Scripts for the Ghidra software reverse engineering suite.
Readme in other languages: English, 简体中文
In the Ghidra Script Manager click the "Script Directories" icon in the toolbar and add the checked out repository as a path.
Some utility used by other Ghidra scripts.
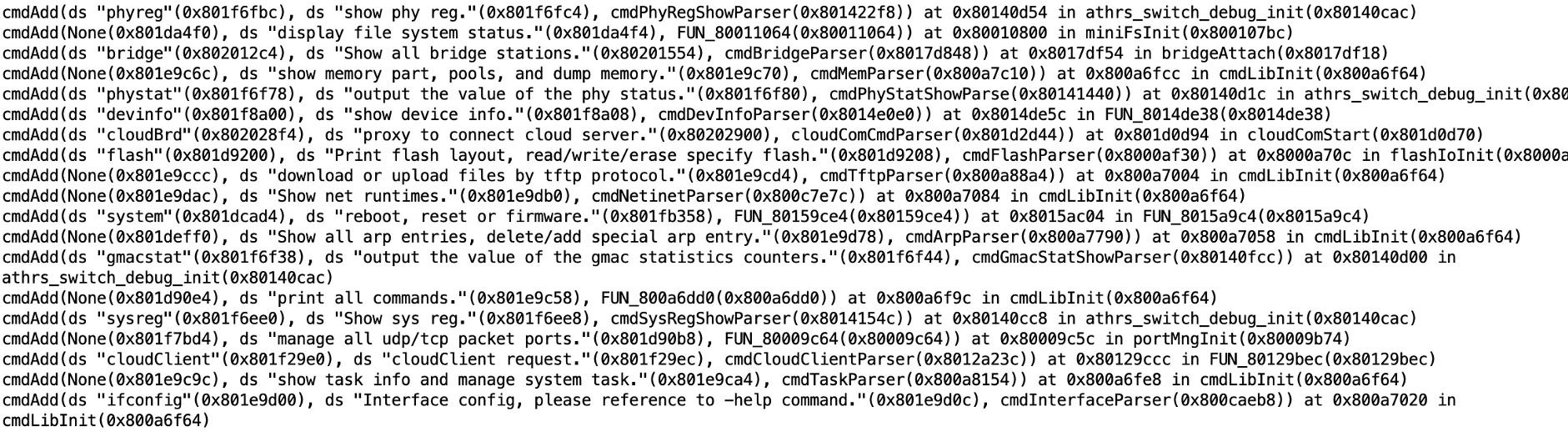
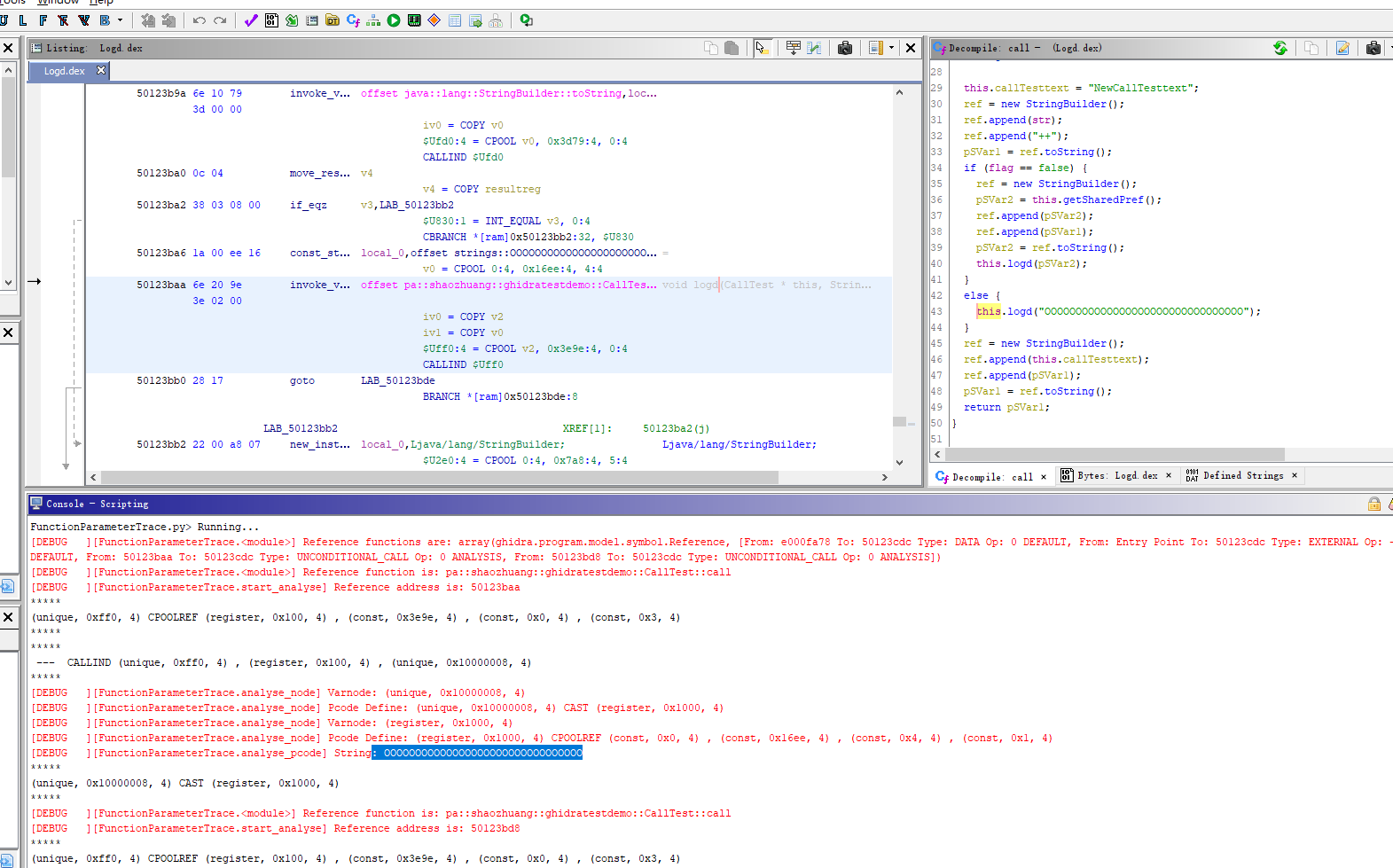
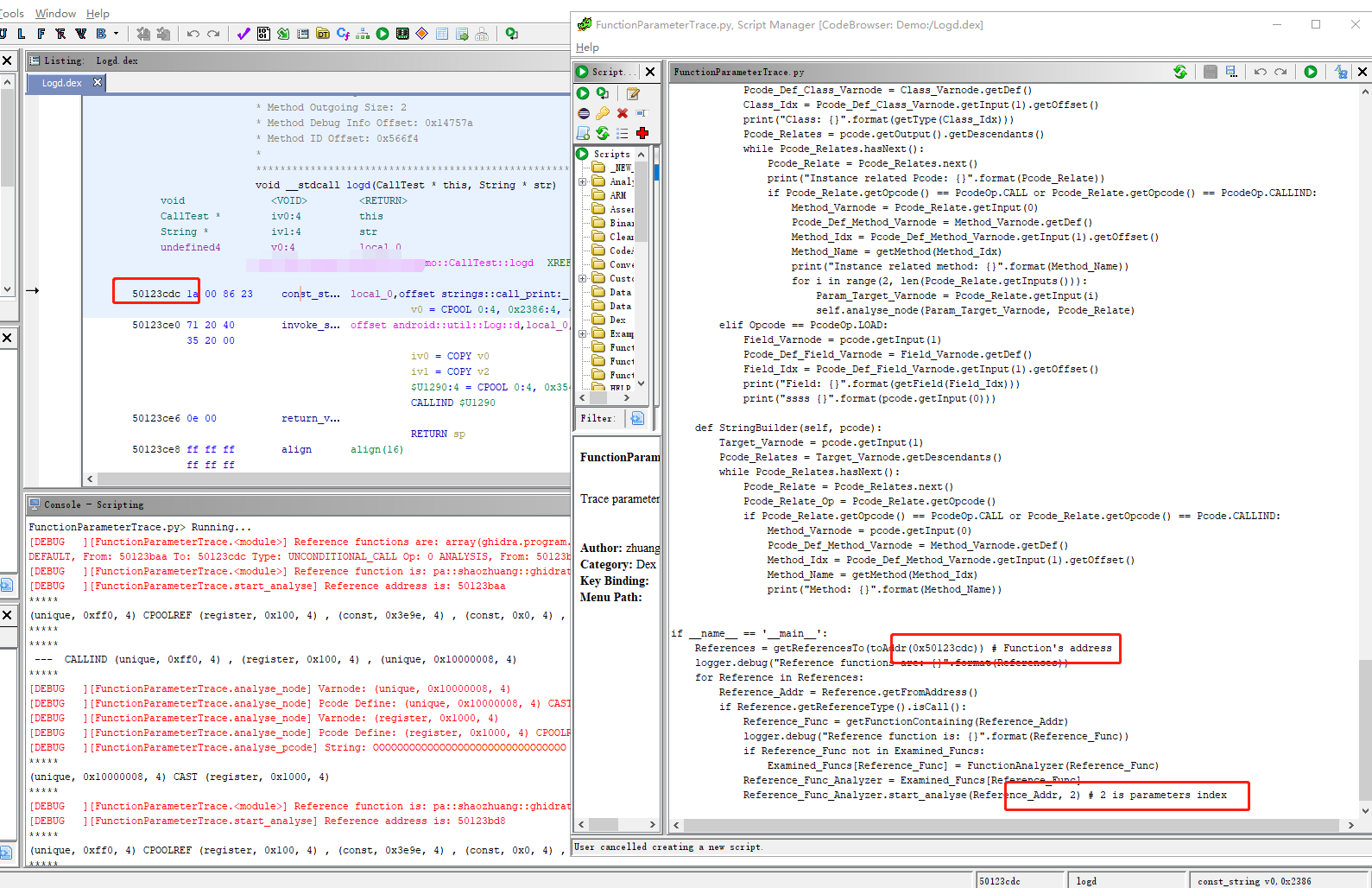
