BIG THANKS to Barney Buffet and j4imefoo for their awesome repositories that helps to create that. The creation of that, is a fusion of two repositories. Instead of making requests from the CLI, we have an API server to make queries against that. After, all the queries are proxied through the tor service.
- Docker Tor: A docker image that runs a Tor service on an Alpine linux base image
- nokyc: A script that lists all current Bisq, HodlHodl, Robosats and LNP2PBot offers in the terminal
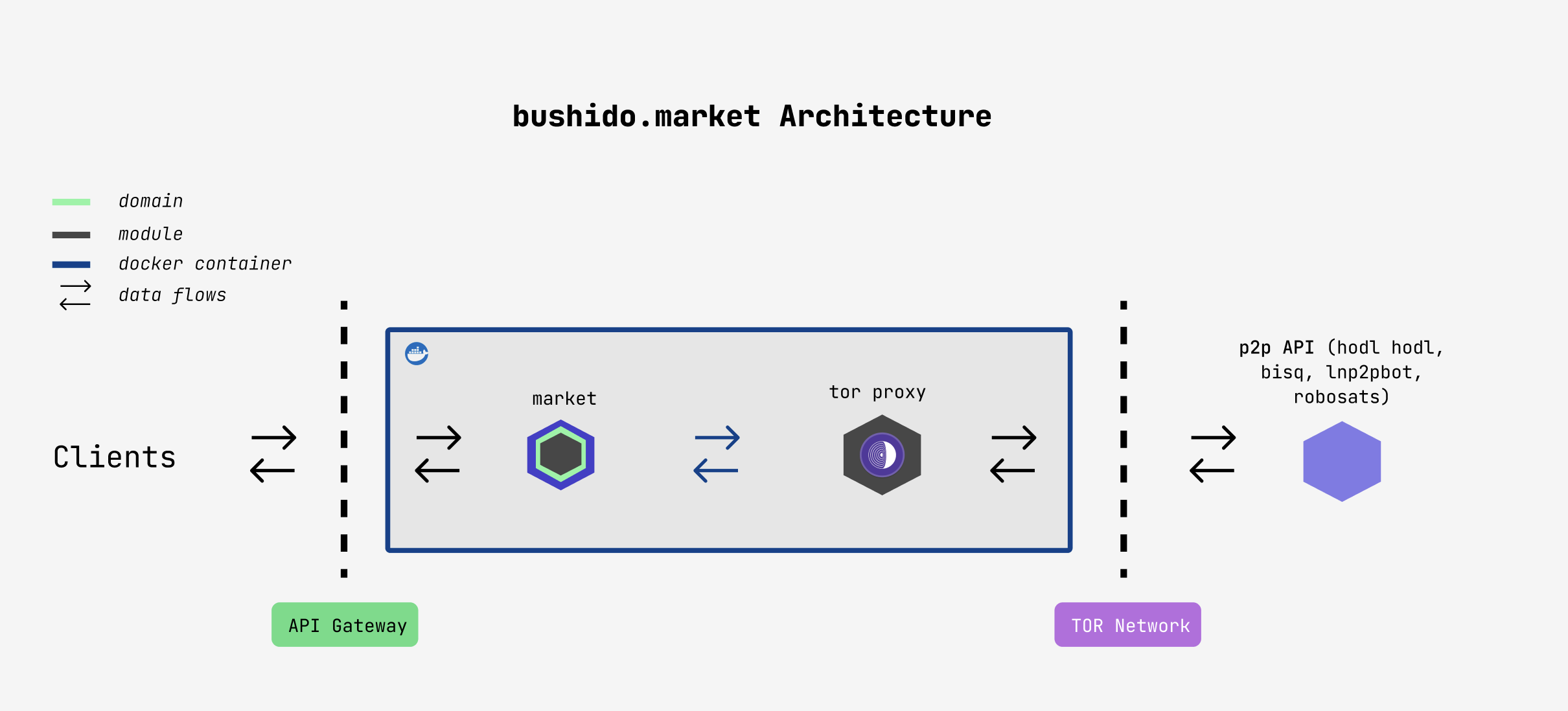
Clients interacts with the system through the API-Gateway. The market module executes the corresponding use-case and proxies the request through the proxy server. Usually, all the requests that travel through the tor network are going to different P2P exchanges (API) as Hodl Hold, Bisq, LNp2pbot and RoboSats to get the market offers. That two modules, work in top of a docker containers which gives the flexibility to be more portable and be able to install in a place that we want.
Create a docker network to set the communication between the containers. Even docker creates a default network in each docker-compose execution, in torrc file, we cannot use docker container name becase it breaks the naming pattern, it has to be an IP.
Allow to the app container to make request against the tor proxy container editing the default value of TOR_PROXY_ACCEPT. Docker proxy container does not expose its SOCKS port to outside, it is just accessible from inside of the docker network.
The below variables would be the default ones but we can add also the following Tor flags (next block). Once we add in the .env new variables, we have to add that flags as environments key in the docker-compose.yml file.
NETWORK_SUBNET=10.0.0.0/8
TOR_STATIC_IP=10.0.0.1
APP_STATIC_IP=10.0.0.2
TOR_PROXY_ACCEPT="accept 127.0.0.1,accept ${APP_STATIC_IP}"Below is a list of available environmental flags that can be set during container creation.
| Flag | Choices/Default | Comments |
|---|---|---|
| TOR_CONFIG_OVERWRITE | true/false | Create new torrc file each time we spin up the container |
| TOR_LOG_CONFIG | true/false | Should the tor config file torrc be echo'd to the log. This can be helpful when setting up a new Tor daemon |
| TOR_PROXY | true/false | Set up the Tor daemon as a Socks5 proxy |
| TOR_PROXY_PORT | string (9050) | What port the Tor daemon should listen to for proxy requests |
| TOR_PROXY_SOCKET | true/false | Create a unix socket for the proxy in the data folder |
| TOR_PROXY_ACCEPT | accept 127.0.0.1 | What IP addresses are allowed to route through the proxy |
| TOR_CONTROL | true/false | Should the Tor control be enabled |
| TOR_CONTROL_PORT | string | What port should the Tor daemon be controlled on. If enabled cookie authentication is also enabled by default |
| TOR_CONTROL_SOCKET | true/false | Create a unix socket for the Tor control |
| TOR_CONTROL_PASSWORD | string | Authentication password for using the Tor control port |
| TOR_CONTROL_COOKIE | true/false | Cookie to confirm when Tor control port request sent |
| TOR_SERVICE | true/false | Set up the Tor daemon with hidden services |
| TOR_SERVICE_HOSTS | hostname=wan-port:redict-ip:rediect-port | Tor hidden service configuration |
| TOR_SERVICE_HOSTS_CLIENTS | hostname:client-1,client-2,... | Authorised clients for hostname |
| TOR_RELAY | true/false | ** NOT IMPLEMENTED YET ** |
- When we change the configuration files delete the volume of tor
- Docker Tor docs
- Running Tor proxy with docker
- How to use Python with Tor and Privoxy
- torpool
- Asynchronous http request in python with aiohttp
- Speeding Up Python with Concurrency, Parallelism, and asyncio
- Configure Tor as a listening proxy server that I can connect to remotely?
- Cannot get tor proxy to work