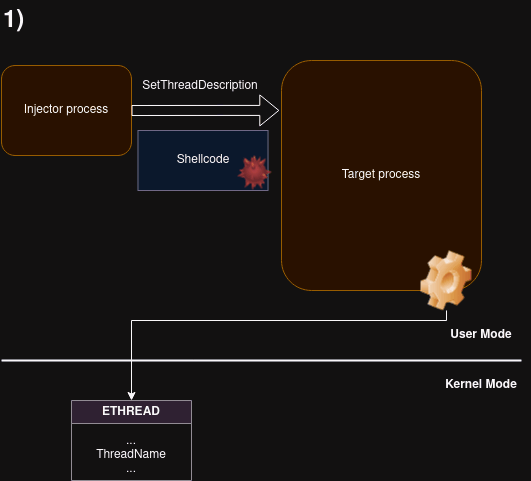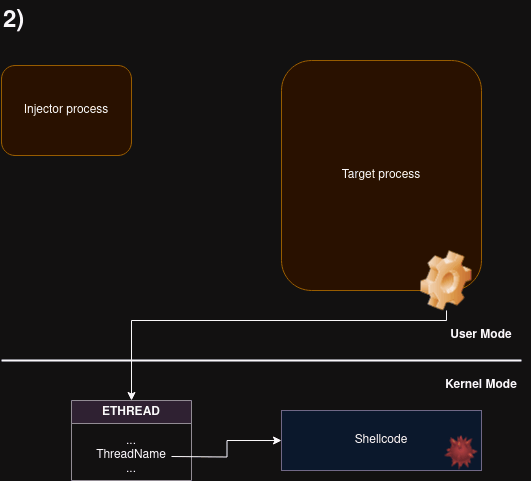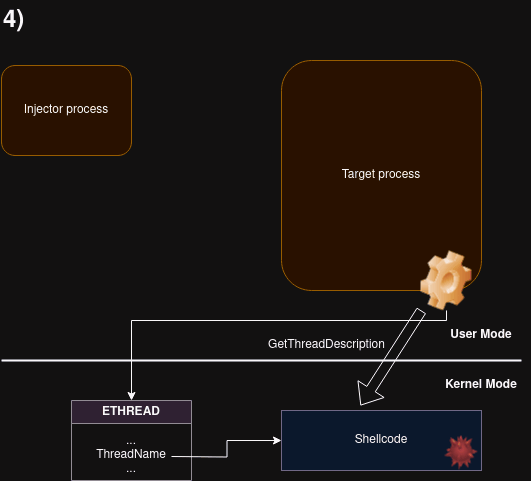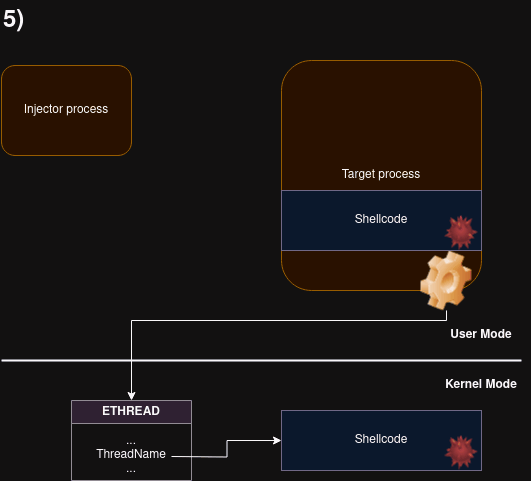
Remote shellcode injection technique, using Thread Name (a.k.a. Thread Description)
The code to be injected is passed as a thread description to the target (with SetThreadDescription). Then, a function GetThreadDescription is called remotely on the target, via APC, causing the description buffer to be copied into the target’s working set. After making the buffer executable, it is run using another APC call.
Details: https://research.checkpoint.com/2024/thread-name-calling-using-thread-name-for-offense/
The buffer is injected into the remote process without the need of having the write privilege (PROCESS_VM_WRITE).
thread_namecaller- implementation of Thread Name-Calling injection. Injects a shellcode that pops a calc into a process selected by the PIDdll_inj- a DLL injection variant. The path to the DLL is written into the remote process via Thread Namethread_receive- a demo target application, with a set of various mitigation policies
thread_namecaller in action:
dll_inj in action: