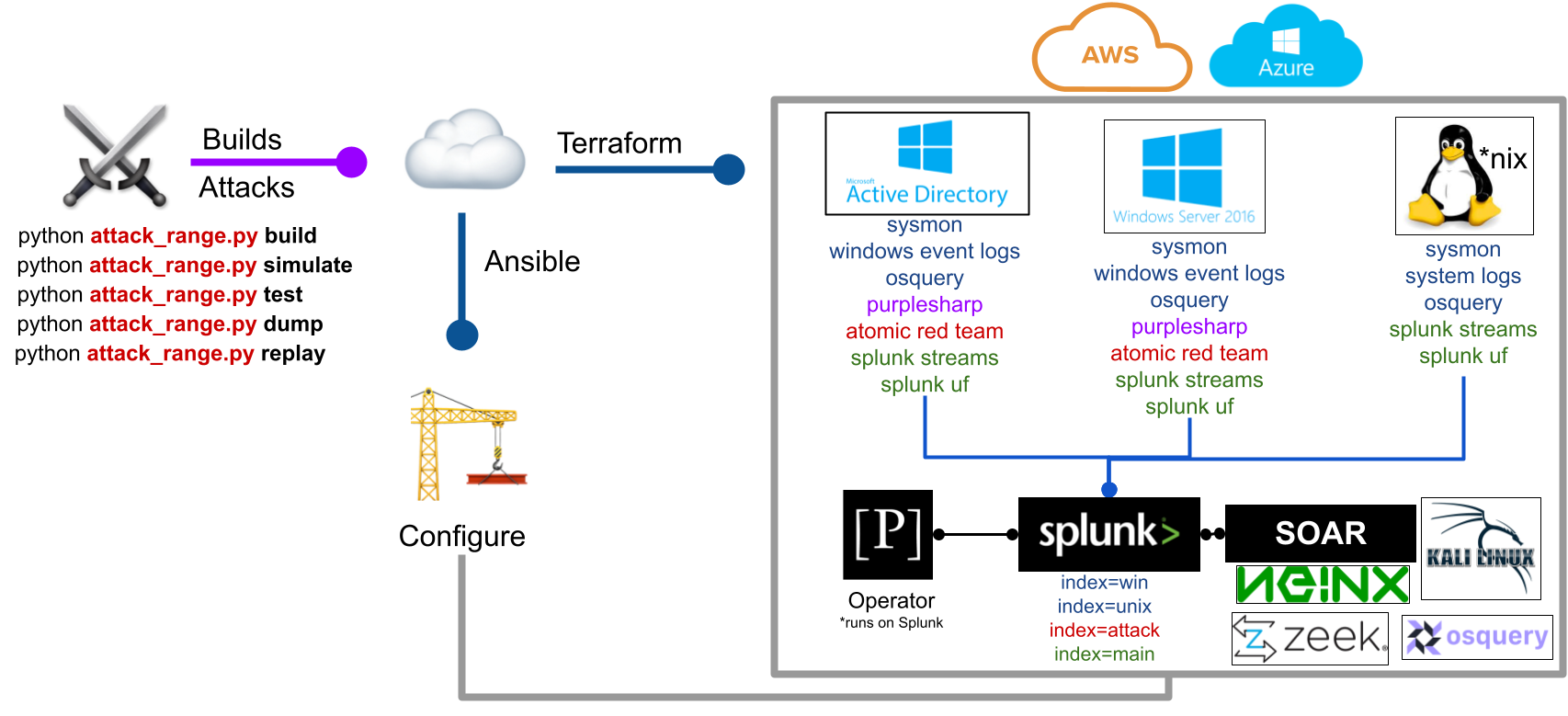
The Attack Range is a detection development platform, which solves three main challenges in detection engineering:
- The user is able to quickly build a small lab infrastructure as close as possible to a production environment.
- The Attack Range performs attack simulation using different engines such as Atomic Red Team or Prelude Operator in order to generate real attack data.
- It integrates seamlessly into any Continuous Integration / Continuous Delivery (CI/CD) pipeline to automate the detection rule testing process.
A demo (~12 min) which shows the basic functions of the attack range. It builds a testing environment using terraform, walks through the data collected by Splunk. Then attacks it using Atomic Red Team with MITRE ATT&CK Technique T1003.002, and Threat Actor simulation playbook using PurpleSharp. Finally showcases how Splunk Security Content searches are used to detect the attack.
docker pull splunk/attack_rangedocker run -it splunk/attack_rangeaws configurepython attack_range.py configure
To install directly on Ubuntu, MacOS follow these instructions.
