- A VPC network consists of subnets, routes and firewall rules
- VPC Network CIDR can be as large as /9 and doesn't require CIDR to be defined
- Subnets are regional, ie. spans across Zones, have a private RFC 1918 CIDR block of /20 and a gateway which reserves First IP address of the CIDR block
- Routes tell VM instances and the VPC network how to send traffic from an instance to destination. Without a VPC network there are no routes.
- Firewall rules controls which packets are allowed to travel to which destinations
- Firewall rules are applied based on priority. Higher integer corresponds to lower priority.
- Each VPC network has 2 implied firewall rules: viz.
- ingress deny all. Priority 65535
- egress allow all. Priority 65535
- Default ingress in default vpc
- default-allow-{icmp,rdp,ssh} from 0.0.0.0/0. Priority 65534
- default-allow-internal tcp, udp, icmp within VPC CIDR. Priority 65534
- RDP port 3389
- Default Internet Gateway ≡ 0.0.0.0/0
- External IP addresses for instances are ephemeral and are released once a instance stops.
- Static External IP Address are reserve addresses assigned to a project until released explicitly.
- SSH Connection GCE generates SSH Key and stores it in:
- By Default, add the generated key to project or instance metadata
- If account is configured with OS Login, key is stored in user account
- Alternatively, keys can be created and added to public ssh key metadata of an instance
