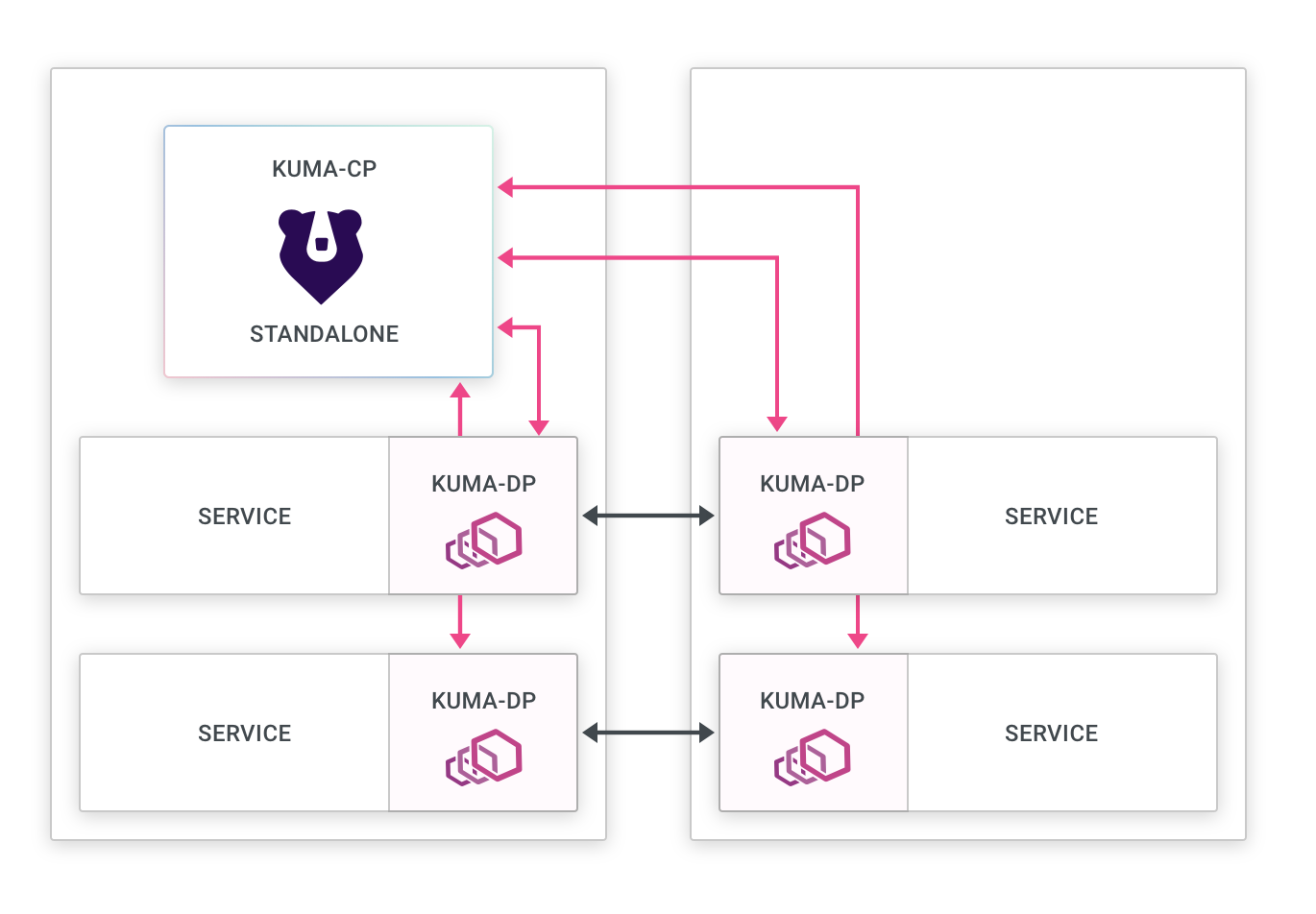
This example assumes installition on an existing k8s cluster, then installs Kong Mesh Enterprise on that cluster in Standalone mode. It also provides instructions for installing Konnect dataplanes
- AKS Credentials (App ID and Password)
- Terraform CLI
- Azure CLI
- AKS Domain name
- Kong Mesh Enterprise license
- Konnect login
- Konnect Personal Access Token (pat)
If you don't already have a k8s cluster stood up, please follow the below instructions to install a vanilla instance of AKS:
-
Open
/tf-provision-aks/aks-cluster.tfto search & replacesimongreenwith your own name. That way, all AKS objects will be tagged with your name making them easily searchable. Also, update the Azure region in this file to the region of your choice. -
If you haven't done so already, create an Active Directory service principal account via the CLI:
az login
az ad sp create-for-rbac --skip-assignment. # This will give you the `appId` and `password` that Terraform requires to provision AKS.- In
/tf-provision-aksdirectory, create a file calledterraform.tfvars. Enter the following text, using your credentials from the previous command:
appId = "******"
password = "******"
location = "East US"- Via the CLI,
cd tf-provision-aks/then run the following Terraform commands to provisions AKS:
terraform init
terraform apply- Once terraform has stoodup AKS, setup
kubectlto point to your new AKS instance:
az aks get-credentials --resource-group $(terraform output -raw resource_group_name) --name $(terraform output -raw kubernetes_cluster_name)
kubectl get all-
Insert your Enterprise license under
./license/license.jsonof this directory. -
Using
helm, run the following command:
helm repo add kong-mesh https://kong.github.io/kong-mesh-charts- Using kubectl, run the following command:
kubectl create namespace kong-mesh-system- Create the license secret:
kubectl create secret generic kong-mesh-license -n kong-mesh-system --from-file=license/license.json- Install Kong Mesh:
helm repo update
helm upgrade -i -n kong-mesh-system kong-mesh kong-mesh/kong-mesh \
--set 'kuma.controlPlane.secrets[0].Env="KMESH_LICENSE_INLINE"' \
--set 'kuma.controlPlane.secrets[0].Secret="kong-mesh-license"' \
--set 'kuma.controlPlane.secrets[0].Key="license.json"'-
