Requirements:
- The azure account created
- The Service Principal set up
- Set the variables (used security variables to make the repo be cleaner) to be used across the commands (used in the github actions)
- For Azure CLI
- AZURE_CREDENTIALS
- For Terraform CLI
- For authentication
- AZURE_CLIENT_ID
- AZURE_CLIENT_SECRET
- AZURE_SUBSCRIPTION_ID
- AZURE_TENANT_ID
- For backend state
- RESOURCE_GROUP_NAME
- STORAGE_ACCOUNT_NAME
- STORAGE_CONTAINER_NAME
- For the remaining resources
- STORAGE_REGION_NAME (In my test, is brazilsouth)
- STORAGE_SKU_NAME
- For authentication
- For Azure CLI
az ad sp create-for-rbac --role="Contributor" --scopes="/subscriptions/{{AZURE_SUBSCRIPTION_ID}}" --name="Azure-DevOps-GithubActions" --sdk-auth
Output will be similar to that:
{
"clientId": "<clientId>",
"clientSecret": "<clientSecret>",
"subscriptionId": "<subscriptionId>",
"tenantId": "<tenantId>",
"activeDirectoryEndpointUrl": "https://login.microsoftonline.com",
"resourceManagerEndpointUrl": "https://management.azure.com/",
"activeDirectoryGraphResourceId": "https://graph.windows.net/",
"sqlManagementEndpointUrl": "https://management.core.windows.net:8443/",
"galleryEndpointUrl": "https://gallery.azure.com/",
"managementEndpointUrl": "https://management.core.windows.net/"
}
Important: Now copy/paste the output into the AZURE_CREDENTIALS variable and also for the clientId, clientSecret, subscriptionId, tenantId into AZURE_* variables, as they are used for terraform scripts. You will not be able to retrieve this data again after creation. The possibility to check this output again is resetting it.
