Digital Ocean Kubernetes Challenge repo, focusing on automation via GitHub Actions.
This repo contains Helm values and Github actions for the installation of the Kyverno.
Initial installation of the Kyverno is triggered by the manual pipeline. Any changes to the Helm values will trigger Helm upgrade.
Policies located in the Policies directory and will be updated automatically if any policy has changed.
Main branch is write protected and all changes should be done through the Pull Request. Each PR is linted and validated.
- DOKS cluster
- Digital Ocean Kubernetes Cluster Created
- DOCR registry
- Digital Ocean Container Registry Created and attached to our cluster
- DO Personal access token
- Digital Ocean PAT used for getting kubeconfig
- GitHub Personal access token
- GitHub Personal Access Token used for creating automatic releases
This repo follows Conventional Commits. All commits are validated for following this convention.
Steps required for initial deployment of Kyverno:
- Set up Github secret with DO personal access token in variable
DO_K8S_TOKEN - Set up Github secret with DO k8s cluster name in variable
DO_K8S_CLUSTER_NAME - Set up Github secret with GitHub PAT in variable
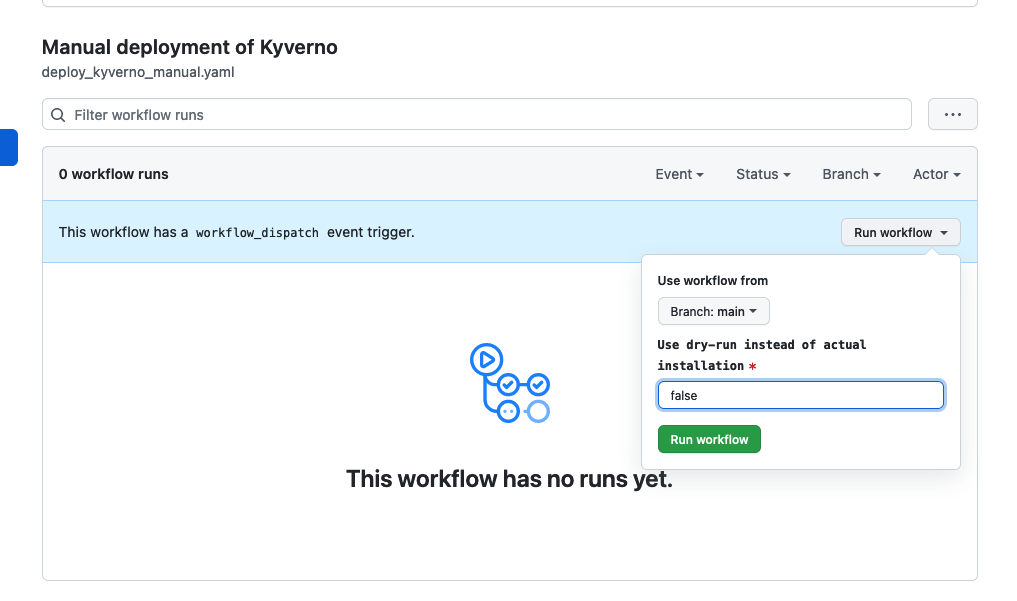
RELEASE_PAT - Trigger the manual pipeline Manual deployment of Kyverno
for the initial installation of
kyvernoHelm Chart into your Kubernetes cluster. For this, setDRY-RUNto false. This will also installkyverno-policyand apply custom policies.
- Check that pipeline finished successfully.
