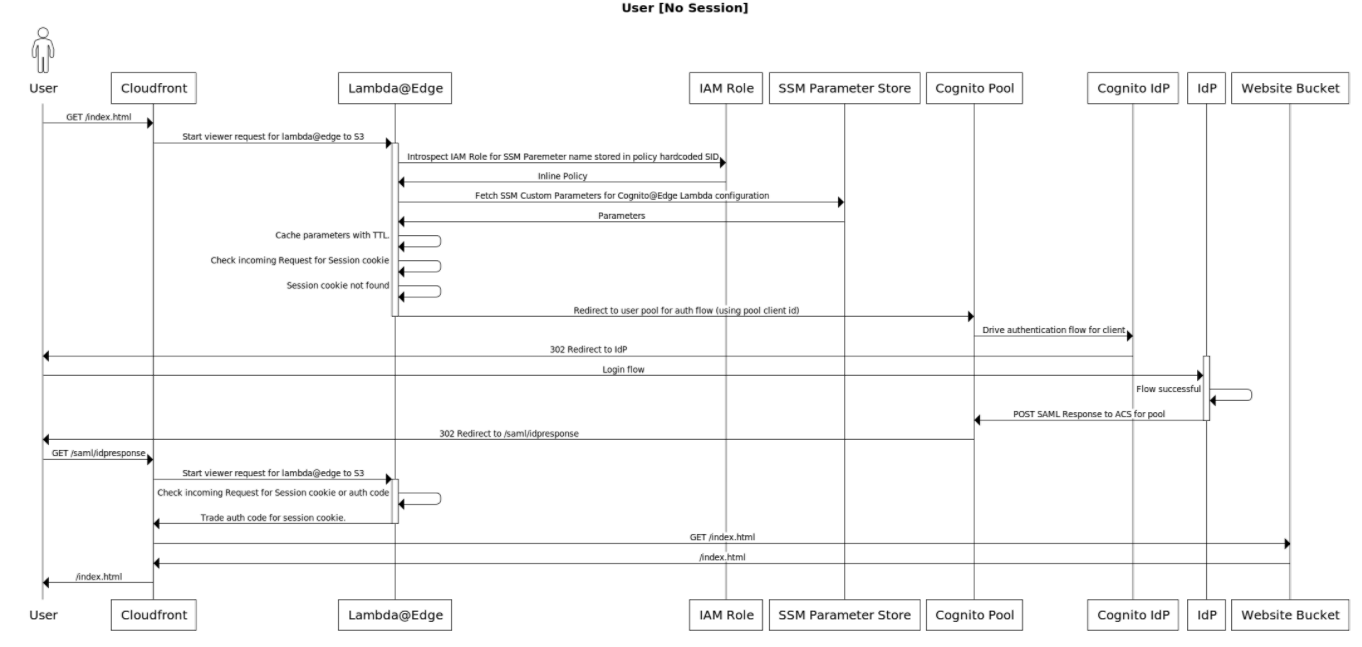
This terraform module creates a Lambda@Edge Lambda to be used within a viewer policy of a CloudFront Distribution to enforce Cognito Authentication through a configured Cognito User Pool.
- Terraform version >= 1.0.X
- NodeJS + NPM (compatible with NodeJS 18.X.X)
- Used for
npm cidependency installation for Lambda@Edge Bundle.
- Used for
- Terraform AWS Provider in
us-east-1- Requirement for CloudFront + Lambda@Edge runtime.
- Existing Cognito User Pool and User Pool Client.
To use this module, source it into one your Terraform project like so:
data "aws_cognito_user_pools" "user_pool" {
name = "my_cognito_pool_name"
}
resource "aws_cognito_user_pool_client" "cognito_client" {
...
