KDC Implementation using NeedhamSchroedar Protocol - Cybersecurity
The following command-line should be used to compile all the 3 files:
#!shell
gcc -O2 -Wall -fPIC aes.c <input> -o <output> -lmcrypt
where, is the source file (Alice.c / Bob.c / KDC.c) is the compiled file
-
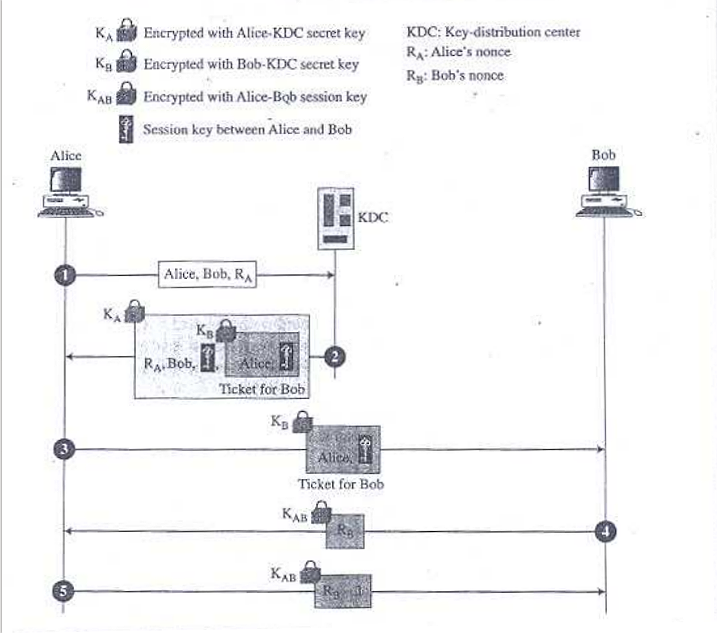
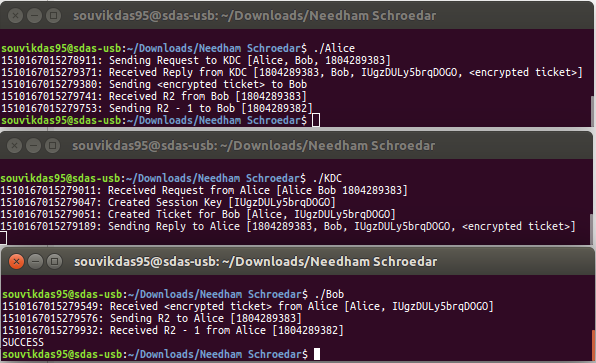
Alice sends Request to KDC
This requires the use of a special structure (kdc_request_s) to contain 3 (+1) parameters:
- Source (Alice)
- Target (Bob)
- Source Nonce (R1 or RA) (Generated by Alice)
- (Optional) Padding (to match with AES blocksize)
The same structure is shared with KDC to receive the data in formatted plaintext.
-
KDC sends Reply to Alice
This requires the use of a special structure (kdc_reply_s) to contain 4 (+1) parameters:
- Source Nonce (R1 or RA)
- Target (Bob)
- Session Key (KAB) (Generated by KDC)
<encrypted ticket>(Ticket is encrypted using Bob’s key after being generated by KDC)- (Optional) Padding (to match with AES blocksize)
The same structure is shared with Alice to receive data in ciphertext and decrypt into formatted plaintext.
The Ticket so encrypted requires an additional structure (ticket_s) to contain 2 parameters:
- Source (Alice)
- Session Key (KAB)
The same structure is shared with Bob to receive the data in ciphertext and decrypt into formatted plaintext.
-
Alice sends Encrypted Ticket to Bob
This stage simply involves forwarding the received payload from KDC directly to Bob since Alice doesn’t have Bob’s key to decrypt the ticket, to be sent to Bob.
-
Bob sends Nonce (R2 or RB) to Alice
- Bob generates Nonce (R2 or RB).
- Then ecrypts it using the Session Key (KAB).
- Then sends the ciphertext to Alice which she can easily decrypt using the shared ession Key (KAB).
-
Alice sends (R2 - 1) to Bob
- Alice subtracts 1 from the Nonce (R2 or RB).
- Then ecrypts it using the Session Key (KAB).
- Then sends the ciphertext to Bob which he can easily decrypt using the shared ession Key (KAB).
- Bob simply compares the expected value with the received value.
- If confirmed, establishment of the Session by announcing “SUCCESS”
-
allocateRandomString()
Creates a random character string of required length from a chosen charset.
-
getTimestamp_usec()
Fetches 64-bit accurate timestamp (in microseconds w/ count from EPOCH)
-
AES Library Methods
AES Library Methods such as encrypt() and decrypt() are used.
-
Quick summary:
Cybersecurity Assignment Project - Implementation of Needham Schroedar Protocol
- Requirements
- CC/GCC Toolkit
- Mcrypt library
- Author: Souvik Das (souvikdas95@yahoo.co.in)