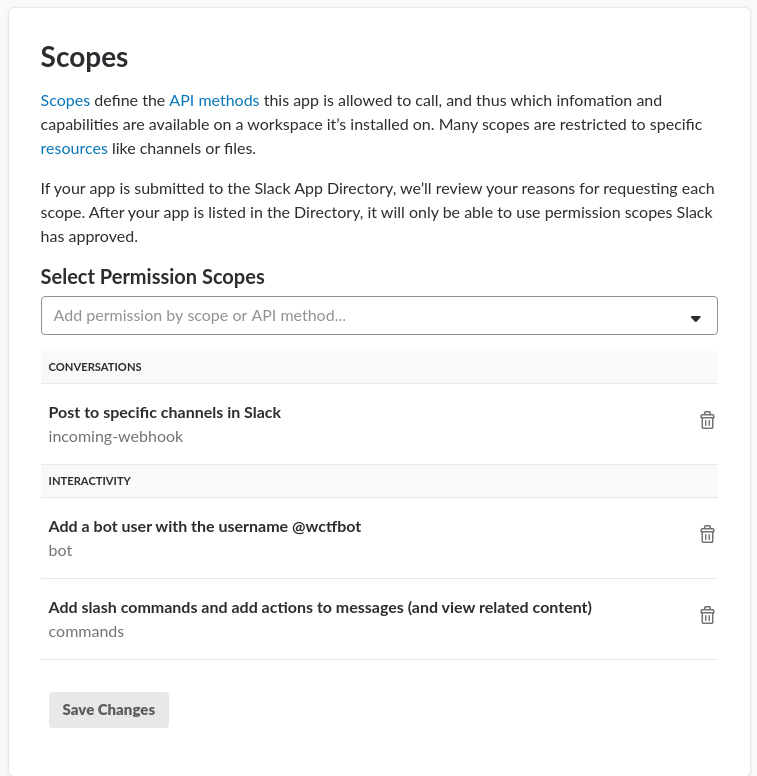
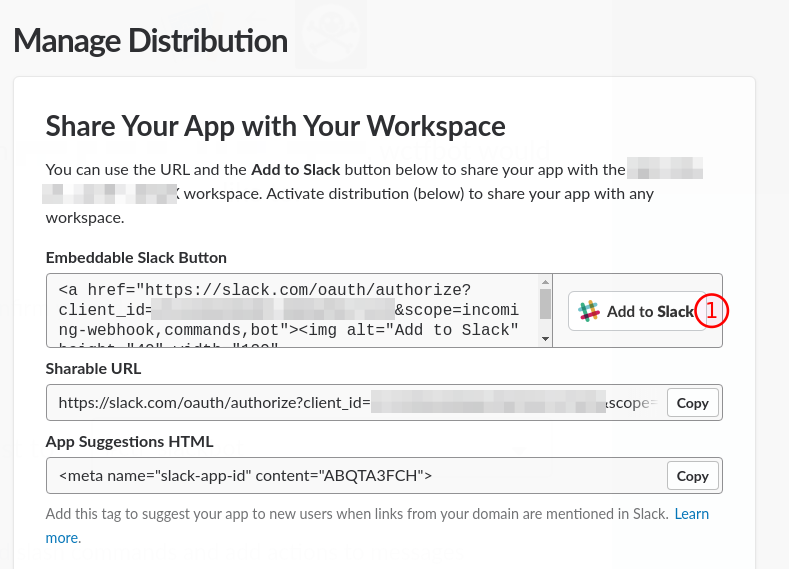
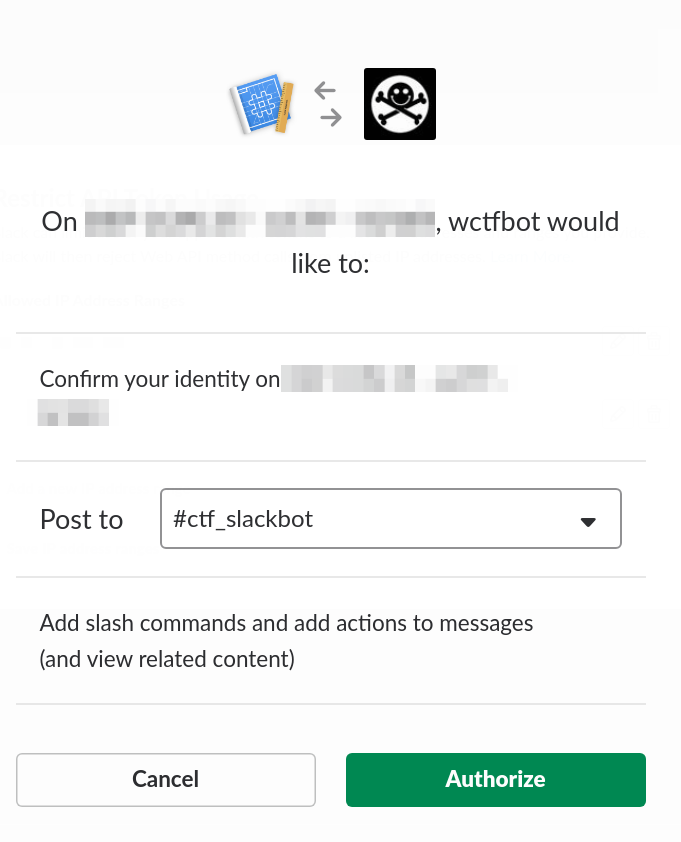
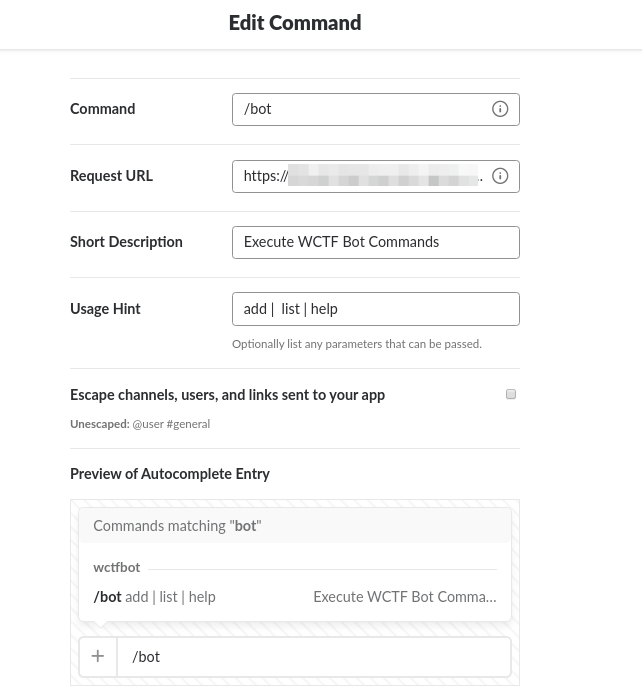
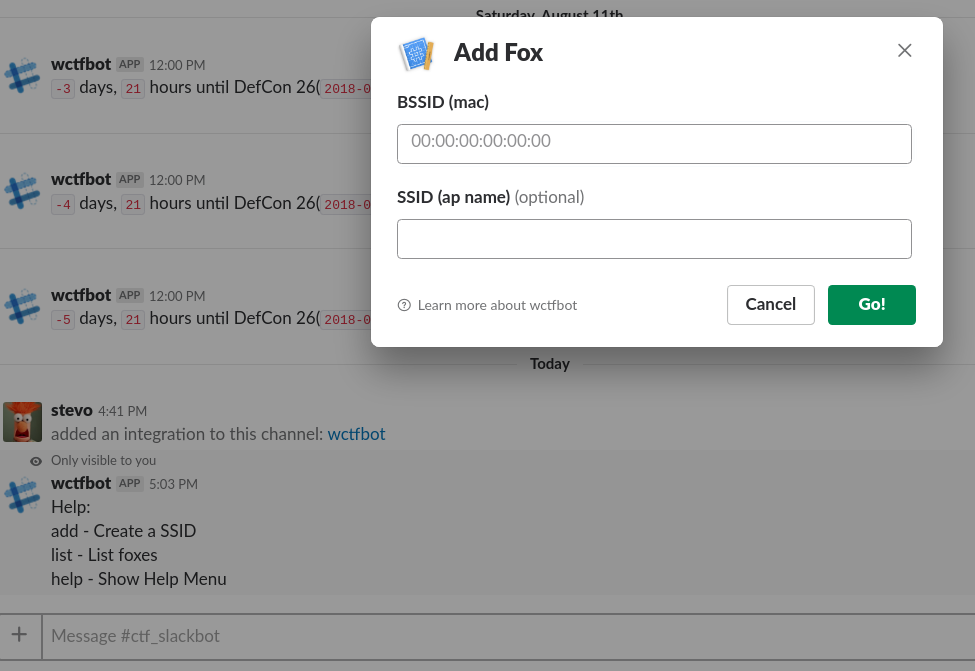
Related to project: https://github.com/shollingsworth/piClicker
Setup a profile in ~/.aws/credentials
example:
[myprofile]
aws_access_key_id = xxxxxxxxxxxxxxxxxxxx
aws_secret_access_key = xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
Run:
./setup_virtualenv.sh
source ./venv/bin/activate
See: https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/elastic-ip-addresses-eip.html
