How to run your own GitHub build farm on a Kubernetes cluster, article, code
This work is largely based on the work done by Sander Knape and David Karlsen:
Modifications:
- Added a sidecar docker-dind with TLS TCP communication between the client and the daemon containers
- Made it dedicated to establish a pool of runners associated to a GitHub organization, not to a particular repository
- Added a way to prefix the runners names (with RUNNER_NAME_PREFIX env variable)
- Removed the sudo package, sudo group and passwordless sudoers from the container user
- Added a way to use self signed certificates for a local registry as a config map
-
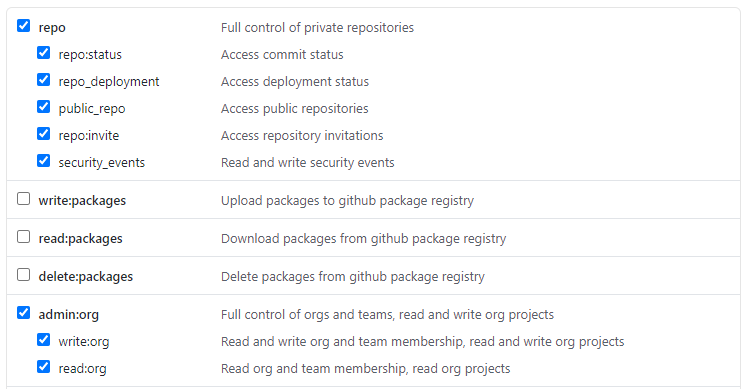
As an organization owner, create a GitHub Personal Access Token with the repo and admin:org scope permissions:
-
Create a generic secret with your GitHub Personal Access Token
kubectl create secret generic my-pat --from-literal=pat=XXXXXXXXXXXXXXXXXX
-
If you want to include your registry self-signed CA certificate, use a config map
kubectl create configmap private-registry-certificate --from-file=ca.crt
-
Adapt the deployment.yml Deployment resource to reflect your organization name in the GITHUB_OWNER environment variable, and deploy:
kubectl create -f k8s-example/deployment.yml
-
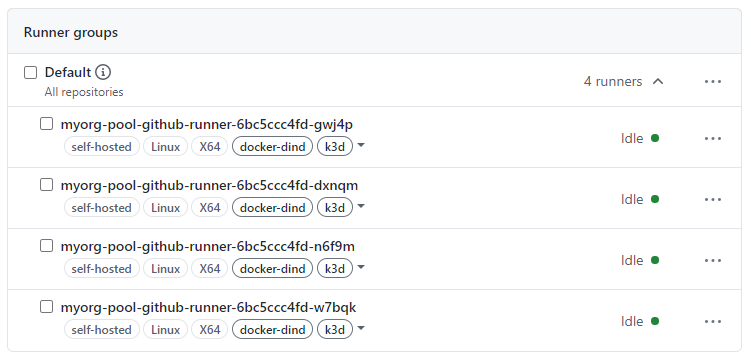
You should see your runners appearing in the default group of your organization: