cri-containerd is a containerd based implementation of Kubernetes container runtime interface (CRI).
With it, you could run Kubernetes using containerd as the container runtime.
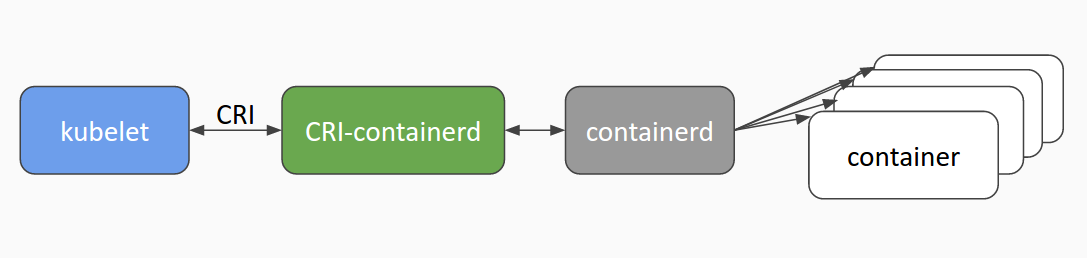
cri-containerd is in beta:
- It is feature complete.
- It (the beta version) works with Kubernetes >= 1.9.
- It has passed all CRI validation tests.
- It has passed all regular node e2e tests.
- It has passed all regular e2e tests.
See test dashboard
| CRI-Containerd Version | Kubernetes Version |
|---|---|
| v1.0.0-alpha.x | 1.7, 1.8 |
| v1.0.0-beta.x | 1.9+ |
For a production quality cluster on GCE brought up with kube-up.sh refer here.
For a multi node cluster installer and bring up steps using ansible and kubeadm refer here.
For non ansible users, you can download the cri-containerd release tarball and deploy
kubernetes cluster using kubeadm as described here.
The current release of cri-containerd has the following dependencies:
See versions of these dependencies cri-containerd is tested with.
As containerd and runc move to their respective general availability releases,
we will do our best to rebase/retest cri-containerd with these releases on a
weekly/monthly basis. Similarly, given that cri-containerd uses the Open
Container Initiative (OCI) image
and runtime specifications, we
will also do our best to update cri-containerd to the latest releases of these
specifications as appropriate.
- Install development libraries:
- libseccomp development library. Required by cri-containerd and runc seccomp support.
libseccomp-dev(Ubuntu, Debian) /libseccomp-devel(Fedora, CentOS, RHEL). On releases of Ubuntu <=Trusty and Debian <=jessie a backport version oflibseccomp-devis required. See travis.yml for an example on trusty. - libapparmor development library. Required by cri-containerd and runc apparmor support. To use apparmor on Debian, Ubuntu, and related distributions the installation of
libapparmor-devis required. - btrfs development library. Required by containerd btrfs support.
btrfs-tools(Ubuntu, Debian) /btrfs-progs-devel(Fedora, CentOS, RHEL)
- Install other dependencies:
nsenter: Required by CNI and portforward.socat: Required by portforward.
- Install and setup a go 1.9.x development environment.
- Make a local clone of this repository.
- Install binary dependencies by running the following command from your cloned
cri-containerd/project directory:
# Note: install.deps installs the above mentioned runc, containerd, and CNI
# binary dependencies. install.deps is only provided for general use and ease of
# testing. To customize `runc` and `containerd` build tags and/or to configure
# `cni`, please follow instructions in their documents.
make install.depsTo build and install cri-containerd enter the following commands from your cri-containerd project directory:
make
sudo make installcri-containerd supports optional build tags for compiling support of various features.
To add build tags to the make option the BUILDTAGS variable must be set.
make BUILD_TAGS='seccomp apparmor'| Build Tag | Feature | Dependency |
|---|---|---|
| seccomp | syscall filtering | libseccomp development library |
| selinux | selinux process and mount labeling | |
| apparmor | apparmor profile support | libapparmor development library |
A Kubernetes incubator project called cri-tools
includes programs for exercising CRI implementations such as cri-containerd.
More importantly, cri-tools includes the program critest which is used for running
CRI Validation Testing.
Run the CRI Validation test to validate your installation of cri-containerd:
make test-criIf you already have a working development environment for supported Kubernetes
version, you can try cri-containerd in a local cluster:
- Start
containerdas root in a first terminal:
sudo containerd- Start
cri-containerdas root in a second terminal:
sudo cri-containerd- From the Kubernetes project directory startup a local cluster using
cri-containerd:
CONTAINER_RUNTIME=remote CONTAINER_RUNTIME_ENDPOINT='/var/run/cri-containerd.sock' ./hack/local-up-cluster.shSee here for information about test.
See here for information about using crictl to debug
pods, containers, and images.
See here for additional documentation.
Interested in contributing? Check out the documentation.
This project was originally established in April of 2017 in the Kubernetes Incubator program. After reaching the Beta stage, In January of 2018, the project was merged into containerd.
For async communication and long running discussions please use issues and pull requests on this github repo. This will be the best place to discuss design and implementation.
For sync communication we have a community slack with a #containerd channel that everyone is welcome to join and chat about development.
Slack: https://dockr.ly/community
As this project is tightly coupled to CRI and CRI-Tools and they are Kubernetes
projects, some of our project communications take place in the Kubernetes' SIG:
sig-node.
For more information about sig-node, CRI, and the CRI-Tools projects:
- sig-node community site
- Slack:
#sig-nodechannel in Kubernetes (kubernetes.slack.com) - Mailing List: https://groups.google.com/forum/#!forum/kubernetes-sig-node
If you are reporting a security issue, please reach out discreetly at security@containerd.io.
The containerd codebase is released under the Apache 2.0 license. The README.md file, and files in the "docs" folder are licensed under the Creative Commons Attribution 4.0 International License under the terms and conditions set forth in the file "LICENSE.docs". You may obtain a duplicate copy of the same license, titled CC-BY-4.0, at http://creativecommons.org/licenses/by/4.0/.
This project follows the CNCF Code of Conduct.