Run the command: (this will likely take ~20 minutes to complete, mostly due to RDS setup)
./env_setup/setup_lambda_rds.py --environment dev --profile personal --eip1 eipalloc-xxxxxxxx --eip2 eipalloc-xxxxxxxx --acl 8.8.8.8/32
for more flags issue ./env_setup/setup_lambda_rds.py -h
1.) Delete contents of created bucket 2.) Go to cloudformation, delete stack with the label previously assigned in the setup_lambda_rds command
./env_setup/modify_db.py init --environment dev --sql_user mysqluser
using example in ./env_setup/dev.json
"connection_type" : "mysql_rds"
"ctftoken" : "Q4stYvFUQJV0bewIvcuwILD2X0j12IVPbg7dHzsy"
"events": []
"log_level": 'DEBUG'
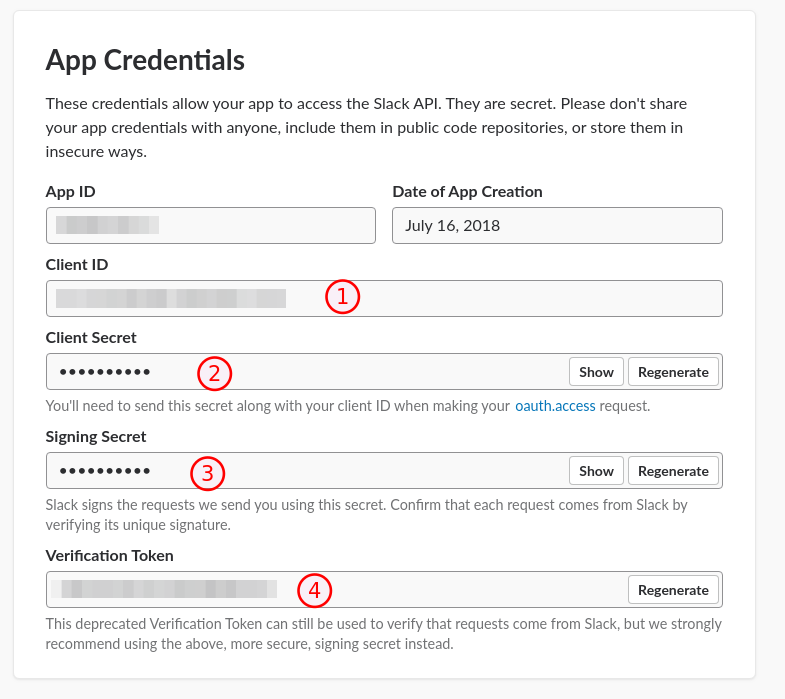
"team_id": "TXXXXXX"- See https://stackoverflow.com/a/44883343/7049363 on how to grab this from the web UI
edit botconfig.py and set ENABLE_CALLBACK to True
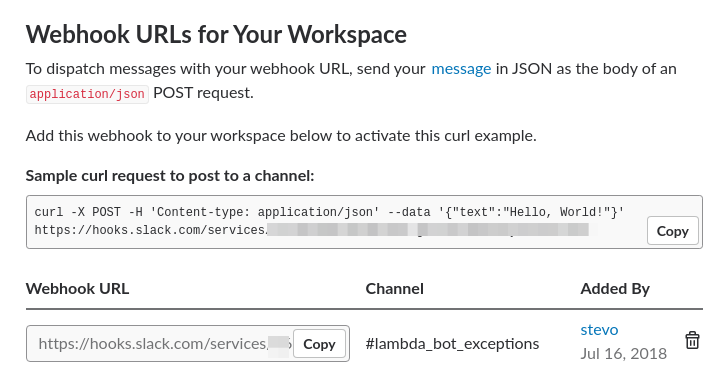
- Create channel
#lambda_bot_exceptions - setup webhook for exceptions
- insert gpg key fingerprint (no spaces) into
./env_setup/gpg.recipients - run
./env_setup/genzappa_settings.py- this will generate the
zappa_config.jsonand encrypt the config's secrets for storage in source control (if desired)