The deployment of Attack Range consists of:
- Windows Domain Controller
- Windows Server
- Windows Workstation
- A Kali Machine
- Splunk Server
- Splunk SOAR Server
- Nginx Server
- Linux + Sysmon
- Zeek Sensor
Which can be added/removed/configured using attack_range.conf.
An approximate cost estimate for running attack_range on AWS can be found here.
The following log sources are collected from the machines:
- Windows Event (
index = win) - Windows Powershell (
index = win) - Sysmon for Windows EDR (
index = win) - Aurora for Windows EDR (
index = win) - Sysmon for Linux EDR (
index = unix) - OSquery for Linux EDR (
index = osquery) - Nginx Proxy (
index = proxy) - Splunk Streams Network (
index = main) - Zeek Network (
index = main) - Attack Simulations from Atomic Red Team (
index = attack)
Attack Range supports different actions:
python attack_range.py configure
python attack_range.py build
python attack_range.py show
python attack_range.py simulate -e ART -st T1003.001 -t ar-win-dc-default-username-33048
python attack_range.py simulate -e PurpleSharp -st T1003.001 -t ar-win-dc-default-username-33048
python attack_range.py simulate -e PurpleSharp -sp AD_Discovery.json -t ar-win-dc-default-username-33048
python attack_range.py test -tf tests/T1003_001.yml, tests/T1003_002.yml
python attack_range.py destroy
python attack_range.py stop
python attack_range.py resume
python attack_range.py dump -dn data_dump
- Replay previously saved dumps from Attack Range
python attack_range.py replay -dn data_dump -fn FILE_NAME --source SOURCE --sourcetype SOURCETYPE --index INDEX
-
- Indexing of Microsoft Event Logs, PowerShell Logs, Sysmon Logs, DNS Logs, ...
- Preconfigured with multiple TAs for field extractions
- Out of the box Splunk detections with Enterprise Security Content Update (ESCU) App
- Preinstalled Machine Learning Toolkit (MLTK)
- pre-indexed BOTS datasets
- Splunk UI available through port 8000 with user admin
- ssh connection over configured ssh key
-
- Splunk Enterprise Security is a premium security solution requiring a paid license.
- Enable or disable Splunk Enterprise Security in attack_range.conf
- Purchase a license, download it and store it in the apps folder to use it.
-
- Splunk SOAR is a Security Orchestration and Automation platform
- For a free development license (100 actions per day) register here
- Enable or disable Splunk SOAR in attack_range.conf
-
Windows Domain Controller & Window Server & Windows 10 Client
- Can be enabled, disabled and configured over attack_range.conf
- Collecting of Microsoft Event Logs, PowerShell Logs, Sysmon Logs, DNS Logs, ...
- Sysmon log collection with customizable Sysmon configuration
- RDP connection over port 3389 with user Administrator
-
- Attack Simulation with Atomic Red Team
- Will be automatically installed on target during first execution of simulate
- Atomic Red Team already uses the new Mitre sub-techniques
-
- Native adversary simulation support with PurpleSharp
- Will be automatically downloaded on target during first execution of simulate
- Supports two parameters -st for comma separated ATT&CK techniques and -sp for a simulation playbook
-
- Adversary Emulation with Prelude Operator
- Headless v1.6 Installed on the Splunk Server, see guide for more details.
- Preinstalled Prelude Operator Pneuma agent across Windows and Linux machines
-
- Preconfigured Kali Linux machine for penetration testing
- ssh connection over configured ssh key
Please use the GitHub issue tracker to submit bugs or request features.
If you have questions or need support, you can:
- Join the #security-research room in the Splunk Slack channel
- Post a question to Splunk Answers
- If you are a Splunk Enterprise customer with a valid support entitlement contract and have a Splunk-related question, you can also open a support case on the https://www.splunk.com/ support portal
We welcome feedback and contributions from the community! Please see our contribution guidelines for more information on how to get involved.
- Bhavin Patel
- Rod Soto
- Russ Nolen
- Phil Royer
- Joseph Zadeh
- Rico Valdez
- Dimitris Lambrou
- Dave Herrald
- Ignacio Bermudez Corrales
- Peter Gael
- Josef Kuepker
- Shannon Davis
- Mauricio Velazco
- Teoderick Contreras
- Lou Stella
- Christian Cloutier
- Eric McGinnis
- Micheal Haag