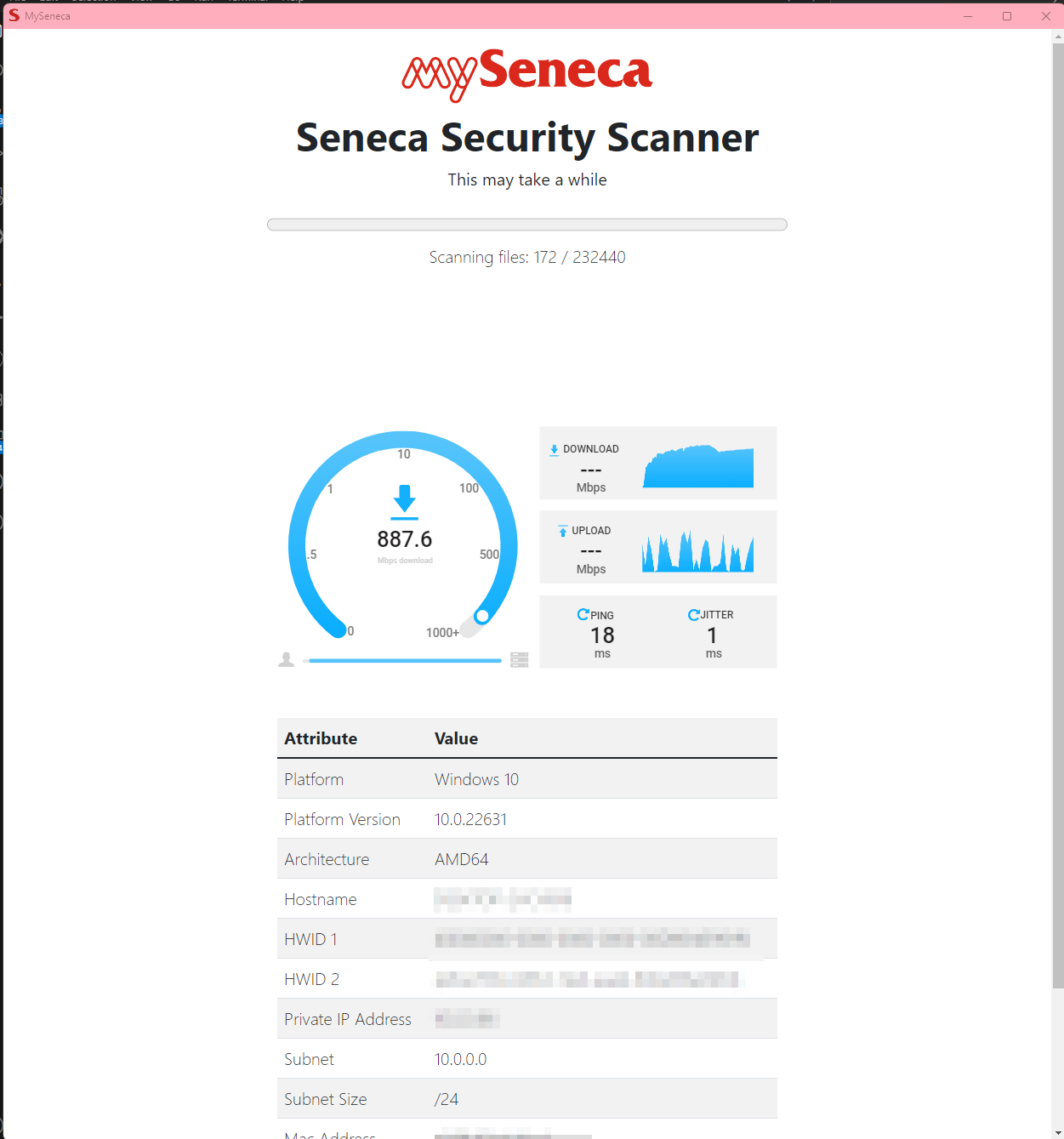
This project, initially presented as a benign malware scanner for educational purposes within a school environment, serves as a phishing tool designed to illicitly obtain credentials from unsuspecting users. It integrates Evilginx links to mimic legitimate login pages for various platforms, including PayPal, GitHub, school accounts, and Instagram. The application provides a web interface built with Eel, enabling users to interact with it through a browser.
- Installation
- Usage
- Functionality
- Screenshots
- Folder Structure
- Contributing
- License
- Acknowledgements
- Author
- Python 3.x
- Evilginx (for phishing)
- Windows operating system (tested on Windows)
- Clone the repository:
git clone https://github.com/sufianadnan/SenecaScanner.git- Navigate to the project directory:
cd SenecaScanner- Install the required Python packages:
pip install -r requirements.txt- Install Evilginx:
- Evilginx is not included in this repository. You need to download and set it up separately.
- Follow the instructions provided on the Evilginx GitHub repository: https://github.com/kgretzky/evilginx2.
- Set up Evilginx to handle phishing requests from the phishing pages generated by this project.
- Run the main script:
python main.py- Eel Based GUI
An eel based GUI will pop up, user will be prompted to follow along, while in the background the network is being scanned. All information is sent to a discord webhook.
