A DNS reconnaissance tool.
dnsrato is a DNS reconnaissance tool that performs tasks such as:
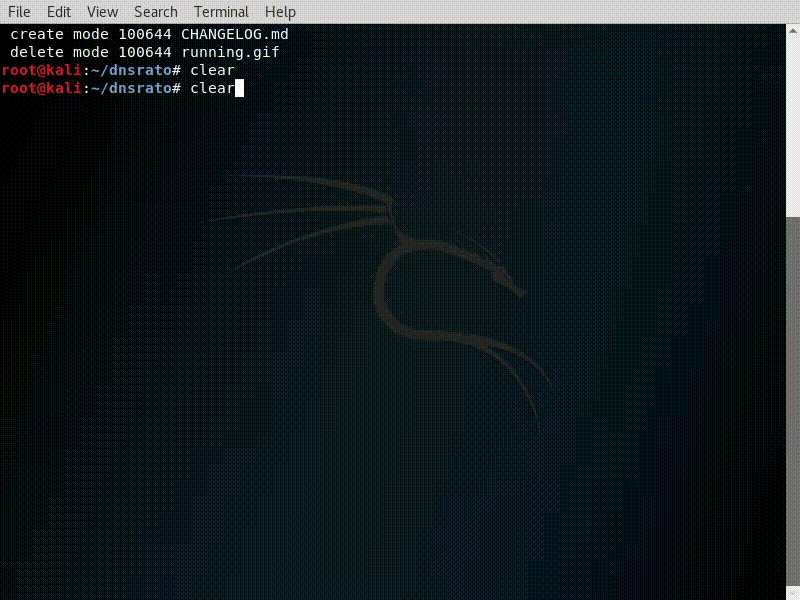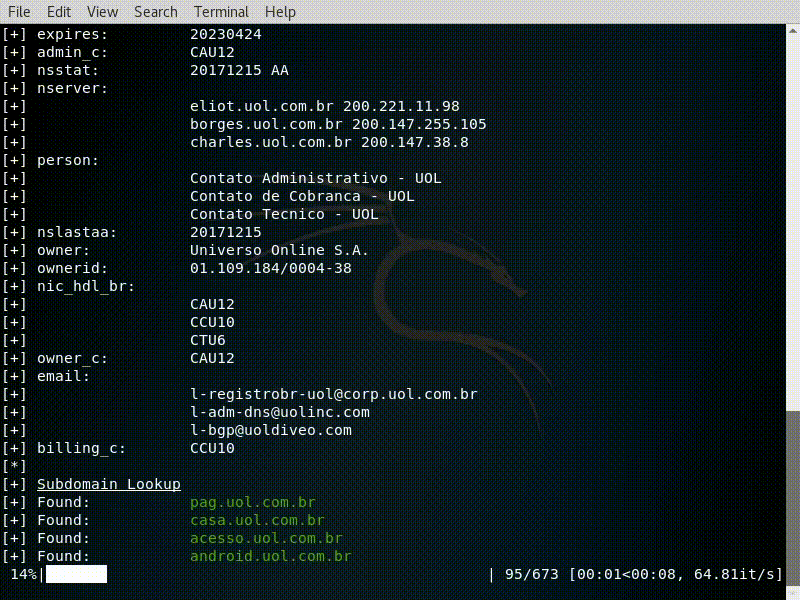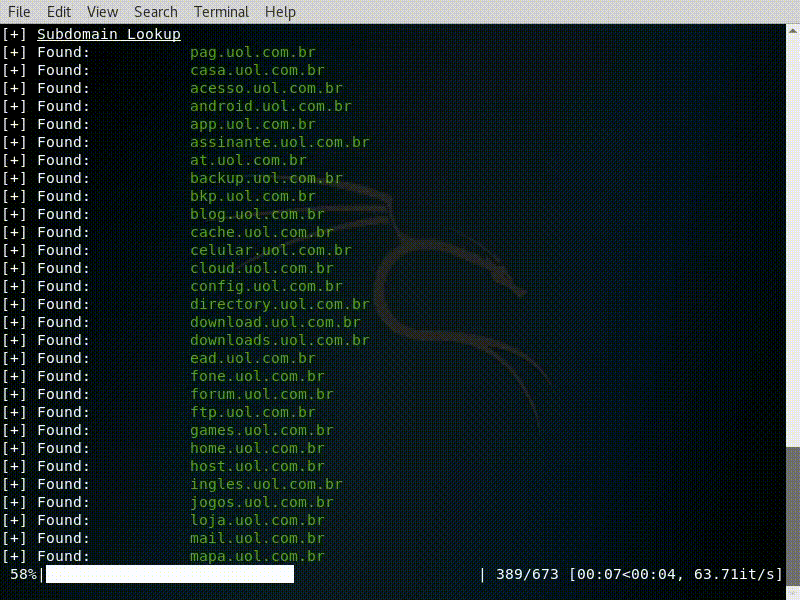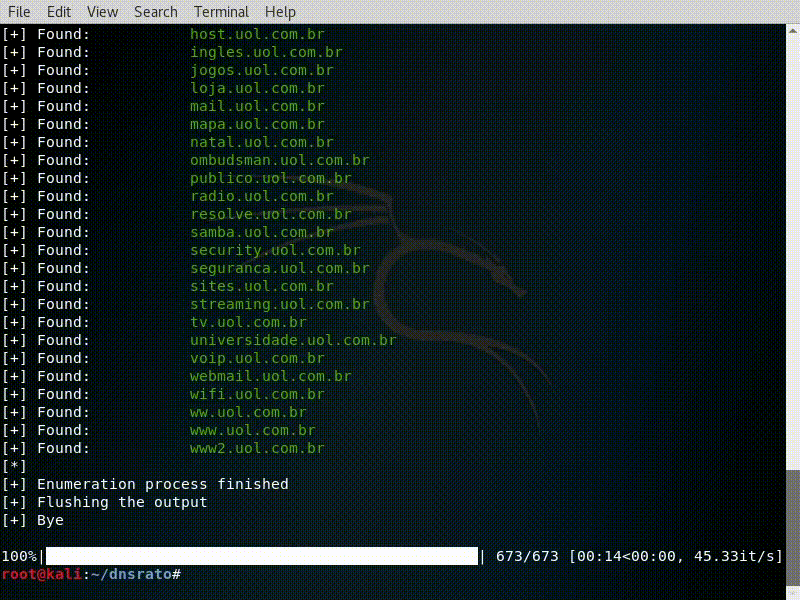
- Whois Lookup;
- Sub-domain enumeration(brute force) based on a word list file.
