nix develop
cp ./nix/manual-repo/minio/exploit.py .
python gen_nix -e exploit.py -o ../minio
# Assumes you are on nixos
sudo nixos-container create minio --flake .#minio
sudo nixos-container start minio
sudo nixos-container show-ip minio
python exploit.py -u "http://<ip>:9000/" -s "minioadmin" -a "minioadmin"
The outdir is set to ../minio because if a dir is in a subdirectory of a git repo - flakes won't search the file if the dir is not added to git.
- Install Nix:
- https://nixos.org/download#nix-install-windows - on windows
- https://nixos.org/download#nix-install-macos - on macos
- Enable Flakes:
echo "experimental-features = nix-command flakes" > ~/.config/nix/nix.conf- restart shell prob
- Getting the shell environment:
nix develop
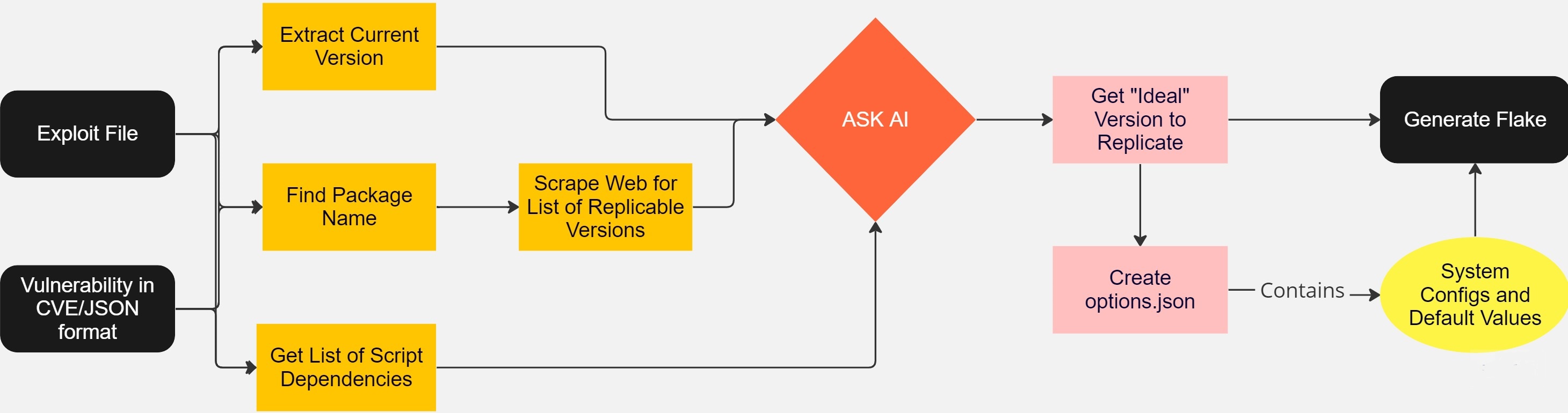
- Essentially - what we need to do is to either use an existing NLP model or a pretrained model to take a CVE and output the software versions of what is needed.
- This seems like pretty much possible already. We can try on some existing models like GPT-2(smaller), DallE, etc, and see what the result is.
- Take a CVE -> Generate JSON, for example:
{
"Software": "Apache Log4j2",
"Vulnerable Versions": {
"Start Version": "2.0-beta9",
"End Version": "2.15.0",
"Exclusions": ["2.12.2", "2.12.3", "2.3.1"]
}
}
- There's a database with nix packages and the exact version of each package, for example, here's "bison" (parser-generator): https://lazamar.co.uk/nix-versions/?channel=nixpkgs-20.03-darwin&package=bison
- We can take this and generate a "flake" to create a development environment, container or virtual machine to reproduce the vulnerability.