- this will generate the
- run
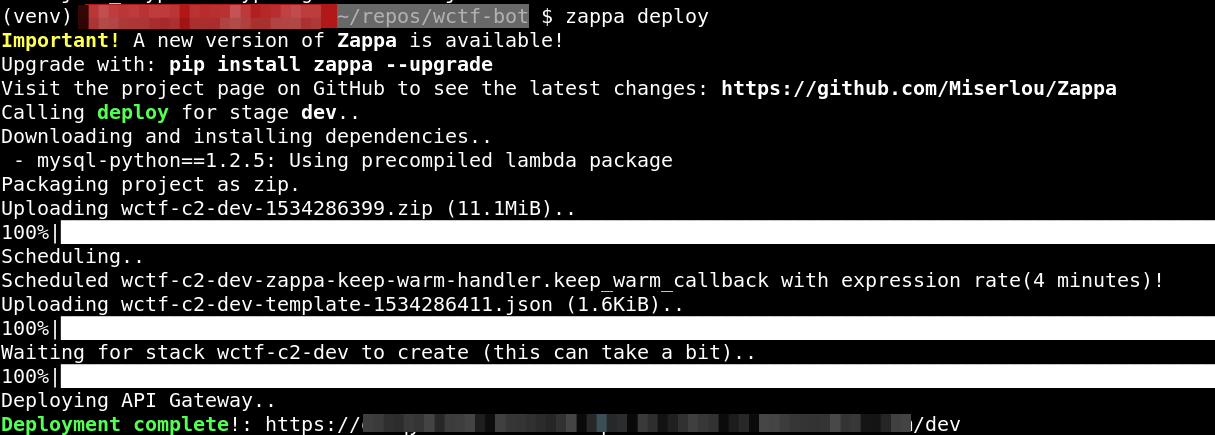
./setup_virtualenv.shandsource ./venv/bin/activeto prep environment - zappa deploy, make note of the URL for next steps
- enter callback url with ext
/callbacki.e.https://xxxxxxx.execute-api.us-east-2.amazonaws.com/dev/callback 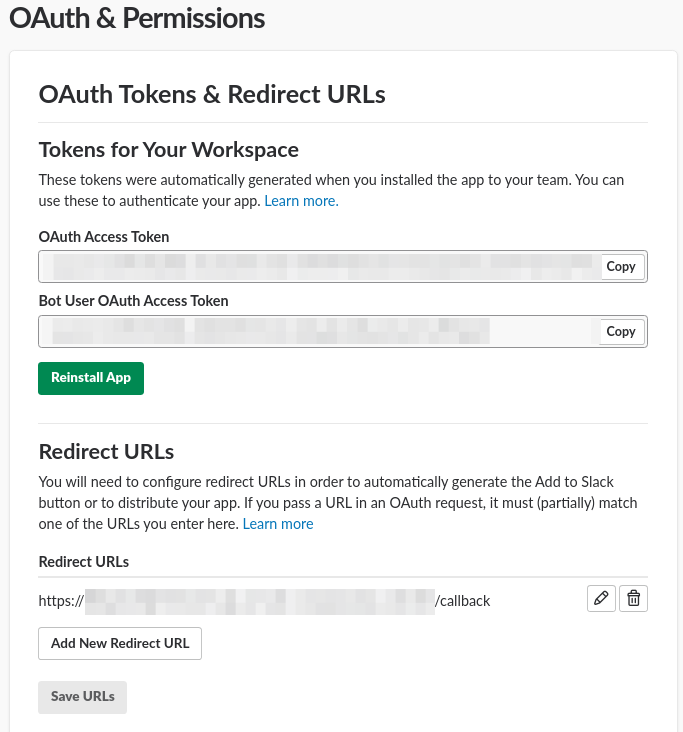
- Add to workspace
- Set Default bot channel
- verify the authdata is there with the command:
zappa invoke scheduled_tasks.show_authed_teams- you should see a json output with the newly created auth data!