Trace Function call parameters value using Ghidra P-Code.
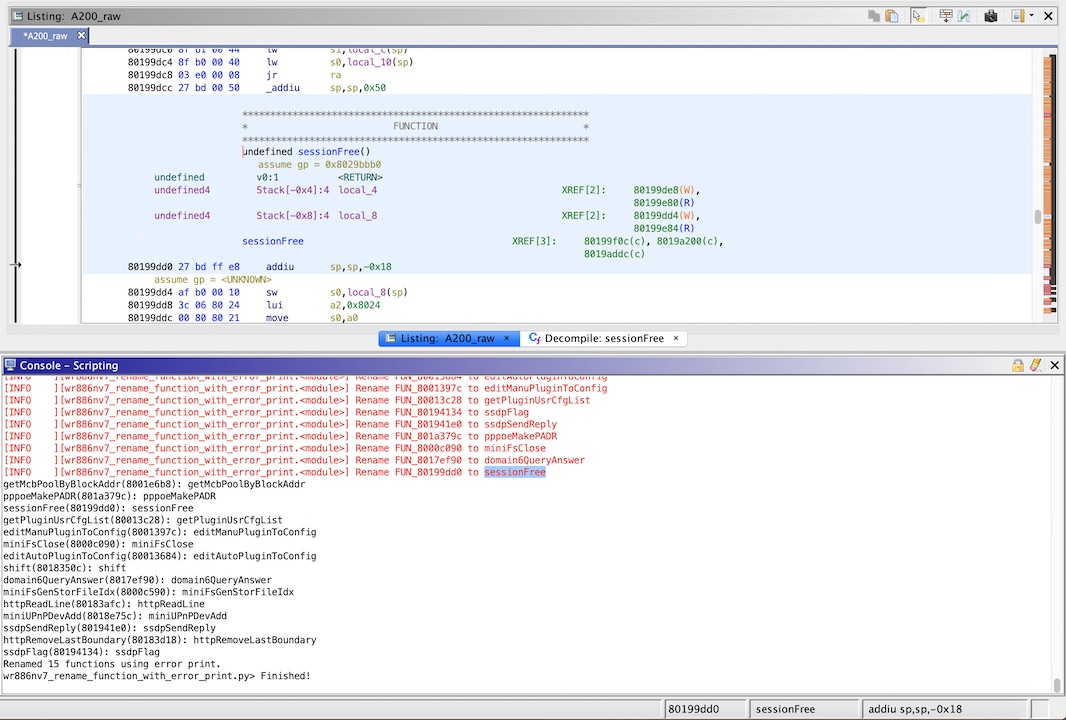
Example script, rename undefined function with error print string.