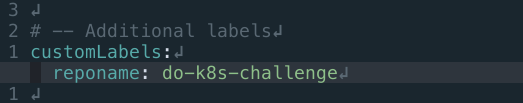
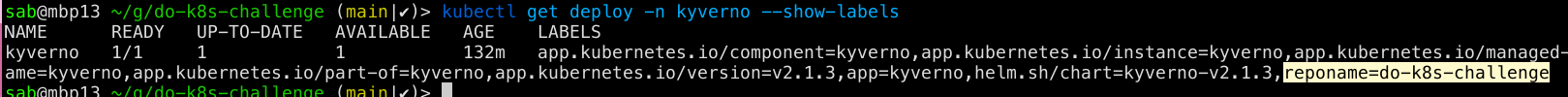
In this example, we'll modify Kyverno Helm values, adding new reponame label:
Create a new branch, push your changes and create a new Pull Request:
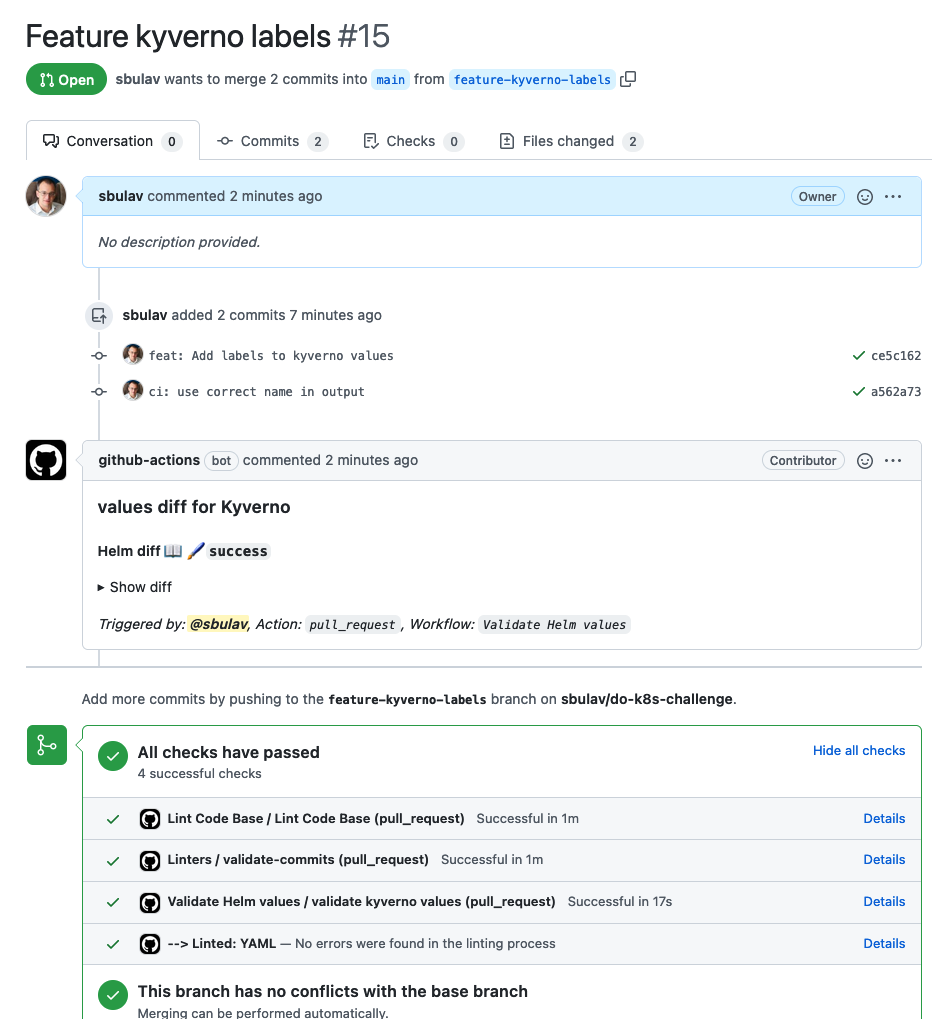
Make sure that all checks have passed. Notice that you can check helm diff
directly in PR.