- VPC network has internal DNS service. An instance name can be used as internal DNS Name to access the instance other than internal IP address and external IP address.
ping -c 3 mynet-eu-vm - Deleting a VPC network order
- Deletes firewall rules
- Deletes Routes
- Deletes Network
- Auto-mode network create subnets in each region automatically while custom starts with no subnets
- Access to instances with external ip addresses is only controlled by the ICMP firewall rules
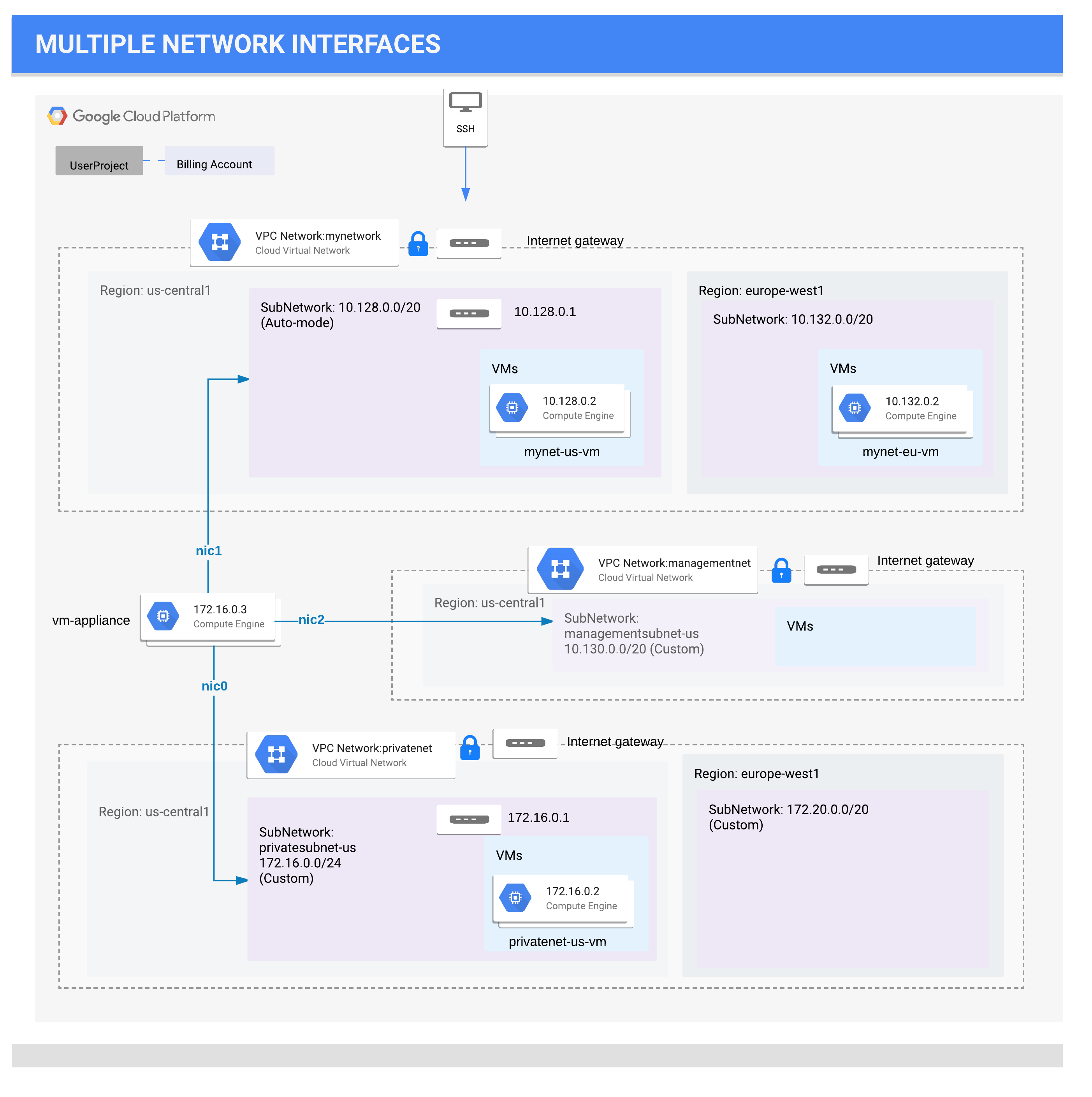
- An instance can have Multiple Network Interfaces (NIC) based on instance type (upto 8 NIC) which enables connections to multiple VPC networks based on configuration
- VMs with multiple network interface controllers (NICs) can't(?) be part of subnets with overlapping CIDR
- Internal DNS query for instance hostname resolves to the primary interface (nic0) of the instance
- NICs get route to for the subnet it is in. In addition, the instance gets a single default route that is associated with the primary interface eth0.
- Unless manually configured otherwise, any traffic leaving an instance for any destination other than a directly connected subnet will leave the instance via the default route on eth0.
