My take on a Web Inventory tool, heavily inspired by Eyewitness. Takes screenshots of webpages using Pyppeteer (headless Chrome/Chromium).
Supports Python >= 3.7, uses Asyncio and has some extra bells & whistles that makes life easier.
- Python >= 3.7
- No dependency/installation hell, works on a variety of *nix flavors
- Asyncio provides Mad Max level speeds
- Headless chrome/chromium is just straight up gangsta
git clone https://github.com/byt3bl33d3r/WitnessMe && cd WitnessMe
pip3 install --user pipenv && pipenv install --three
pipenv shell # Enter the virtualenvwitnessme.py is what takes the screenshots, wmdb.py allows you to browse the database created on each scan.
usage: witnessme.py [-h] [-p PORTS [PORTS ...]] [--threads THREADS]
[--timeout TIMEOUT]
target [target ...]
positional arguments:
target The target IP(s), range(s), CIDR(s) or hostname(s)
optional arguments:
-h, --help show this help message and exit
-p PORTS [PORTS ...], --ports PORTS [PORTS ...]
Ports to scan if IP Range/CIDR is provided (default:
[80, 8080, 443, 8443])
--threads THREADS Number of concurrent threads (default: 25)
--timeout TIMEOUT Timeout for each connection attempt in seconds
(default: 35)
Can accept a mix of .Nessus file(s), Nmap XML file(s) and IP addresses/ranges/CIDRs as targets:
python witnessme.py 192.168.1.0/24 192.168.1.10-20 ~/my_nessus_scan.nessus ~/my_nmap_scan.xmlNote: as of writing, WitnessMe detects files by their extension so make sure Nessus files have a .nessus extension, NMap scans have a .xml extension etc..
If an IP address/range/CIDR is specified as a target, WitnessMe will attempt to screenshot HTTP & HTTPS pages on ports 80, 8080, 443, 8443 by default. This is customizable with the --port argument.
Once a scan is completed, a folder with all the screenshots and a database will be in the current directory, point wmdb.py to the database in order to see the results.
python wmdb.py scan_2019_11_05_021237/witnessme.dbPressing tab will show you the available commands and a help menu:
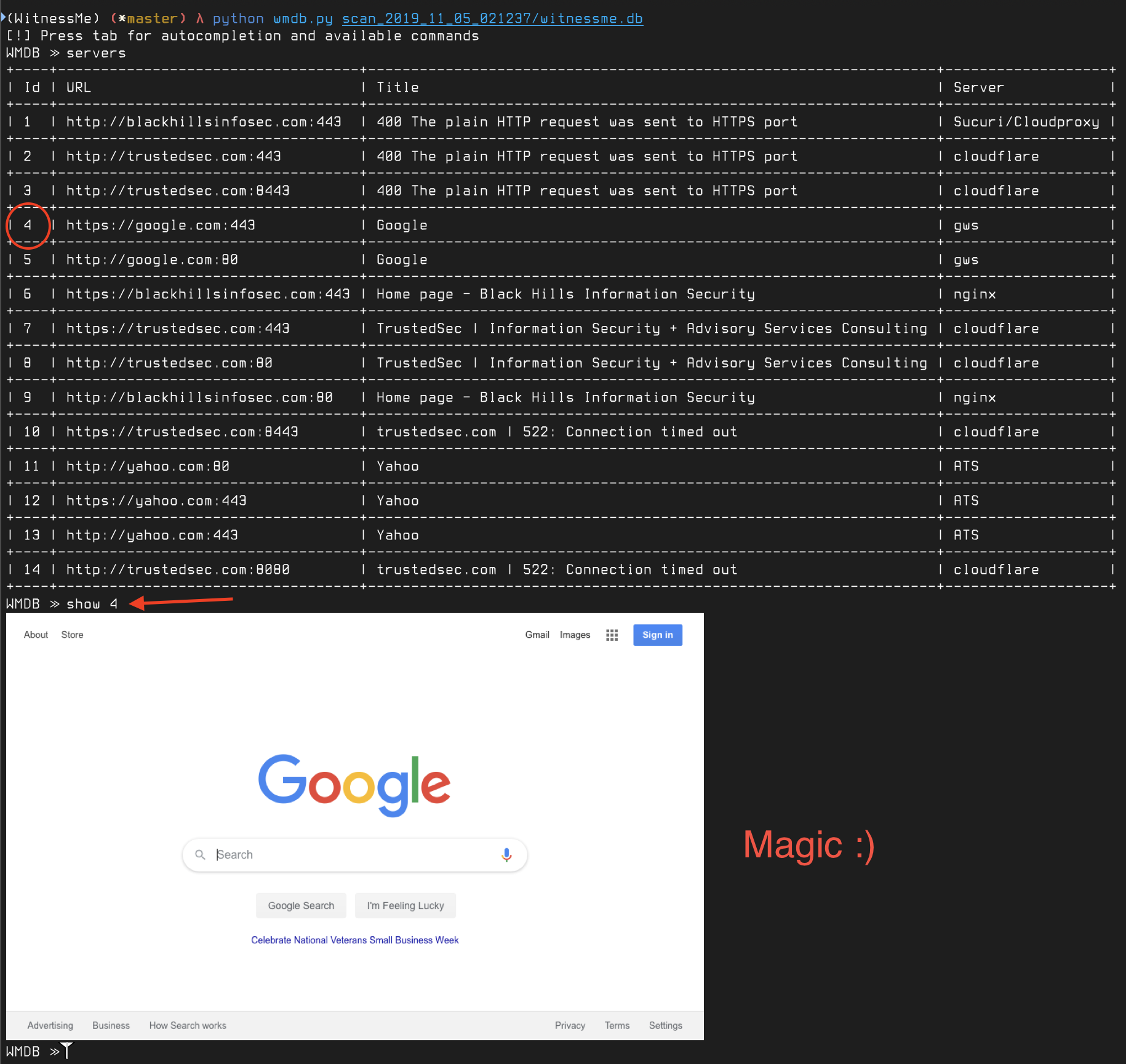
If you're using ITerm2 on MacOSX, you can preview screenshots directly in the terminal using the show command:
Store server info to a database- HTML report generation
Cmdline script to search database- Support NMap & .nessus files as input (Almost there, still some bugs but usable)
- Web server categorization & signature support
- Accept URLs as targets (cmdline, files, stdin) (Accepts files)