Zircolite is a standalone tool written in Python 3. It allows to use SIGMA rules on : MS Windows EVTX (EVTX, XML and JSONL format), Auditd logs, Sysmon for Linux, EVTXtract, CSV and XML logs
- Zircolite is relatively fast and can parse large datasets in just seconds
- Zircolite is based on a Sigma backend (SQLite) and do not use internal sigma to "something" conversion
- Zircolite can export results to multiple format with using Jinja templates : JSON, CSV, JSONL, Splunk, Elastic, Zinc, Timesketch...
Zircolite can be used directly in Python or you can use the binaries provided in releases.
Documentation is here (dedicated site) or here (repo directory).
Python 3.8 minimum is required. If you only want to use base functionnalities of Zircolite, you can install dependencies with : pip3 install -r requirements.txt. But pip3 install -r requirements.full.txt is strongly recommanded.
The use of evtx_dump is optional but required by default (because it is -for now- much faster), If you do not want to use it you have to use the --noexternal option. The tool is provided if you clone the Zircolite repository (the official repository is here).
evtx library may need Rust and Cargo to be installed.
Check tutorials made by other (EN, SP and FR) here.
Help is available with zircolite.py -h. If your EVTX files have the extension ".evtx" :
# python3 zircolite.py --evtx <EVTX FOLDER or EVTX FILE> --ruleset <SIGMA RULESET> [--ruleset <OTHER RULESET>]
python3 zircolite.py --evtx sysmon.evtx --ruleset rules/rules_windows_sysmon_pysigma.jsonThe SYSMON ruleset employed is a default one, intended for analyzing logs from endpoints with SYSMON installed.
python3 zircolite.py --events auditd.log --ruleset rules/rules_linux.json --auditd
python3 zircolite.py --events sysmon.log --ruleset rules/rules_linux.json --sysmon4linux
python3 zircolite.py --events <JSON_FOLDER or JSON_FILE> --ruleset rules/rules_windows_sysmon_pysigma.json --jsononlyℹ️ If you want to try the tool you can test with EVTX-ATTACK-SAMPLES (EVTX Files).
# Pull docker image
docker pull wagga40/zircolite:latest
# If your logs and rules are in a specific directory
docker run --rm --tty \
-v $PWD:/case/input:ro \
-v $PWD:/case/output \
wagga40/zircolite:latest \
-e /case/input \
-o /case/output/detected_events.json \
-r /case/input/a_sigma_rule.ymlYou can replace $PWD with the directory (absolute path only) where your logs and rules/rulesets are stored.