- Instance Creation: Networks use network tags to identify which VM instances are subject to certain firewall rules and network routes. Later in this lab, you create a firewall rule to allow HTTP access for VM instances with the web-server tag. Alternatively, you could check the Allow HTTP traffic checkbox, which would tag this instance as http-server and create the tagged firewall rule for tcp:80 for you.
- VM get default service account [PROJECT_NUMBER]-compute@developer.gserviceaccount.com.
- 2 type of Service Accounts:
- User-managed service accounts
- Google-managed service accounts ([PROJECT_NUMBER]-compute@developer.gserviceaccount.com) with Cloud IAM project editor role.
- VM's Default Service Account doesn't have Network Admin Role and thus can't affect firewall and SSL certificates
- 2 type of Service Accounts:
- To activate a service account: Create a service account -> Assign role eg. Compute Security Admin -> Create Key -> Download json and rename to credentials.json ->
gcloud auth activate-service-account --key-file credentials.json
- Network Admin: Permissions to create, modify, and delete networking resources, except for firewall rules and SSL certificates. Provide listing of firewall resources
- Security Admin: Permissions to create, modify, and delete firewall rules and SSL certificates
- Use
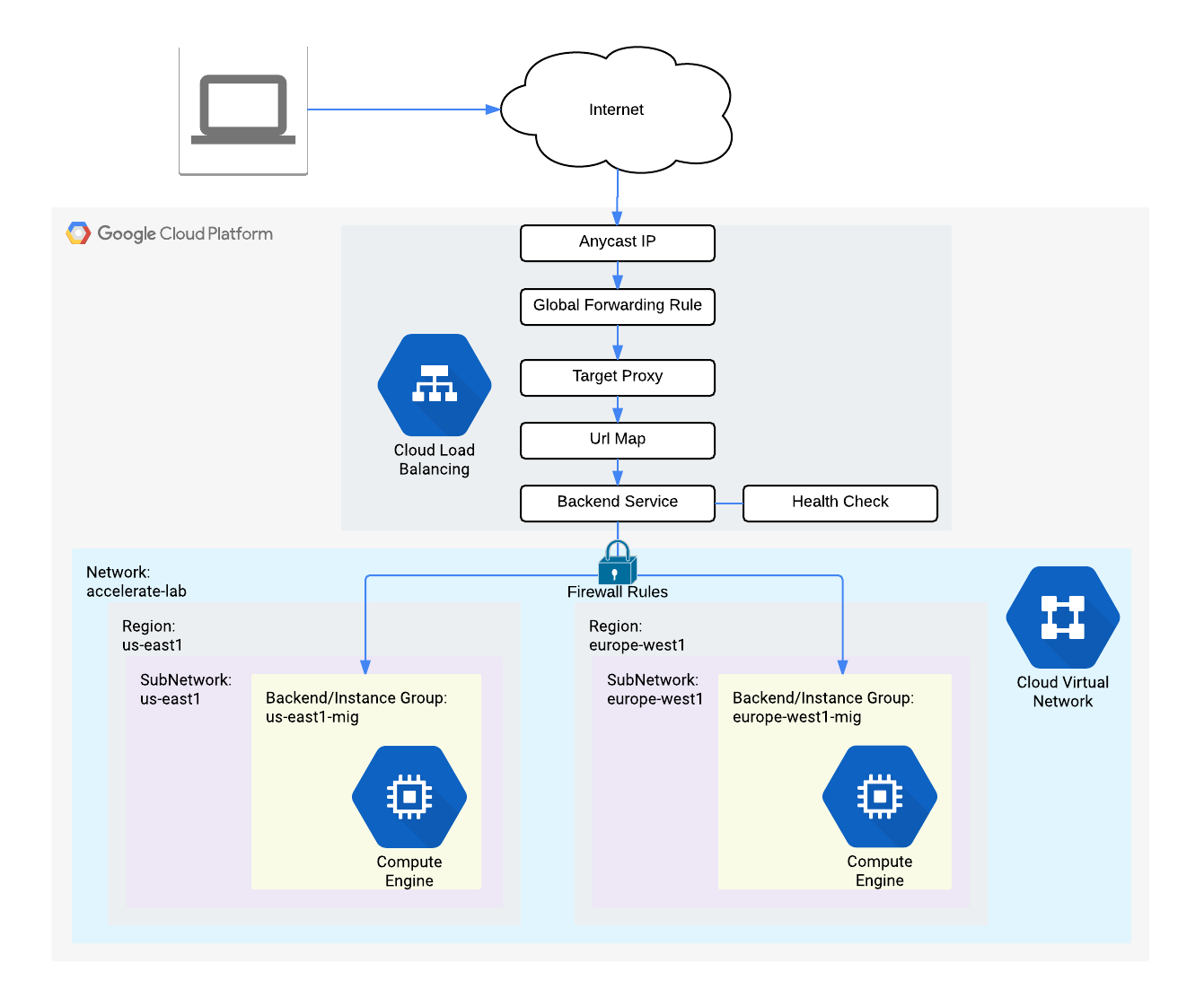
siegeto stress test network load balancing - GCP implements HTTP(S) Loadbalancers at edge location aka. point of presence (POP)
- Cloud Armor provides IP whitelisting/blacklisting to filter traffic to LBs.