- run:
./env_setup/data_import_export.py export -e dev -d ./env_setup - move the file to ./env_setup/authed-data.json, and edit out all tables other than
authed_data
- enter base url for request component url
/formi.e.https://xxxxxxx.execute-api.us-east-2.amazonaws.com/dev/form - enter base url for options load url
/menui.e.https://xxxxxxx.execute-api.us-east-2.amazonaws.com/dev/menu 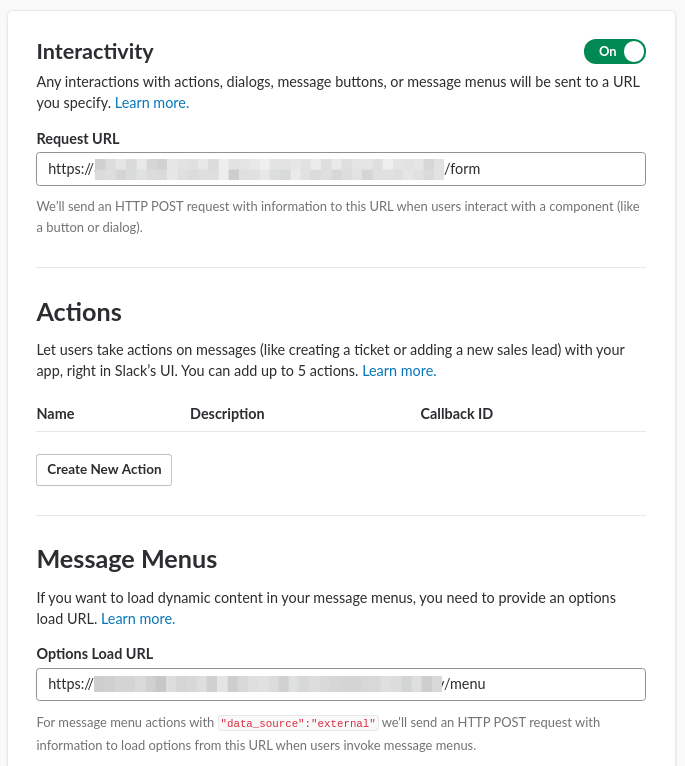
edit botconfig.py and set ENABLE_CALLBACK to False
- update environment by issuing:
zappa update dev
{
"dbport" : "3306",
"slack_client_secret" : "xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx",
"igwsub1" : "subnet-xxxxxxxa",
"igwsub2" : "subnet-xxxxxxxb",
"s3bucket" : "wctf-vpc-rds-vpc-xxxxxxxx",
"profile_name" : "myprofile",
"connection_type" : "mysql_rds",
"slack_client_id" : "000000000000.000000000000",
"sql_password" : "xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx",
"sglambda" : "sg-xxxxxxxx",
"log_level" : "DEBUG",
"slack_verification_token" : "xxxxxxxxxxxxxxxxxxxxxxxx",
"master_password" : "xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx",
"sql_user" : "normal_user",
"sgrdsinternal" : "sg-xxxxxxxa",
"sgrdsexternal" : "sg-xxxxxxxb",
"vpc" : "vpc-xxxxxxxx",
"slack_signing_secret" : "xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx",
"dbinstance" : "xxxxxxxxxxxxxxx",
"base_name" : "wctf-vpc-rds",
"exception_hook_url": "https://hooks.slack.com/services/TXXXXXXXX/BXXXXXXXX/xxxxxxxxxxxxxxxxxxxxxxxx",
"endpoint_address" : "xxxxxxxxxxxxxxx.bbbbbbbbbbbb.us-east-2.rds.amazonaws.com",
"privsub1" : "subnet-xxxxxxxa",
"privsub2" : "subnet-xxxxxxxb",
"region" : "us-east-2",
"master_user" : "master_user",
"ctftoken": "xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx",
"events": [
{
"function": "scheduled_tasks.show_countdown",
"expression": "cron(0 19 * * ? *)"
}
]
}
example ./env_setup/authdata-dev.json
{
"db_wctf" : {
"slack_authed_teams" : [
{
"team_id" : "TXXXXXXXX",
"team_json" : {
"py/object" : "sqlalchemy.ext.mutable.MutableDict",
"py/state" : {
"team_id" : "TXXXXXXXX",
"ok" : true,
"scope" : "identify,bot,commands,incoming-webhook",
"access_token" : "xoxp-xxxxxxxxxxxx-xxxxxxxxxxxx-xxxxxxxxxxxx-xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx",
"user_id" : "UXXXXXXXX",
"team_name" : "Super Awesome WCTF Team",
"bot" : {
"bot_user_id" : "UXXXXXXXX",
"bot_access_token" : "xoxb-xxxxxxxxxxxx-xxxxxxxxxxxx-xxxxxxxxxxxxxxxxxxxxxxxx"
},
"incoming_webhook" : {
"url" : "https://hooks.slack.com/services/TXXXXXXXX/xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx",
"channel_id" : "CXXXXXXXX",
"channel" : "#lambda_bot_exceptions",
"configuration_url" : "https://awesome-team-name.slack.com/services/BXXXXXXXX"
}
}
}
}
]
}
}