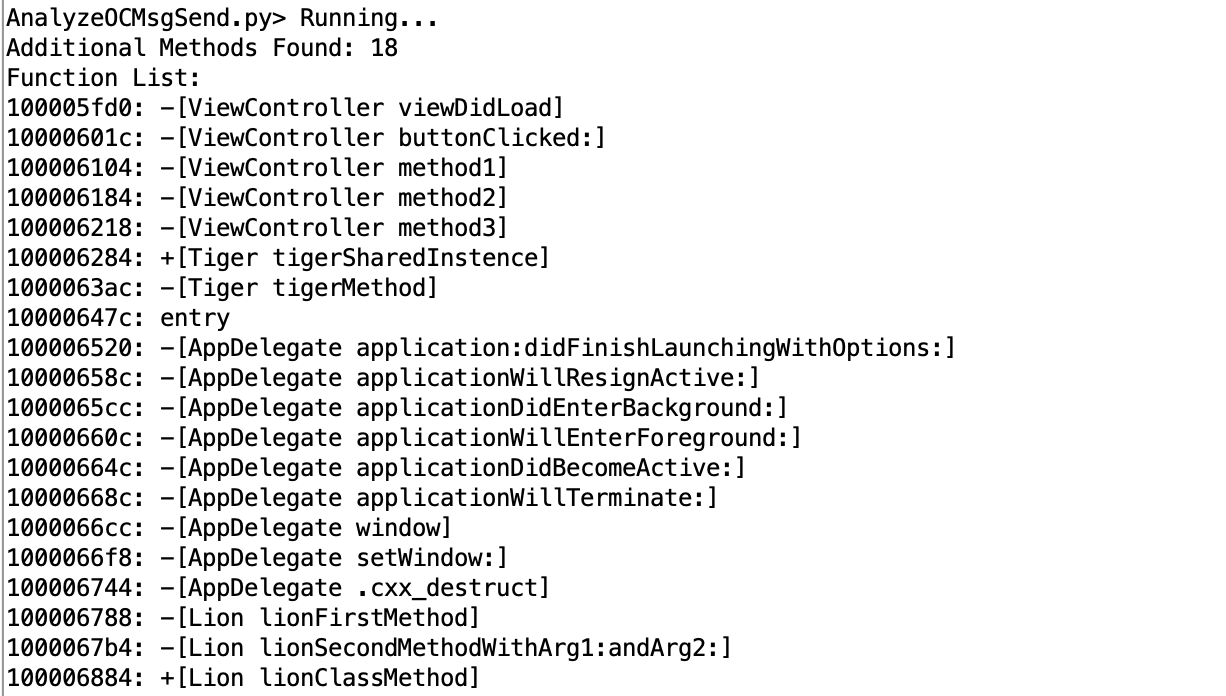
Analyze Objective-C MsgSend using this script.
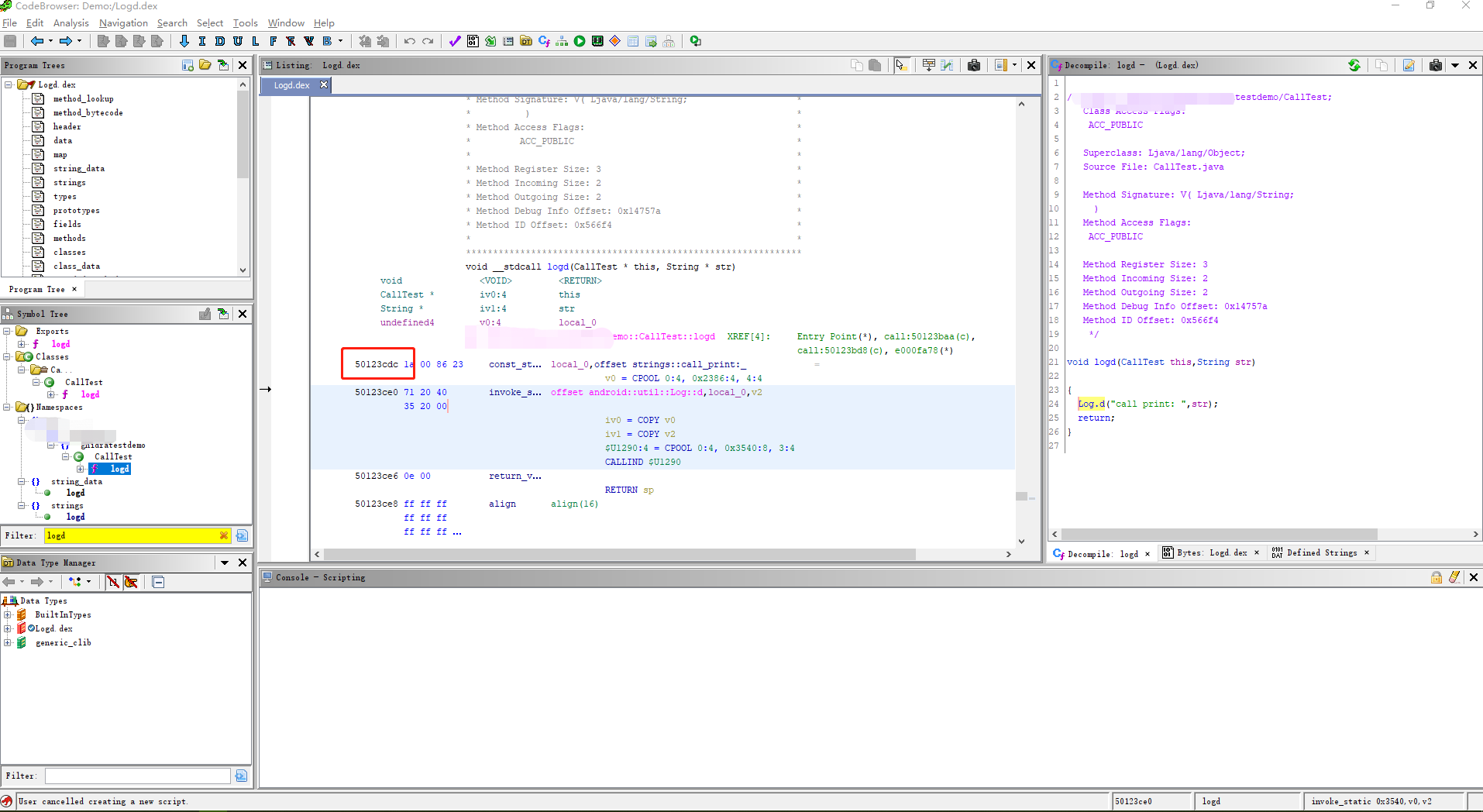
Trace an Android Function parameters