- Healthcheck probes to loadbalanced instances comes from 130.211.0.0/22 and 35.191.0.0/16
- Managed Instance Groups uses Instance Templates to create group of identical instances
- Instance Groups aws-aka. AutoScaling Groups use instance templates to to launch identical VMs based on load. They can be created for a region or zone
- startup-script-url awk-aka. user-data
- The Hostname and Server Location identifies where the HTTP Load Balancer sends traffic
Command structure gcloud service [subservice(s)] action [name] --options. subservices are mentioned in plural form
# get help
gcloud help compute instances create
# setup gcloud
gcloud init
gcloud init --project qwiklabs-gcp-00-190ccec93406
# active account name
gcloud auth list
# list the project ID
gcloud config list project
# Project Quota
gcloud compute project-info describe --project <project-id>
# check whether the server is ready for an RDP connection
# create a custom vpc network
gcloud compute --project=qwiklabs-gcp-00-cf97919dc2f9 networks create managementnet --subnet-mode=custom
# create a subnet in custom mode vpc network, subnet is regional defined by a CIDR in a VPC
gcloud compute networks subnets create managementsubnet-us --network=managementnet --region=us-central1 --range=10.130.0.0/20
# Add firewall rules to network, a firewall rule for a network is defined as source, direction, action, rule, priority
gcloud compute firewall-rules create managementnet-allow-icmp-ssh-rdp --direction=INGRESS --priority=1000 --network=managementnet --action=ALLOW --rules=tcp:22,tcp:3389,icmp --source-ranges=0.0.0.0/0
# create an instance in a network, machine-type, zone and subnet is important
gcloud compute instances create privatenet-us-vm --zone=us-central1-c --machine-type=n1-standard-1 --subnet=managementsubnet-us
# list routes of an instance
ip route
# tag an instance
gcloud compute instances add-tags blue --tags=web-server
# create a firewall rule to target an instance
gcloud compute firewall-rules create allow-http-web-server --allow=tcp:80,icmp --network default --priority 1000 --source-ranges 0.0.0.0/0 --direction INGRESS --target-tags web-server
# create healthcheck firewall rules
gcloud compute firewall-rules create default-allow-health-check --direction INGRESS --allow tcp --source-ranges=130.211.0.0/22,35.191.0.0/16 --target-tags http-server --network default
# create an instance template
gcloud compute instance-templates create us-east1-template --metadata startup-script-url=gs://cloud-training/gcpnet/httplb/startup.sh --network default --tags http-server
# create an instance group
gcloud compute instance-groups managed create us-east1-mig --template us-east1-template --size 1 --region us-east1
# set autoscaling in instance group
gcloud compute instance-groups managed set-autoscaling us-east1-mig --min-num-replicas 1 --max-num-replicas 5 --cool-down-period 45 --target-cpu-utilization 0.80
# enable osLogin to an instance
gcloud compute instances add-metadata instance-name --metadata enable-oslogin=TRUE
# ssh osLogin to an instance
gcloud compute ssh instance-name
- GCP: Cloud based products and services = Infra + Platform + Software = Compute + Storage + Networking + BigData + Machine Learning = CSNBiM + G Suite + G Devices + Stackdriver, etc
- Cloud Computing: On-Demand + Broad Network Access + Resource Pooling + Elasticity + Measured Services (Pay per use)
- History
<->Future: On Perm->Virtual->Serverless - Compute: (Managed Infra)
<-Compute Engine (IaaS)-Kubernetes Engine (Hybrid)-App Engine (PaaS)-Cloud Functions (Serverless)-Managed Services (Automated Elastic Resource)->(Dynamic Infra) - Global -> Multi Region -> Region (Each region separated by 160KM/100Miles) -> Zones (Think of them as separate facilities)
- Environmental Concerns - 0 Carbon Emission and 100% Renewable Energy
- Encryption at Rest, In Transition, DDoS, Google Frontend Test for Vulnerabilities
- Built on OpenAPIs like kubernetes, Hadoop, Apache HBase which are opensource
- Encryption at Rest, In Transition, DDoS, Google Frontend Test for Vulnerabilities
- Project Number (Auto-generated can't change), Project ID auto-generated, can be changed at time of creation only, Project Name user provided, NOT Globally unique
- Project in gshell can be changed by
gcloud config set project <PROJECT_ID>, current project is set in$DEVSHELL_PROJECT_IDenvvariablegcloud config listgcloud config core list
- Compute Resources, IAM, least privilige, raw compute to managed services, access using web console/cli-tools(G Cloud SDK preinstalled, gsutil, bq, gcloud)/iOS/Android/APIs
- Resources are allocated based on PROJECTS which can be grouped under FOLDERS
- Organization Nodes -> Folders (It is must to have org node to create folders) -> Projects -> GCP Resources
- Policies are inherited from top (eg. Org node), with more generous of them taking precedence (consider it binary OR of access level)
- Org node can be create by using Cloud Identity
- [?] Billing is per project basis
- who (person|group|application) -> can do what (previliges|actions)-> on which resources (GCP Services)?
