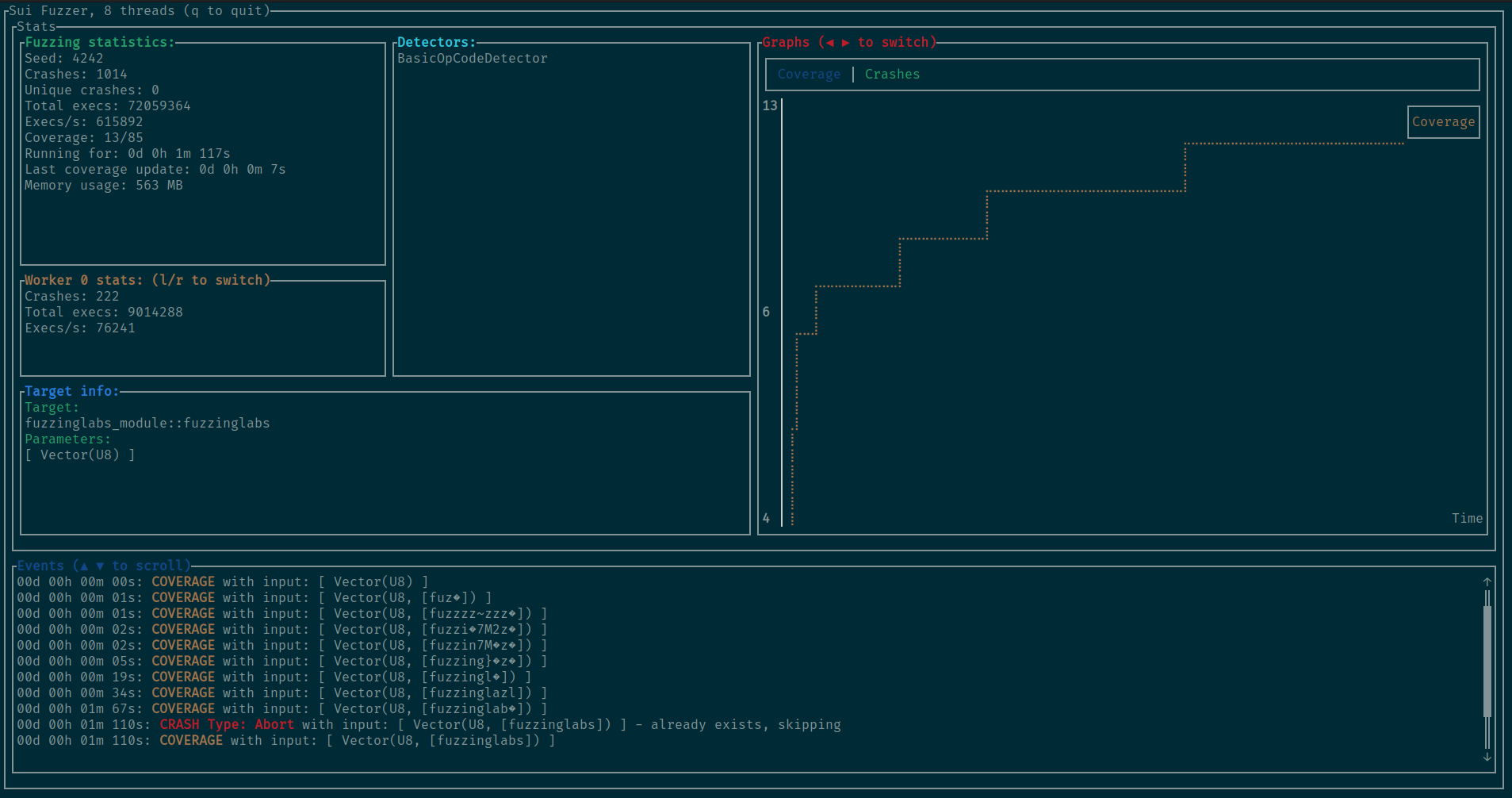
Fuzzer for Sui Move Smart Contracts.
- Testing and analysis of Sui Move and VM internals
- Development of the project base (architecture and command line interface)
- Tutorial for project installation and testing
- Identification of arguments and contracts execution requirements
- Creation MVP
- Improvement of the project (threading, runtimes perf monitoring)
- Implementation of coverage-guided fuzzing
- Implementation of vulnerability detectors
- Add support for property testing methods
- Docker and packaging of the fuzzer as a library
- Tutorial for running fuzzers and using advanced CLI options
- Generation of sequences of calls (stateful fuzzing)
- Improvement of contract argument generation (based on )
- Improvement of command line options
- Improvement of the fuzzing (input file sharing, mutation algorithm, speed)
- Create more documentation & tutorials against basic/example contracts
You need to clone the repository with the submodules using the following command:
$ git clone --recursive git@github.com:FuzzingLabs/sui-fuzzer.gitTo run the fuzzer just use (with rust and cargo installed):
$ make CONFIG_PATH="./config.json" TARGET_MODULE="fuzzinglabs_module" TARGET_FUNCTION="fuzzinglabs"You need to have a compiled SuiMove module path in the contract item in the config.
To run the fuzzer just use (with rust and cargo installed):
$ make CONFIG_PATH="./config.json" TARGET_MODULE="calculator_module" TARGET_FUNCTIONS="add,sub"You need to have a package path in the contract item in the config.
Here is an example of config:
{
"use_ui": true, // Do you want the nice UI or not ?
"nb_threads": 8, // The number of threads used by the fuzzer
"seed": 4242, // The inital seed
"contract": "./examples/fuzzinglabs_package/build/fuzzinglabs_package/bytecode_modules/fuzzinglabs_module.mv", // The path to the compiled module / package
"execs_before_cov_update": 10000, // When the coverage is shared between the threads (don't modify if you don't know why)
"corpus_dir": "./corpus", // Path to where the corpus are written
"crashes_dir": "./crashes", // Path to where the crashfiles are written
"fuzz_functions_prefix": "fuzz_", // Fuzzing functions prefix (can be listed by the fuzzer)
"max_call_sequence_size": 5 // Maximum size of a generated call sequence (only for stateful fuzzing)
}You can find more information on how to use the fuzzer in ./doc/how_to_use_stateless.md and in ./doc/how_to_use_stateful.md .
You can also use the provided docker_run.sh script to launch it in a container, use the same arguments for the script as for the Makefile (Documentation in ./doc/how_to_use_stateless.md and ./doc/how_to_use_stateful.md).
$ ./docker_run.sh CONFIG_PATH="./config.json" TARGET_MODULE="fuzzinglabs_module" TARGET_FUNCTION="fuzzinglabs"