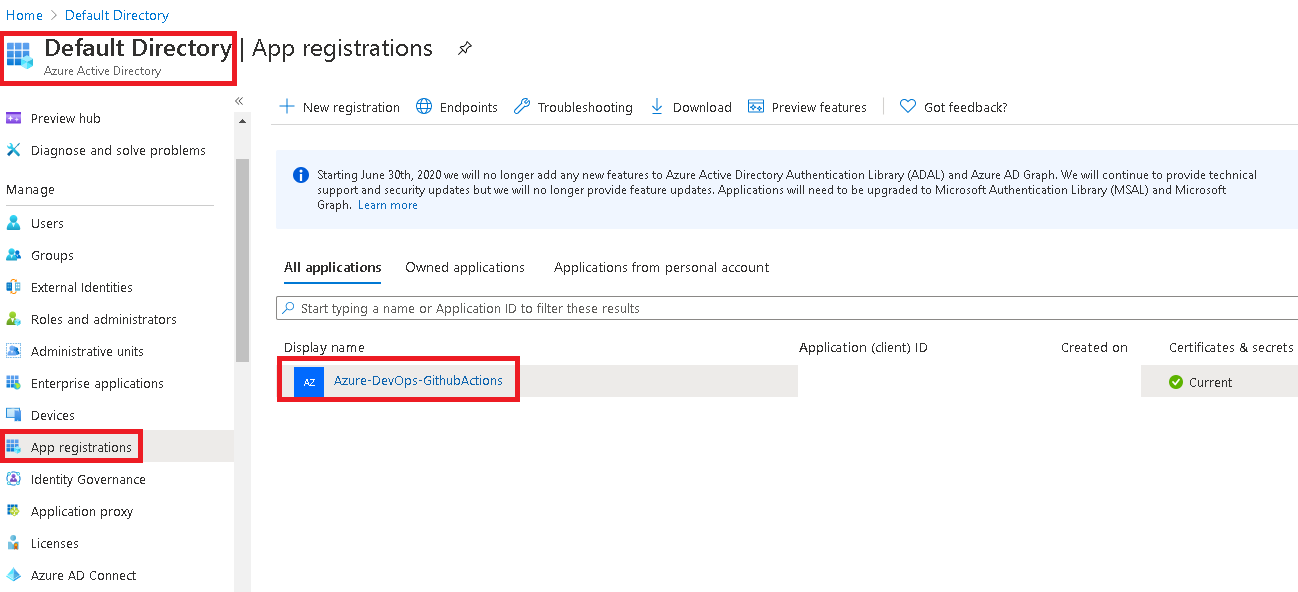
You should be able to see the Service Principal User present in the AD, as showed below:
az group create -g {{RESOURCE_GROUP_NAME}} -l {{STORAGE_REGION_NAME}}
az storage account create -n {{STORAGE_ACCOUNT_NAME}} -g {{RESOURCE_GROUP_NAME}} -l {{STORAGE_REGION_NAME}} --sku {{STORAGE_SKU_NAME}}
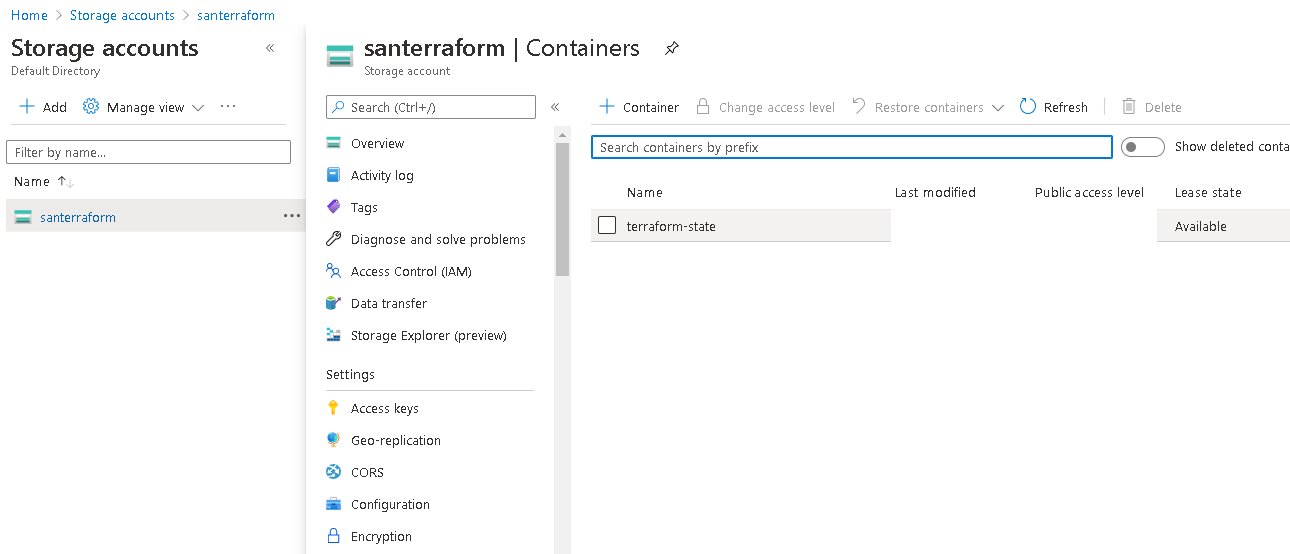
az storage container create -n {{STORAGE_CONTAINER_NAME}} --account-name {{STORAGE_ACCOUNT_NAME}}
Using Github actions, it was created the following YML files:
- az-create-terraform-state.yml
- az-destroy-terraform-state.yml
- It will destroy all the resources related to state, including the resource group
- az-terraform-resource-create-test.yml
- az-terraform-resource-destroy-test.yml
- A test using the backend state file destroying a resource
What is not covered:
- RBAC Azure command, why ?
- Because the output of this command is mandatory to have in the AZURE_CREDENTIALS file that is used across another commands to be able to login as Service Principal.
Microsoft
- Github Actions
- CLI
- Storage
- Resource Group
- AD Service Principal
- Generic
- Services available per region -> https://azure.microsoft.com/en-us/global-infrastructure/services/?regions=brazil-south,brazil-southeast&products=all
Github
- Using Github Actions -> https://docs.github.com/en/free-pro-team@latest/actions
- Encrypting the variables into secrets -> https://docs.github.com/en/free-pro-team@latest/actions/reference/encrypted-secrets
Terraform
- Provider
- Backend -> https://www.terraform.io/docs/backends/types/azurerm.html
- With Github Actions
Externals