This is a Python version(with some extra features) of the first version written in C by Ricardo Longatto. The C version can be found at: https://github.com/ricardolongatto/dnsrato
git clone https://github.com/tommelo/dnsrato
cd dnsrato && sudo pip install -r requirements.txt| Short opt | Long opt | Default | Required | Description |
|---|---|---|---|---|
| -d | --domain | None | Yes | The domain url |
| -D | --dictionary | rato.txt | No | The dictionary file |
| -f | --format | txt | No | The output format(xml, json or text) |
| -h | --help | None | No | Shows the help usage |
| -o | --outuput | stdout | No | The output file |
| -p | --port | 80 | No | The host port |
| -s | --sleep | 0 | No | The thread sleep time(seconds) |
| -w | --workers | 10 | No | The number of thread workers |
| -t | --timeout | 4 | No | The request timeout |
| -v | --verbose | False | No | Enables the verbose mode |
| N/A | --proxy | False | No | Use proxy |
| N/A | --proxy-host | 127.0.0.1 | No | Proxy host IP |
| N/A | --proxy-port | 9150 | No | Proxy host PORT |
| N/A | --ssl | False | No | Enables SSL |
| N/A | --version | None | No | Shows the current version |
The domain url. The following urls are considered valid:
http://domain.com
http://www.domain.com
http://subdomain.domain.com
Running the script with the domain argument:
python dnsrato.py -d domain.comA dictionary file can be used to perform the subdomain brute force recon. The file must contain a list of words with the following format:
subdomainone.
subdomaintwo.
Running the script with the dictionary argument:
python dnsrato.py -d domain.com -D /path/to/file.txtThe enumeration result can be sent to the output with the follwing formats:
- text
- json
- xml
Running the script with the output format argument:
python dnsrato.py -d domain.com -f json > enumeration.jsonThe text format will produce the follwing result:
Domain: domain.com
Whois Lookup
key: value
...
Subdomain Lookup
subdomainone.domain.com
subdomaintwo.domain.com
...
The json format will produce the follwing result:
{
"domain": "domain.com",
"whois": {
"key": "value"
}
"subdomains": [
"subdomainone.domain.com"
"subdomaintwo.domain.com"
]
}
The xml format will produce the follwing result:
<?xml version="1.0" ?>
<dns>
<domain>domain.com</domain>
<whois>
<key>value</key>
<key>
<item>value1</item>
<item>value2</item>
</key>
</whois>
<subdomains>
<item>subdomainone.domain.com</item>
<item>subdomaintwo.domain.com</item>
</subdomains>
</dns>
The enumeration result can be saved to a file. The default output is the standard output(sys.stdout).
Running the script with the output file argument:
python dnsrato.py -d domain.com -f xml -o enumeration.xmlThe host port to connect. The default port is 80.
Running the script with the port argument:
python dnsrato.py -d domain.com -p 8080The thread sleep(in seconds). If you don't want to slam the server with too many concurrent requests you may consider using the sleep argument.
Running the script with the sleep argument:
python dnsrato.py -d domain.com -s 10The number of thread workers. The default number of workers is 10.
Running the script with the workers argument:
python dnsrato.py -d domain.com -w 20The request timeout(in seconds). If you running the script using a proxy you may consider using the timeout argument to increase the request timeout.
Running the script with the timeout argument:
python dnsrato.py -d domain.com -t 10The verbose. You may consider using the verbose mode to check the working status of the application.
Running the script with the verbose argument:
python dnsrato.py -d domain.com -vEnables the proxy mode.
Running the script with the proxy argument:
python dnsrato.py -d domain.com --proxy --proxy-host 127.0.0.1 --proxy-port 8080The proxy host. The default proxy host is 127.0.0.1.
Running the script with the proxy host argument:
python dnsrato.py -d domain.com --proxy --proxy-host 127.0.0.1 --proxy-port 8080The proxy port. The default proxy port is 9150.
Running the script with the proxy port argument:
python dnsrato.py -d domain.com --proxy --proxy-host 127.0.0.1 --proxy-port 8080Enables the SSL mode.
Running the script with the ssl argument:
python dnsrato.py -d domain.com --ssl -p 443Shows the current version of the application.
Running the script with the version argument:
python dnsrato.py --versionShows the help usage.
Running the script with the help argument:
python dnsrato.py -hCurrently, only the domain url is accepted as piped input:
echo domain.com | python dnsrato.pyThe enumeration result can also be piped:
python dnsrato.py -d domain.com | cat
python dnsrato.py -d domain.com -f json > outfile.json
python dnsrato.py -d domain.com -f json | python -m json.tool
python dnsrato.py -d domain.com -f xml | xmllint --format -Note: A piped output disables the verbose mode.
This is an open-source software licensed under the MIT license.