- Organization -= Folders -= Projects -= Members -= Roles -= Resources -= Products -= G Suit Super Admins
- Policy is set on resource comprises of Roles and Role Members
- Policies|Permission are inherited top to down and is union of all policies in the hierarchy with less restrictive policy overriding restrictive policy
-
- Follow principle of least privilege
Global System (Internet) -> Points of Presence (Edge Locations and CDNs)
-> Global (Private Global Network)
-> Multi Region
-> Region (Each region separated by 160KM/100Miles)
-> Zones (Think of them as separate facilities)
-> Datacenters
-> Rack
-> Physical Server
-> vCPU (2vCPU = 1 core)
- Organization Nodes
->Folders (It is must to have org node to create folders)->Projects->GCP Resources- Policies are inherited from top (eg. Org node), with more generous of them taking precedence (consider it binary OR of access level)
- Org node can be create by using Cloud Identity
- Billing is per project basis
- Compute Resources, IAM, least privilege, raw compute to managed services, access using web console/cli-tools/iOS/Android/APIs
- Resources are allocated based on PROJECTS which can be grouped under FOLDERS
- Normal Network: Routes via internet to edge location closets to destination, available at lower price
- Google: Routes so traffic enters from @edge closest to source
- Single global IP address and Loadbalancers worldwide
- AWS only supports Normal network
- Network Traffic: Ingress Free, Egress charged per GB
- egress to a gcp service in a region is sometimes free
- Services: Usage, Provisioned
- Discounts: Pay by second, Sustained Use discount, Customize compute resources or use out of box
- Separation of duties
- Encryption at rest, in transition even within gcp network, DDoS, Google Frontend Test for Vulnerabilities
- Recommends: Distrust the network
- Sample Architectures
- API Hosting
- Jenkins on Kubernetes
- Live Streaming
- Log Processing
- Shopping Cart Analysis
- Network Map
- Regions Map
- Apigee API Platform
- App Engine (GAE)
- Using Stackdriver Logging in App Engine apps App Engine Documentation
- Reading and Writing Application Logs App Engine standard environment for Python
- BeyondCorp
- BigQuery
- Using the bq Command-Line Tool BigQuery
- Bigtable - Scalable NoSQL Database Service Cloud Bigtable
- Cloud Billing API
- Billing Access Docs
- GCP Docs on Budgets and Billing Alerts
- GCP Docs on Billing Export to BigQuery
- BigQuery Under the Hood
- Dataflow Shuffle
- GPUs in Kubernetes Engine now available in beta
- Cloud CDN
- Google Certified Professional Cloud Architect
- Compute Engine (GCE)
- Service Accounts and Scopes
- Service Accounts Compute Engine Documentation
- Viewing Audit Logs Compute Engine Documentation
- Local SSD
- GCE Instance Statuses
- Creating Instances
- Preemptible Instances
- Creating a VM Instance with a Custom Machine Type Compute Engine Documentation
- Static IPs
- Global Load Balancing
- Machine Types Compute Engine Documentation
- Regions and Zones Docs
- Changing the Default Region or Zone Compute Engine Documentation
- Startup Scripts
- Instance Metadata Reference
- Storing and Retrieving Instance Metadata
- Long-Polling for Metadata Changes
- Cloud VPN
- Network Pricing
- Resource Quotas (Soft Limits)
- Container Builder
- Container Registry (GCR)
- Cloud Data Studio
- Cloud Dataflow - Stream & Batch Data Processing Cloud Dataflow
- Cloud Datalab
- Cloud Dataprep
- Cloud Dataproc - Cloud-native Apache Hadoop & Apache Spark Cloud Dataproc
- Cloud Datastore
- Cloud Datastore Queries
- Stackdriver Debugger
- Cloud Deployment Manager
- Dialogflow
- Cloud Data Loss Prevention (DLP) API
- Cloud DNS
- Main Documentation
- Geography and Regions Documentation
- Tutorials
- Cloud Endpoints
- Cloud Endpoints gRPC Transcoding
- Cloud Endpoints Architecture
- Stackdriver Error Reporting
- Cloud Functions (GCF)
- Cloud Genomics
- Cloud Identity and Access Management (IAM)