python3 zircolite.py -Uℹ️ Please note these rulesets are provided to use Zircolite out-of-the-box but you should generate your own rulesets but they can be very noisy or slow. These auto-updated rulesets are available on the dedicated repository : Zircolite-Rules.
Everything is here.
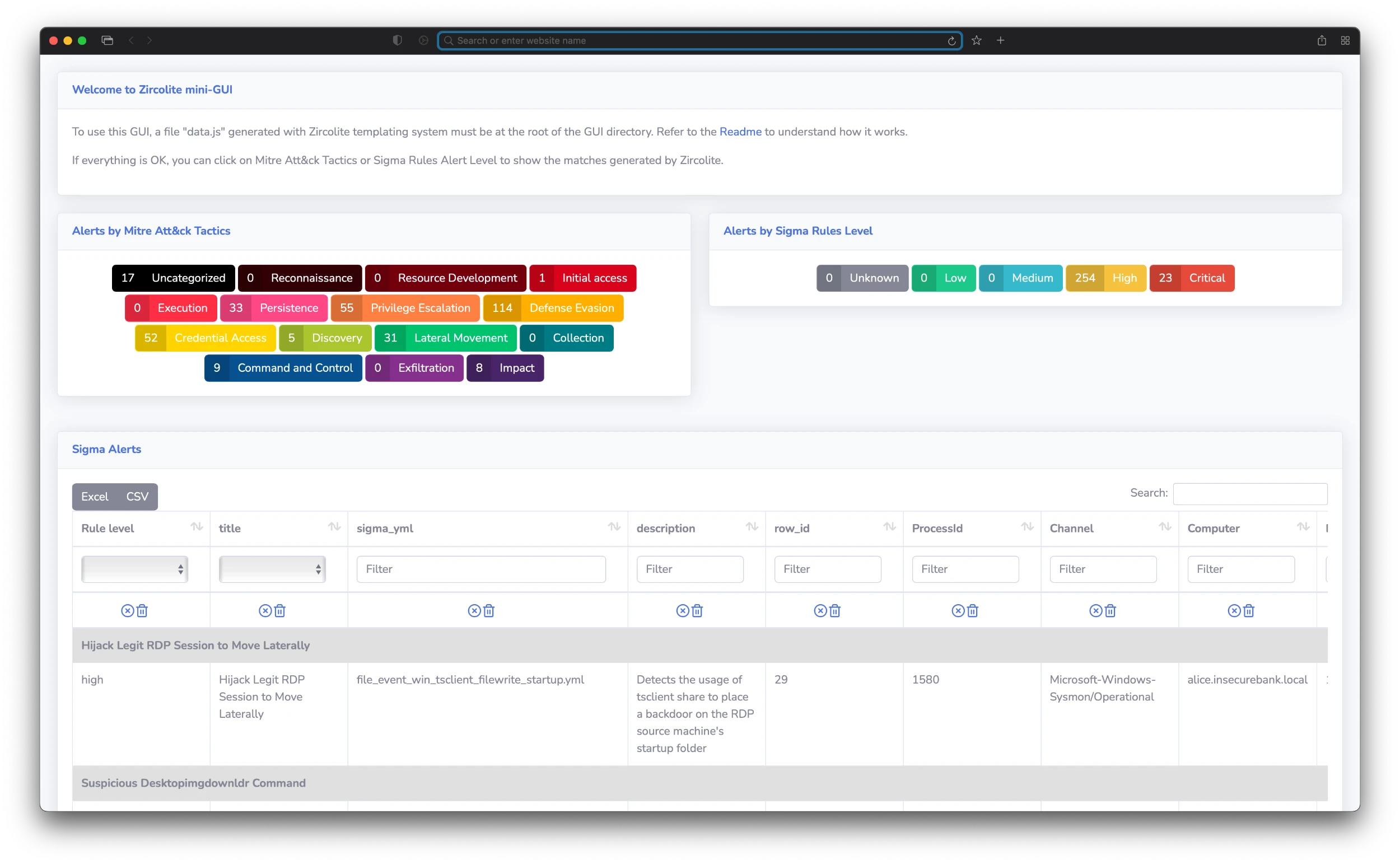
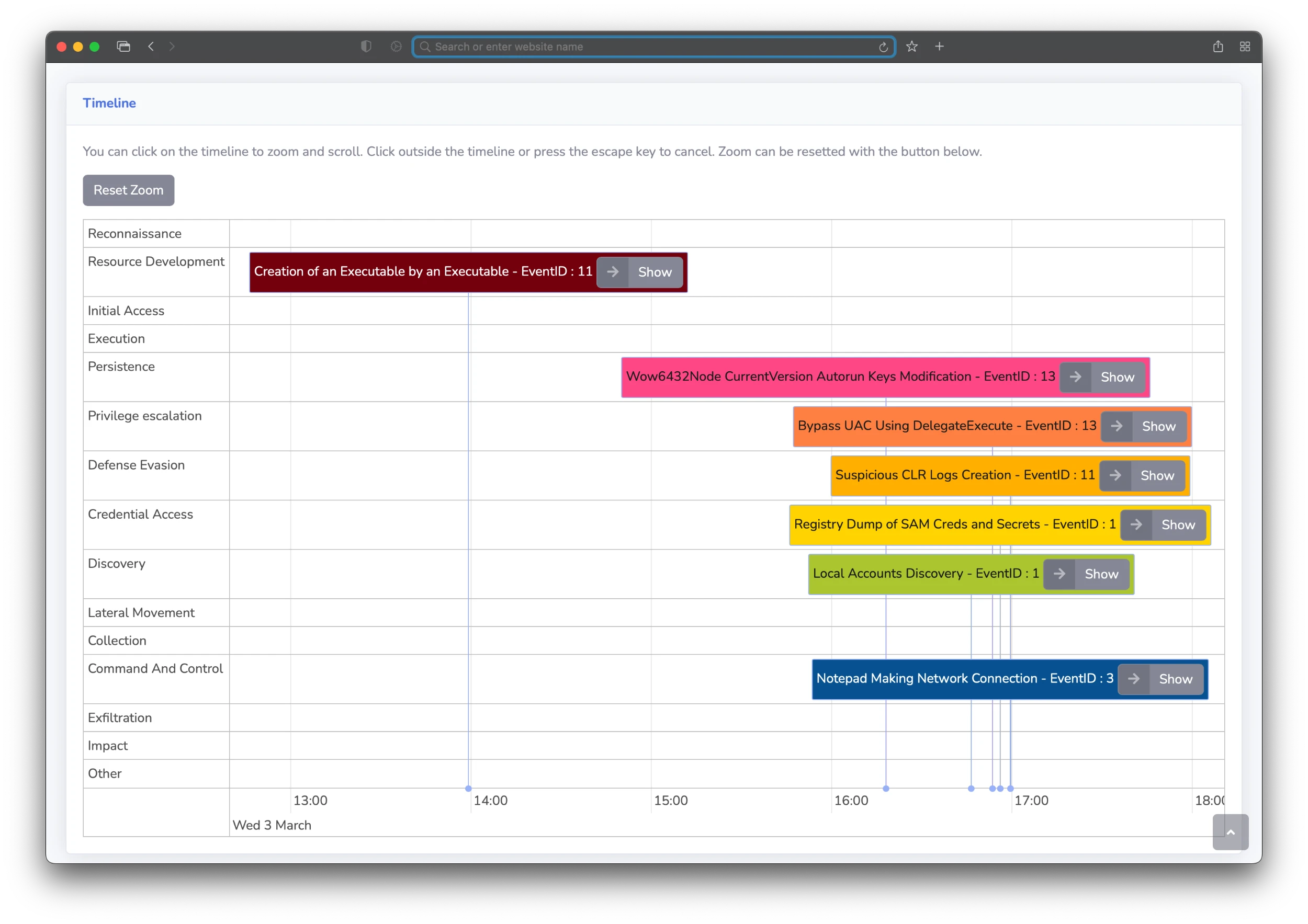
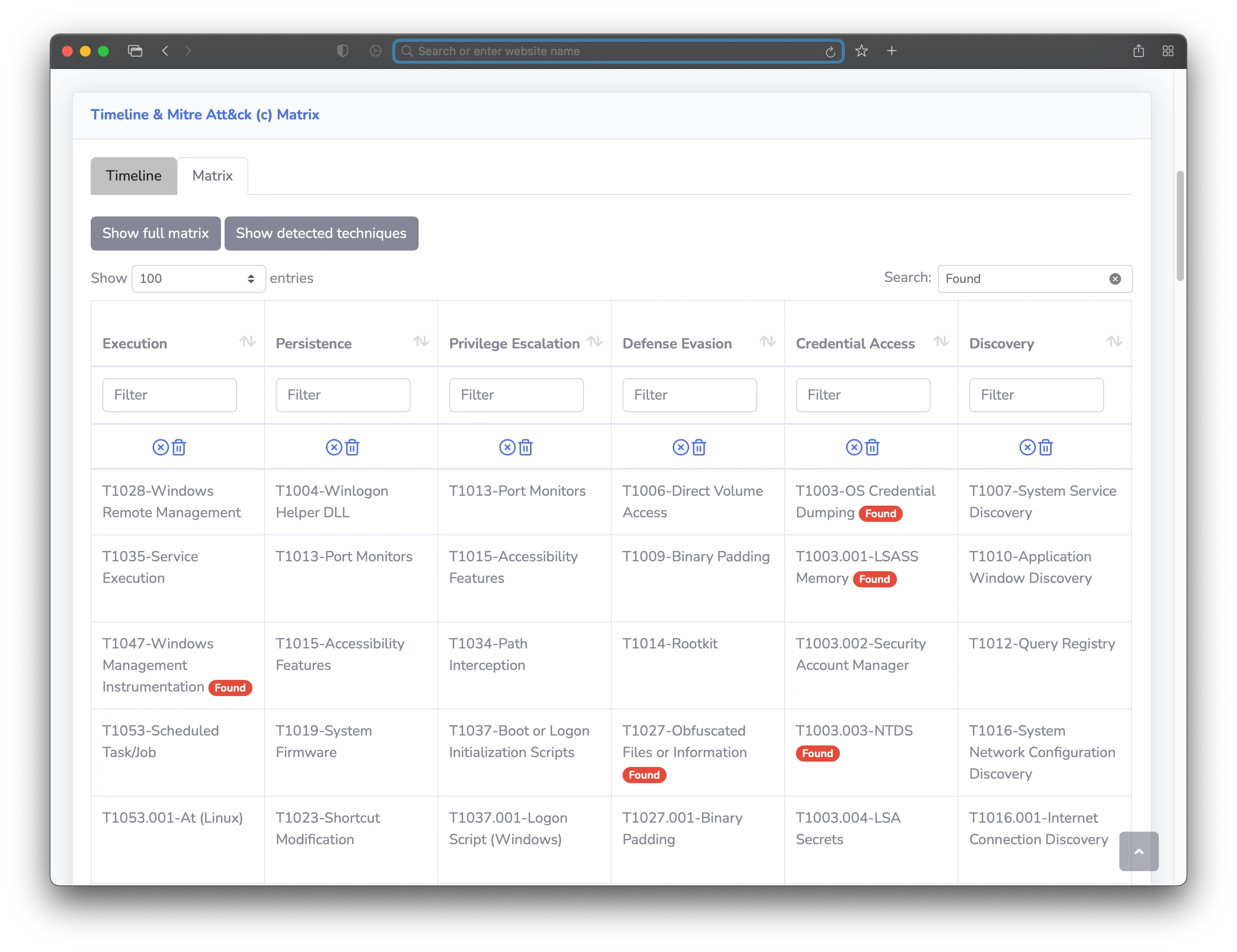
The Mini-GUI can be used totally offline, it allows the user to display and search results. You can automatically generate a Mini-Gui "package" with the --package option. To know how to use the Mini-GUI, check docs here.
-
(EN) Russ McRee has published a pretty good tutorial on SIGMA and Zircolite in his blog
-
(SP) César Marín has published a tutorial in spanish here
-
(FR) IT-connect.fr has published a very extensive tutorial in French on Zircolite
- Florian Roth cited Zircolite in his SIGMA Hall of fame in its talk dugin the October 2021 EU ATT&CK Workshop in October 2021
- Zircolite has been cited and used in the research work of the CIDRE team : PWNJUSTSU - Website and PWNJUSTSU - Academic paper
- Zircolite has been cited and presented during JSAC 2023
- All the code of the project is licensed under the GNU Lesser General Public License
evtx_dumpis under the MIT license- The rules are released under the Detection Rule License (DRL) 1.0