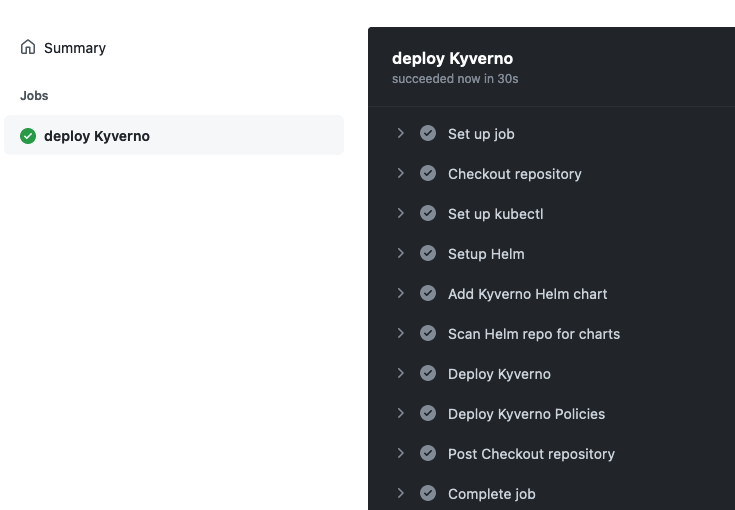
Merge the PR and notice that deployment has been triggered automatically:
After successful deployment, you'll see new repo applied to Kyverno deployment:
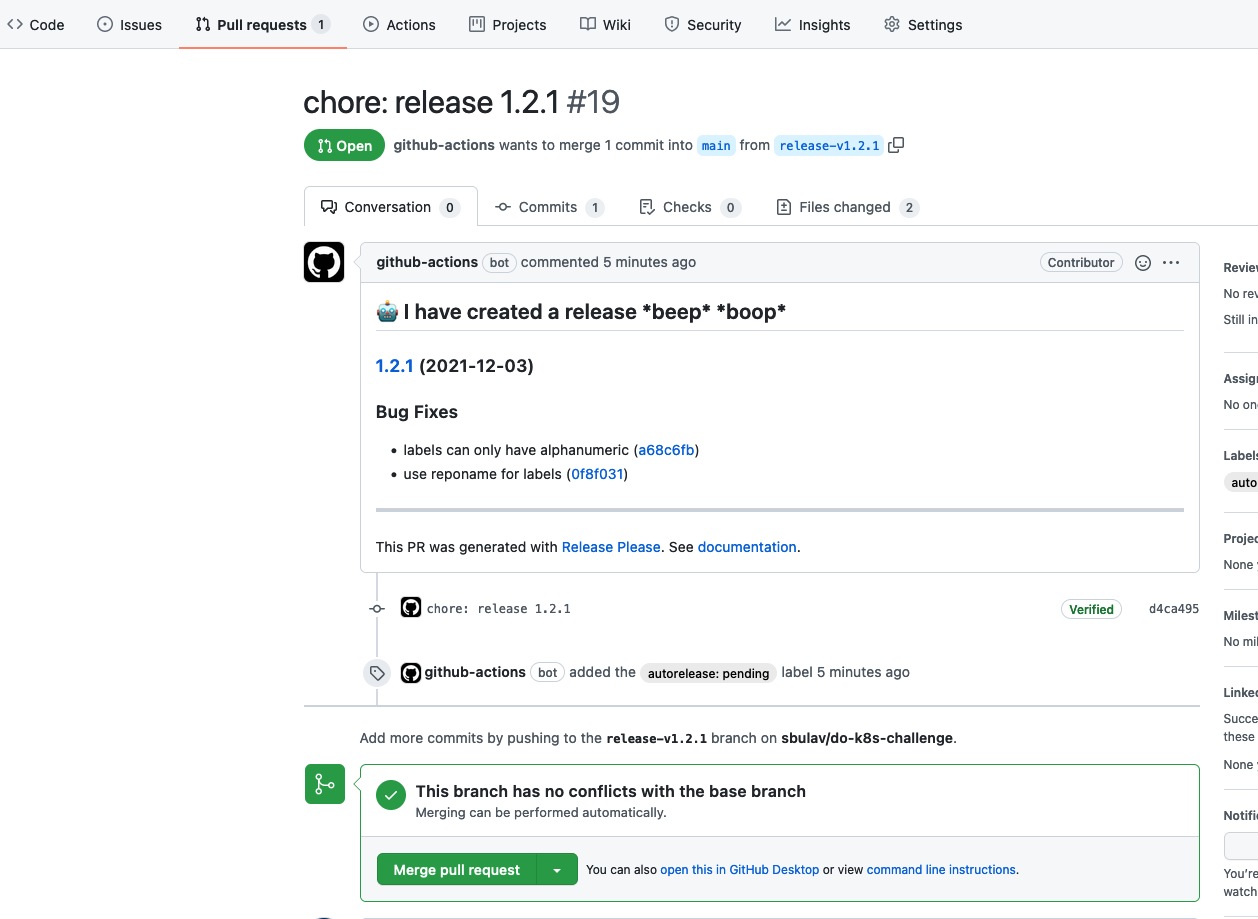
If our commits had breaking changes, features or fixes, new PR