}
module "cloudfront_cognito_auth_lambda" {
source = "git::https://github.com/disney/terraform-aws-lambda-at-edge-cognito-authentication.git?ref=<version-ref>"
name = "my-application"
cognito_user_pool_name = data.aws_cognito_user_pools.user_pool.name
cognito_user_pool_region = "us-east-1"
cognito_user_pool_id = aws_cognito_user_pool_client.cognito_client.user_pool_id
cognito_user_pool_app_client_id = aws_cognito_user_pool_client.cognito_client.id
tags = { foo = "bar" }
}
You can use the output of this module to pass as a rule on your CloudFront distribution cache on viewer-requests (typically on an S3 Bucket Origin with an OAI).
resource "aws_cloudfront_distribution" "my_cloudfront_distribution" {
...
ordered_cache_behavior {
...
lambda_function_association {
event_type = "viewer-request"
lambda_arn = module.cloudfront_cognito_auth_lambda.qualified_arn
}
}
}
Note that if a destroy action is performed on this terraform module, terraform is unable to delete the Lambda@Edge that was published as a part of this infrastructure (This is noted by this issue on the Terraform provider). It will only be removed from the terraform state as the skip_destroy flag is set to true.
In order to properly delete this resource, it should be manually cleaned up, instructions here.
| Name | Version |
|---|---|
| terraform | ~> 1.0 |
| aws | >= 4.57 |
| Name | Version |
|---|---|
| archive | 2.4.0 |
| aws | 5.26.0 |
| null | 3.2.2 |
No modules.
| Name | Type |
|---|---|
| aws_iam_role.lambda_at_edge | resource |
| aws_kms_key.ssm_kms_key | resource |
| aws_lambda_function.cloudfront_auth_edge | resource |
| aws_ssm_parameter.lambda_configuration_parameters | resource |
| null_resource.install_lambda_dependencies | resource |
| archive_file.lambda_edge_bundle | data source |
| aws_caller_identity.current | data source |
| aws_iam_policy_document.allow_lambda_service_assume | data source |
| aws_region.current | data source |
| Name | Description | Type | Default | Required |
|---|---|---|---|---|
| cognito_additional_settings | Map of any to configure any additional cognito@edge parameters not handled by this module. | any |
{} |
no |
| cognito_cookie_expiration_days | Number of days to keep the cognito cookie valid. | number |
7 |
no |
| cognito_disable_cookie_domain | Sets domain attribute in cookies, defaults to false. | bool |
false |
no |
| cognito_log_level | Logging level. Default: 'silent' | string |
"silent" |
no |
| cognito_redirect_path | Optional path to redirect to after a successful cognito login. | string |
"" |
no |
| cognito_user_pool_app_client_id | Cognito User Pool App Client ID for the targeted user pool. | string |
n/a | yes |
| cognito_user_pool_app_client_secret | Cognito User Pool App Client Secret for the targeted user pool. NOTE: This is currently not compatible with AppSync applications. | string |
null |
no |
| cognito_user_pool_domain | Optional: Full Domain of the Cognito User Pool to utilize. Mutually exclusive with 'cognito_user_pool_name'. | string |
"" |
no |
| cognito_user_pool_id | Cognito User Pool ID for the targeted user pool. | string |
n/a | yes |
| cognito_user_pool_name | Name of the Cognito User Pool to utilize. Required if 'cognito_user_pool_domain' is not set. | string |
"" |
no |
| cognito_user_pool_region | AWS region where the cognito user pool was created. | string |
"us-west-2" |
no |
| lambda_runtime | Lambda runtime to utilize for Lambda@Edge. | string |
"nodejs20.x" |
no |
| lambda_timeout | Amount of timeout in seconds to set on for Lambda@Edge. | number |
5 |
no |
| name | Name to prefix on all infrastructure created by this module. | string |
n/a | yes |
| tags | Map of tags to attach to all AWS resources created by this module. | map(string) |
{} |
no |
| Name | Description |
|---|---|
| arn | ARN for the Lambda@Edge created by this module. |
| qualified_arn | Qualified ARN for the Lambda@Edge created by this module. |