/blob/master/27-fail2ban_log.conf
This project is licensed under the MIT License.
See LICENSE.md for details.