- An example flake (this is a flake for the OS class that I dropped):
{
inputs = { nixpkgs.url = "nixpkgs/nixos-unstable"; };
description = "Simple filesystem";
outputs = { self, nixpkgs }:
let
system = "x86_64-linux";
pkgs = import nixpkgs { inherit system; };
exfs = pkgs.callPackage ./default.nix { };
in {
devShells."${system}".default = pkgs.mkShell {
# TODO add a testing framework + a fuzzer
# TODO mailutils has to be enabled system-level (kind of obviously)
inputsFrom = [ exfs ];
};
packages."${system}".default = exfs;
# TODO https://nix.dev/tutorials/nixos/nixos-configuration-on-vm
# Create a nix VM to test on with the mailserver
# TODO refactor this into a default.nix..?
# https://www.tweag.io/blog/2023-02-09-nixos-vm-on-macos/ - VM tutorial for flakes
# Necessary configurations for enabling the mail server
nixosModules.base = { pkgs, ... }: {
system.stateVersion = "23.05";
# Configure networking
# networking.useDHCP = false;
# networking.interfaces.eth0.useDHCP = true;
# If I want it to send a "real" email
# might need to enable more stuff..?
environment.systemPackages =
[ pkgs.mailutils exfs ]; # Add my "exfs" file system here as well?
services.postfix.enable = true;
systemd.services.post-fixsetup-maildir = {
description =
"Set up the mail directories (for some reason, they aren't being created automatically)";
serviceConfig.RemainAfterExit = true;
serviceConfig.Type = "oneshot";
# run after postfix service
after = [ "postfix.service" ];
wantedBy = [ "postfix.service" ];
# TODO I can prob write this better somehow but this works..
# Also, this is terrible security practice..
script = ''
mkdir -p /var/spool/mail/userone/cur
mkdir -p /var/spool/mail/userone/new
mkdir -p /var/spool/mail/userone/tmp
chown userone /var/spool/mail/userone/*
chmod a+rwxt /var/spool/mail/userone/*
mkdir -p /var/spool/mail/usertwo/cur
mkdir -p /var/spool/mail/usertwo/new
mkdir -p /var/spool/mail/usertwo/tmp
chmod a+rwxt /var/spool/mail/usertwo/*
'';
};
# TODO the mailbox is not being created properly for some reason
# create two users
users.mutableUsers = false;
# https://discourse.nixos.org/t/impossible-to-log-in-to-result-of-nixos-rebuild-build-vm/9895/3
# need to remove qcow file everytime you change the password..
users.users = {
userone = {
isNormalUser = true;
password = "test";
};
usertwo = {
isNormalUser = true;
password = "test";
};
root = {
password = "test";
};
};
# users.users.userone.isNormalUser = true;
# users.users.root.initialPassword = "test";
# users.users.usertwo.isNormalUser = true;
# Configure networking
networking.useDHCP = false;
networking.interfaces.eth0.useDHCP = true;
# Enable passwordless ‘sudo’ for the "userone" user
users.users.userone.extraGroups = ["wheel"];
security.sudo.wheelNeedsPassword = false;
};
# I can start and run the container in this flake..?
# This creates a container with the
# TODO can't figure out how to enable fuse
# with containers ... so I'll just build a vm instead..?
# nixosConfigurations.container = nixpkgs.lib.nixosSystem {
# system = "x86_64-linux";
# modules = [
# self.nixosModules.base
# ({ pkgs, ... }: {
# boot.isContainer = true;
# # TODO you can also create bindmounts for the container as well in this case..?
# })
# ];
# };
nixosConfigurations.linuxBase = nixpkgs.lib.nixosSystem {
system = "x86_64-linux";
modules = [
self.nixosModules.base
];
};
# TODO you can also create lightweight containers:
# https://www.tweag.io/blog/2020-07-31-nixos-flakes/
};
}- This flake creates an entire Virtual machine / container (I couldn't get the container working b/c FUSE needs access to kernel stuff) that replicates an environment for running the mail-file system in that class.
- We can basically do that but for security vulnerabilities