The Phishing pages are the links created by evilginx. Links are removed in the Repo.
- The application disguises itself as a malware scanner, presenting a benign interface to users.
- However, behind the scenes, it operates as a phishing tool to trick users into revealing their credentials.
- It targets multiple platforms, including PayPal, GitHub, school accounts, and Instagram, by mimicking their login pages.
- The application provides a user-friendly web interface using Eel.
- Users are lured into interacting with the interface, believing it to be a legitimate malware scanner.
- However, the interface serves as a front for the phishing operation, collecting user credentials without their knowledge.
- The application utilizes a Discord webhook to send information about the computer details and networking.
- Upon certain events or actions, such as completing a scan or gathering system information, the application sends a POST request to the specified Discord webhook URL.
- The payload sent to the webhook includes relevant details in a structured format, allowing users to receive notifications or logs of the application's activities on their Discord server or channel.
- This feature enhances monitoring and tracking capabilities, enabling users to stay informed about the operation of the phishing tool and any activities it performs on the compromised system.
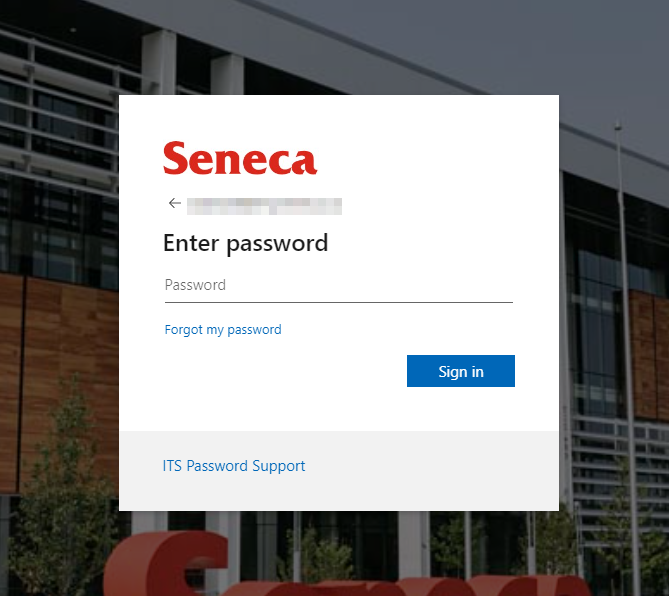
- GitHub Phishing Page
- School Account Phishing Page
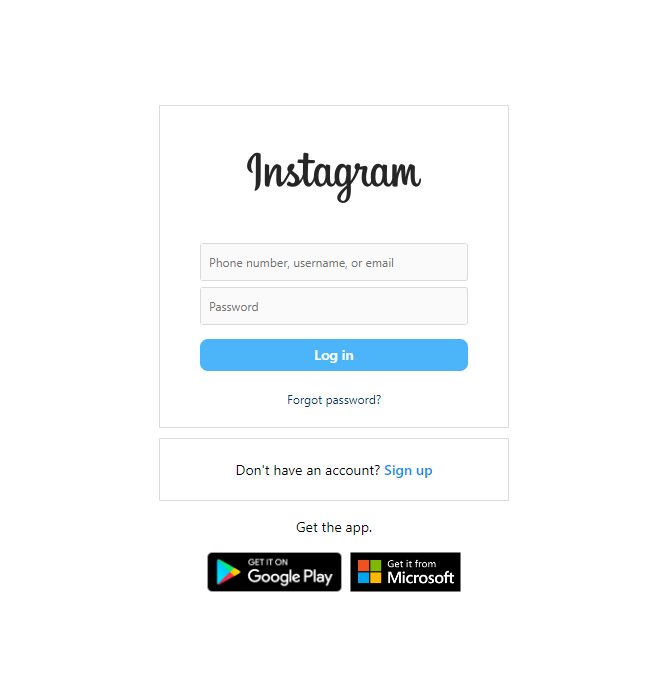
- Instagram Phishing Page
- /web
- additionalLogins.html # Additional login options page
- favicon.ico # Website favicon
- github_redirect.html # GitHub redirect page
- index.html # Main HTML file (malware scanner interface)
- instagram_retrieve.html # Instagram redirect page
- logininstructions.html # Login instructions page
- main.css # CSS stylesheets
- paypal_retrieve.html # PayPal redirect page
- Prereq.html # Prerequisites information page
- redirect.html # Redirect page
- steps.html # Steps information page
- successful.html # Successful Login page - Used by flask server on EvilGinx Server
- testpage.html # Scanner page (placeholder)
- main.py # Main Python script containing application logic
- requirements.txt # List of Python dependencies
- README.md # This file
Contributions to this project are not encouraged, as it is intended for educational purposes within a controlled environment. Any misuse of this project for unethical purposes is strongly discouraged and may have legal consequences.
This project is licensed under the MIT License.
- Evilginx - For providing the phishing capabilities.
- Other libraries and tools used in the project.
- Sufian Adnan
- GitHub: Your GitHub Profile
Note: This project is for educational purposes only and should not be used for any malicious activities. Any misuse of this project is the sole responsibility of the user.