with new RELEASE will be created automatically:
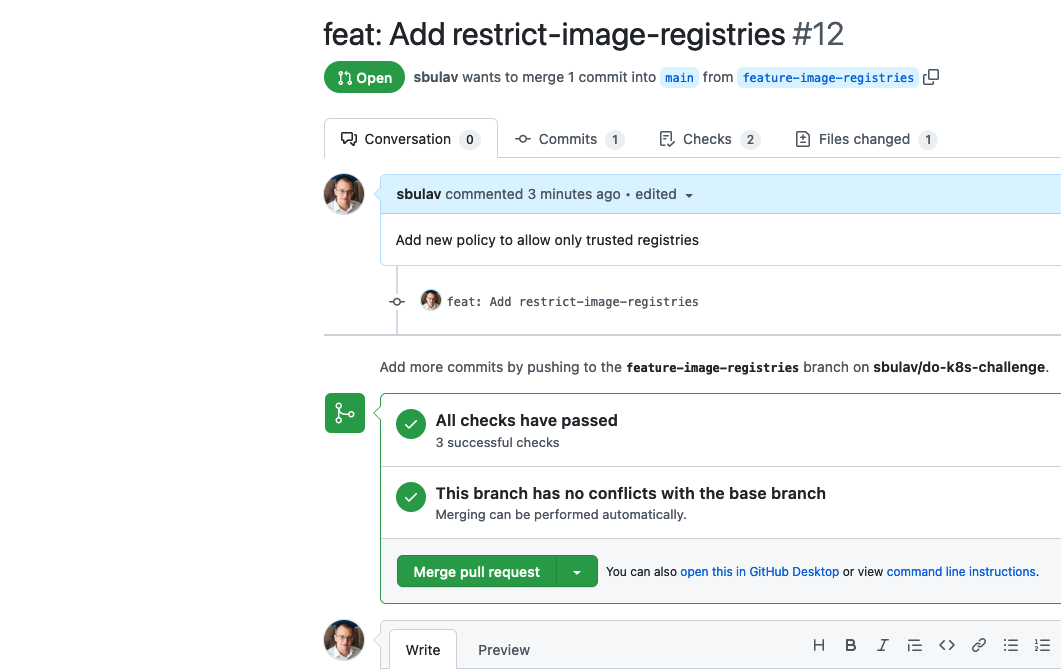
In this example, we'll add new custom Kyverno policy, allowing images only from allowed registries.
Create a new branch, push your changes and create a new Pull Request:
Make sure that all checks have passed.
