The Music Store
Runnning
If you only want to try the application without modifying it, run the build and start the components with docker-compose.
mvn clean package
docker-compose upWhen all components are up browse to http://localhost:8080.
Otherwise start each component individually.
The Postgres database
docker run --rm --name musicstore-db -e POSTGRES_USER=music -e POSTGRES_PASSWORD=music -e POSTGRES_DB=musicdb -p 5432:5432 postgresThe MongoDB server
docker run --rm --name musicstore-mongo -p 27017:27017 mongoDevelopment
-
Do one time build to pull the dependencies
mvn clean install -
To run the application in foreground do
mvn vertx:runwith redeploy enabled -
To run the applicaiton in background mode i.e. vertx start do
mvn vertx:start
Check vertx-maven-plugin for more information and examples on the plugin.
Useful stuff
Initial dataset
The initial dataset has been created with the initdb.groovy script located at the project root.
It parses a Rhythmbox database file and inserts the data into Postgres.
Then it’s easy to create a script for Flyway.
docker exec musicstore-db pg_dump -a --inserts --exclude-table=schema_version -h 127.0.0.1 -U music musicdb > src/main/resources/db/migration/V2__InsertData.sqlInstall HDIV Agent
-
Copy agent jar to hdiv/agent folder.
-
Copy Hdiv license to hdiv/conf folder
Vulnerable end-points
SQl Injection
Threre are two sql injection vulnerable endpoints:
-
Threre is an endpoint which you could download artists data in CSV file. You should filter by artistid parameter: http://localhost:8080/api/csv?artistId=1 union select 1,1,1,1,1,1,username, password from users.
Path traversal
There is an endpoint through which you can read remote files on the server. User parameter "filename" to set the path and name of the file to read.
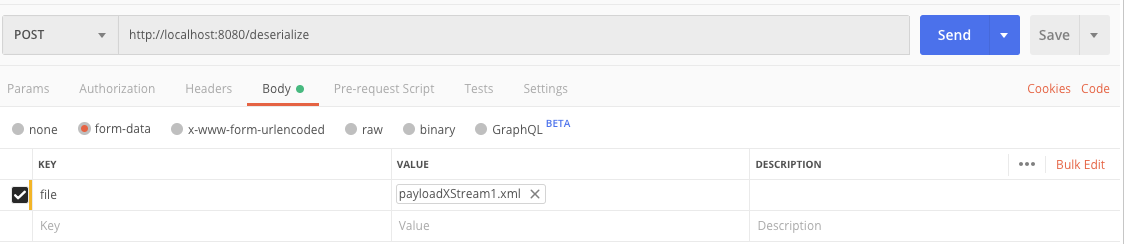
Untrusted deserialization
-
Upload XML files and deserialize with XStream.
-
There are four example RCE payloads in: src/resources/payloadXStreamXXX.xml.
-
You could try it from postman using url: http://localhost:8080/deserialize.
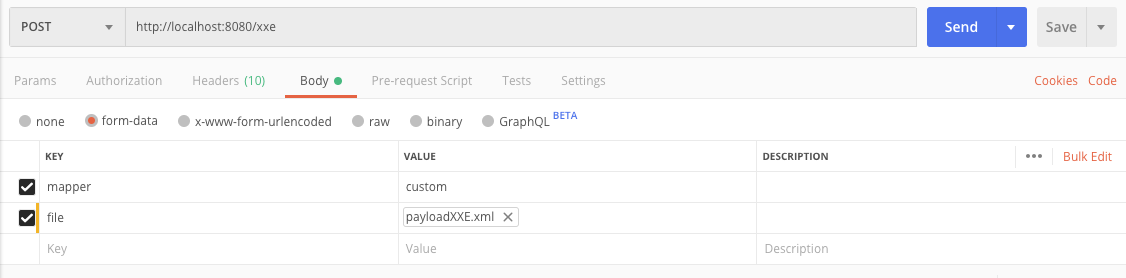
XXE
-
Upload XML files and map to java objects.
-
There is an example RCE payload in: src/resources/payloadXXE.xml
-
There is an example normal payload in: src/resources/payloadFoo.xml
-
You could try it from postman using url: http://localhost:8080/xxe.
-
The xml can be processed by Jackson or SAX. Use parameter "mapper" with values: custom or jackson.
XPath Injection
Simulate a dummy login process where list of users is in XML. * If endpoint return true, you have access permissions. * If endpoint return false, you don’t have access permissions.
Examples:
-
Access granted: http://localhost:8080/xpath?user=neo&pass=trinity
-
Access denied: http://localhost:8080/xpath?user=neo&pass=trinityXX
-
Access granted: http://localhost:8080/xpath?user=1' or '1'='1&pass=1' or '1'='1