Python3-Tools
This is a collection of tools InfoSec people may use.
- fibonnaci.py is a simple function that InfoSec people would not use. I just really like it is all
- CVE-2019-17240.py is a CVE script I expanded on to practice some python 3. Original template for this script is located HERE
# The below command will prompt you for the required values since no args are specified
python3 CVE-2019-17240.py
# The below command will not prompt for the values as all values are specified
python3 CVE-2019-17240.py '10.10.10.10' '/admin/login' 'admin' '/usr/share/wordlists/rockyou.txt'
python3 CVE-2019-17240.py 10.10.10.10 /admin/login admin /usr/share/wordlists/rockyou.txt- hex2num.py I hate doing hexadecimal math. This is a command I made to help me calculate the offset in a buffer overflow when I have a return address of 0x4c. Calculating 0x4c to decimal is shown in the command below
./hex2num.py
# RESULTS OF RUNNING ABOVE COMMAND
Enter a hexadecimal value to convert to decimal: 4c # Enter 4c not 0x4c
4c in Decimal = 76- hex2text.py This command is meant to easily calculate the text value of hexadecimal value to string. I found this useful when using msf-pattern_create to crash an application and discover the registries EIP value of the crash.
./hex2text.py
# RESULTS OF RUNNING ABOVE COMMAND
Enter the hexadecimal value you want to conver to text: 42306142
B0aB- porttest.py is used for testing whether a port is open on a remote machine.
- pwd_generator.py is for quickly generating a password consisting of random characters for situtaions you may want to generate a password without entering a password manager GUI.
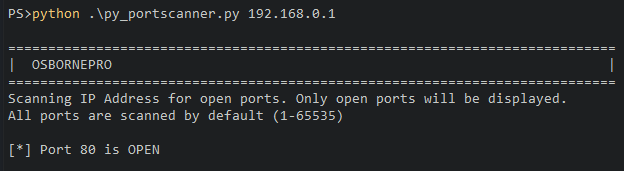
- py_portscanner.py I plan on making my baby as a great way for testing for open ports when python3 is available on a target
- porttest.py simple tool that was great for met in getting started in working with sockets. It can have values piped to it for scripting and it can be used with proxychains.
printf "10.1.1.27\n\r80\n\r" | proxychains python3 porttest.py
# OR
python3 porttest.py
IPv4 address of target: 10.1.1.27
Enter port number to test: 8000
Port 8000 is closedPython Reverse Shell Scripts
- py_reverse_shell_connect.py
- py_reverse_shell_listener.py
py_reverse_shell_listener.py opens a listening port you define. If no port is defined the default is 8089 as that is my favorite at the moment Below is how to execute the script.
python3 py_reverse_shell_listener.py
# Edit the contents of this file to change the listening portpy_reverse_shell_connect.py can be used to connect to a listening port. This does not neccessarily need to be used to connect to the above python listener however it does work.
python3 py_reverse_shell_connect.py
# Once this is executed you will be prompted for the listening ipv4 address and portAs can be seen from the image above, py_portscanner.py uses the following format. These examples scan all ports on the defined host.
python3 .\py_portscanner.py <ipv4 address>
python3 .\py_portscanner.py 192.168.0.1