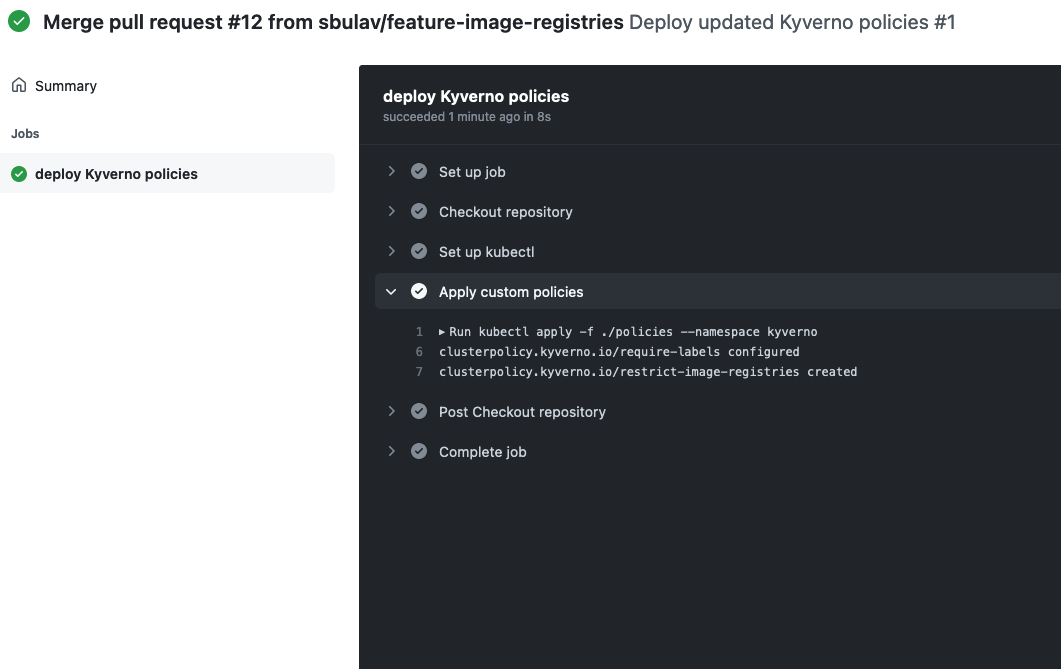
Merge the PR and notice that deployment has been triggered automatically:
Now let's push an image into our Digital Ocean Container Registry. I'll use
nginx:latest for that:
docker tag nginx:latest registry.digitalocean.com/do-k8s-challenge-cr/nginx:latest
docker push registry.digitalocean.com/do-k8s-challenge-cr/nginx:latestAfter successful deployment new Policies should enforce:
- label
app.kubernetes.io/nameis set - only images from
registry.digitalocean.comare allowed
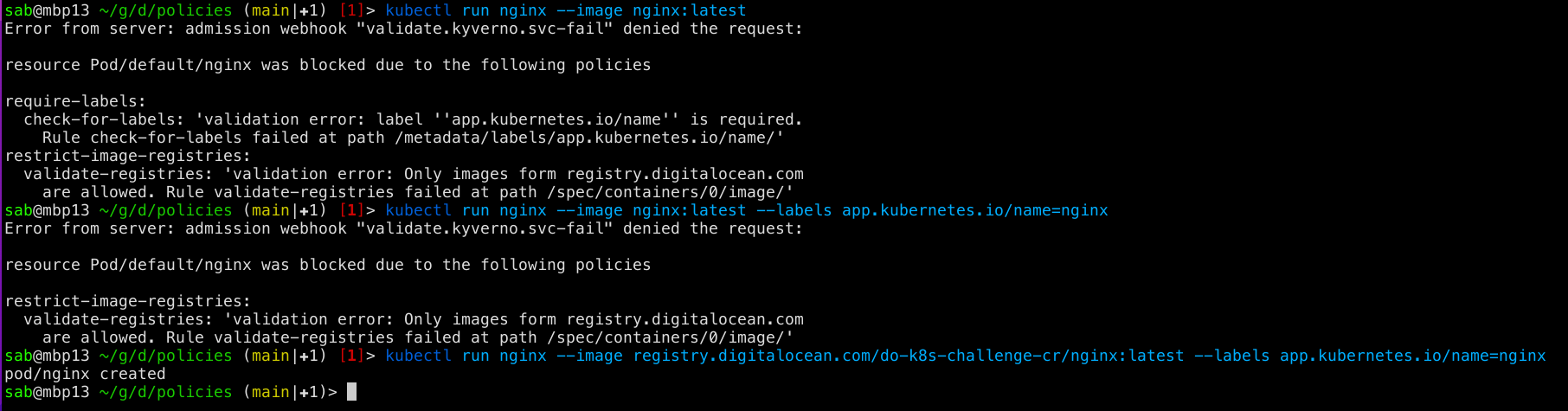
Let's try to run Pods with images from different registries:
As you can see, image from DockerHub was blocked, and label is required
for Pod creation.
After requirements were satisfied, Pod with image from
registry.digitalocean.com was created.