- Granting Roles to Service Accounts
- Overview
- Hierarchical Access Control
- Service Accounts
- Understanding Roles
- Understanding Service Accounts
- Cloud Identity-Aware Proxy (IAP)
- Cloud Interconnect
- Dedicated Interconnect
- CDN Interconnect
- Cloud Internet of Things (IoT) Core
- Cloud Job Discovery
- Cloud Key Management Service (KMS)
- Kubernetes Engine (GKE)
- Cluster Architecture Kubernetes Engine
- DaemonSet Kubernetes Engine
- Deployment Kubernetes Engine
- Pod Kubernetes Engine
- StatefulSet Kubernetes Engine
- Logging Kubernetes Engine
- Resizing a Cluster Kubernetes Engine
- Cloud Load Balancing (CLB)
- Stackdriver Logging
- Configuring the Agent Stackdriver Logging
- List of Logs Sent by Agent (by Default)
- Installing Stackdriver Agent
- Cloud Audit Logging Stackdriver Logging
- Google Cloud Platform Marketplace Solutions
- What is Google Cloud Platform Marketplace? GCP Marketplace
- Cloud Machine Learning Engine
- Stackdriver Monitoring
- Agent-Visible Metrics
- Hypervisor-Visible Metrics
- Cloud Natural Language API
- Persistent Disk
- Prediction API (Deprecated)
- Pricing Calculator
- Cloud Pub/Sub
- Resource Manager
- Resource Manager Hierarchy
- Cloud Router
- Configurations in gcloud
- Initializing Cloud SDK Cloud SDK Documentation
- Properties in gcloud
- Overview Doc for gcloud
- Syntax of gcloud
- gcloud compute instances create Cloud SDK
- gcloud container clusters resize Cloud SDK
- Filters in gcloud
- Security Key Enforcement
- Cloud Security Scanner
- GCP Security Overview
- GCP Security Design
- Best Practices for Operating Containers Architectures
- Big Data Lifecycle
- Cloud Source Repositories
- Cloud Spanner
- Cloud Spanner Instance Configurations and Nodes
- Cloud Speech API
- Cloud SQL
- Google Stackdriver
- Stackdriver Chargeable Resources
- Cloud Storage
- Making Data Public
- Bucket Locations
- config - Obtain credentials and create configuration file Cloud Storage
- Storage Classes Cloud Storage
- Cloud Storage Pricing Cloud Storage
- Storage Transfer Service
- Stackdriver Trace
- Data Transfer Appliance
- Cloud Translation API
- Cloud Video Intelligence API
- Cloud Vision API
- Virtual Private Cloud (VPC)
- GCP Blog
- Codelabs
- Free Trial Account
- Nginx | Marketplace - Google Cloud Platform
- NGINX Plus | Marketplace - Google Cloud Platform
- Using OAuth 2.0 for Server to Server Applications Google Identity Platform Google Developers
- My Coke Rewards Case Study
- Google Domains
- Google's Tools
- Firebase DBs
- Test Lab for Android
- GCP Slack
- Course Resources GitHub Link
- GCP Qwiklabs
- Jupyter Notebook
- kubectl Cheat Sheet - Kubernetes
- Viewing Pods and Nodes - Kubernetes
- Site Reliability Engineering (SRE) Book
- Summary article on SRE Principles
- A GCP flowchart a day – Google Cloud Platform - Community – Medium
- How to log your application on Google Compute Engine
- Lab Commands List
- Interview with Lynn Langit
- Cloud Identity
- Data Wrangling vs ETL
- Google’s Cloud Launcher is now the GCP Marketplace, adds container-based applications | TechCrunch
- Google Cloud Platform - NGINX
- Security by Design Principles - OWASP
- GCP YouTube Channel
- Data Center Tour #1
- Data Center Tour #2 (360 Degree)
- White Papers
- Sample Case Study
- SRE Book, Loadbalancing, Data Processing Pipelines, MTTR (mean time to repair), MTBF (mean time between failure) - Testing for reliability - Release Engineering
- Cloud Architect Certification Guide
- Loadbalancing
- Cloud Identity
- Data Transfer
- GCSFuse
[...document.getElementsByClassName('course-viewer--sidebar-course'), ...document.getElementsByClassName('course-viewer--resource-list')]
.map((n) => {
return [...n.querySelectorAll('h3'), ...n.querySelectorAll('a')].map((n) => {
return (n.text ? '- [' : '### ') + (n.text||n.innerText || '').replace(/\s+/gm, ' ').trim() + (n.text ? '](' + n.href +')' : '')
})
})
.reduce((acc, n) => acc.concat(n), [])
.join("\n")