value using Ghidra P-Code.
Provide target function's address and parameters index
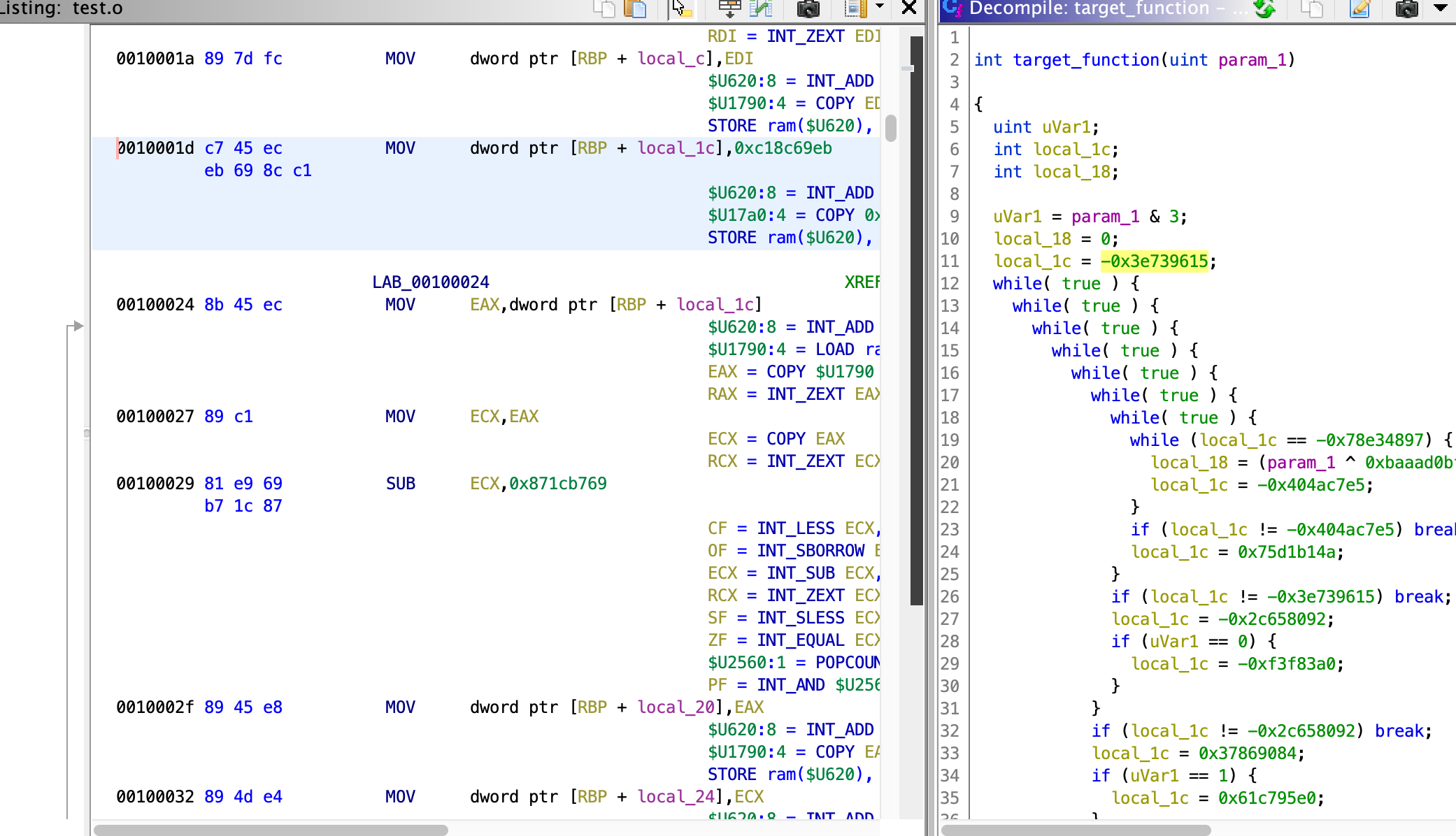
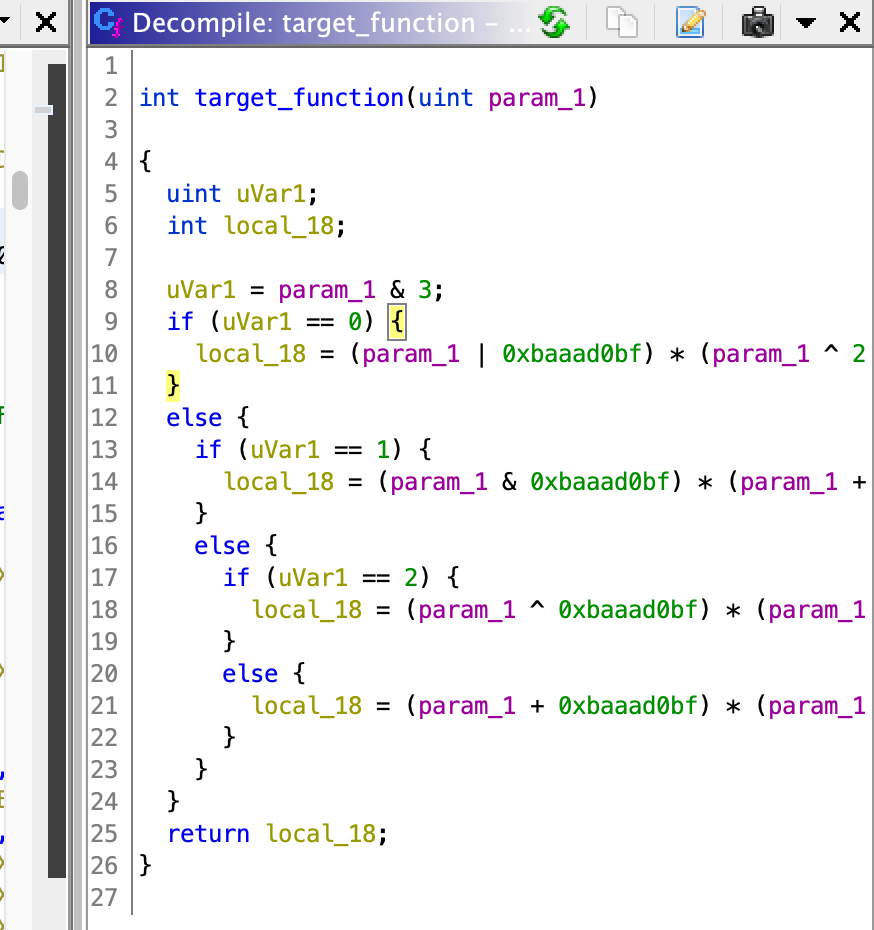
Deobfuscating OLLVM control flow flattening.
Select the assembly for state var initialization in Ghidra code listing interface.
Then run the script for deobfuscation.