From the Konnect runtime instance page, copy the contents of the certificate and key to konnect/tls.crt and konnect/tls.key respectively.
-
Create the namespace and secrets
kubectl create namespace kong
helm repo add kong https://charts.konghq.com
helm repo update
kubectl create secret tls kong-cluster-cert -n kong --cert=konnect/tls.crt --key=konnect/tls.key-
Copy the configuration parameters from Konnect to konnect/values.yaml.
-
Install (or upgrade) kong using the new configuration:
helm upgrade --install kong kong/kong -n kong --values konnect/values.yaml-
Via the Konnect runtime instances page, ensure the new dataplane (runtime instance) has connected.
-
Via the CLI, figure out what the external IP is of the Konnect dataplane:
kubectl get services --all-namespaces -o json | jq -r '.items[] | { name: .metadata.name, ns: .metadata.namespace, ip: .status.loadBalancer?|.ingress[]?|.ip }'-
Update konnect/konnect-ingress.yaml file with the external IP, by using search+replace on
999.999.999.999. Save the file. -
Copy your Konnect personal access token (pat) to a file call
pat -
Run
deck sync --konnect-runtime-group-name default --konnect-token-file pat --state=konnect/konnect-ingress.yamlto create the Services and Routes. -
Via the Browser, copy the external address. This will form your GUI URL:
http://mesh-gui.app.<external address>.nip.io/gui -
Click through the wizard, choosing the Standalone deployment. Next choose Kubernetes. Then choose the Demo App.
-
As per the instructions, copy the
kubectlcommand and create the DemoApp in your cluster. -
Via a new browser tab, copy the external address. This will form your GUI URL:
http://demo-app.app.<external address>.nip.io
- Enable mTLS using the following command:
kubectl apply -f konnect/mtls.yaml-
Via the Mesh GUI, navigate to Data Plane Proxies and click the Create data plane proxy button.
-
Select default mesh, then click Next.
-
In the namespace field, type
kongwhich is where the Konnect dataplane ingress point is running. -
Copy and paste the CRD that is generated and execute it via the CLI.
-
Give it a couple of minutes, as the pods need to restart. After a short wait, you should now see 3 DP proxies on the dashboard, including the kong proxy apearing as
gateway_delegated. -
To test, navigate to http://demo-app.app..nip.io/ and you should be able to see the
Kuma Counter Demo 1.0app.