Terraform codes in this collection cover different hub and spoke network patterns using standard Virtual Network (Vnet) network topologies.
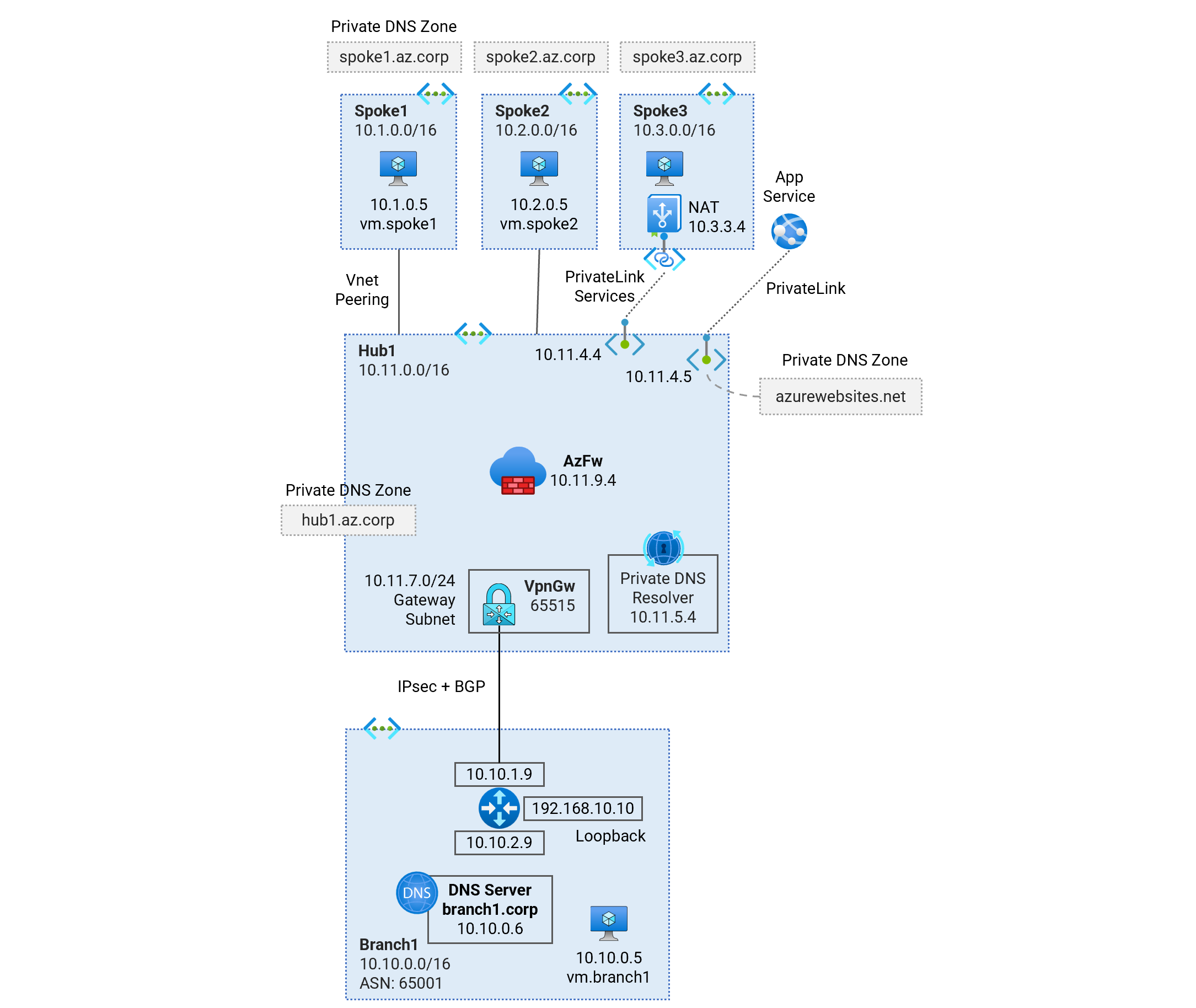
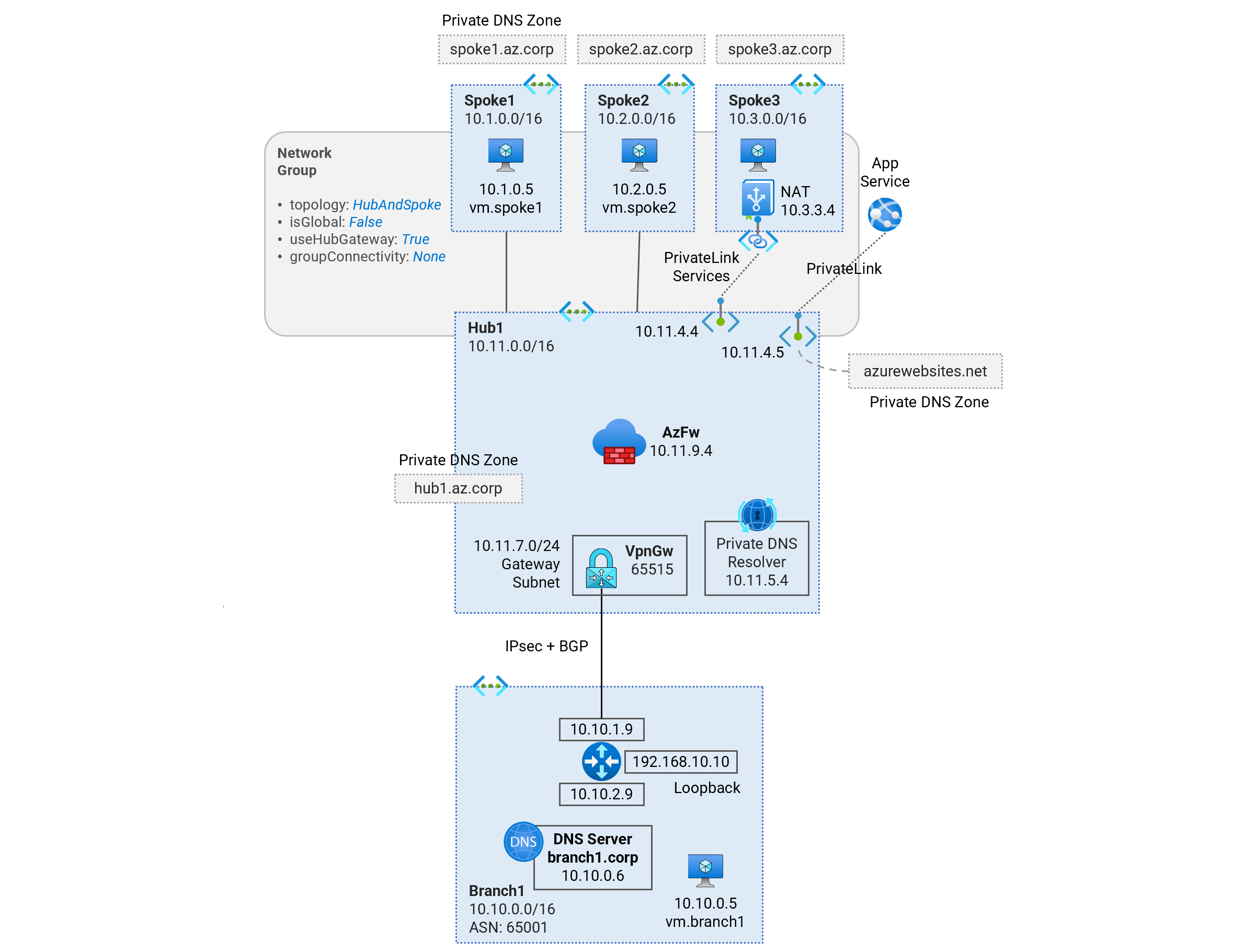
Deploy a single-region Hub and Spoke Secured Virtual Network (Vnet) topology using Azure Firewall for traffic inspection. Learn about traffic routing patterns, hybrid DNS resolution, firewall security policies, and PrivateLink Services access to IaaS, PrivateLink access to PaaS services.
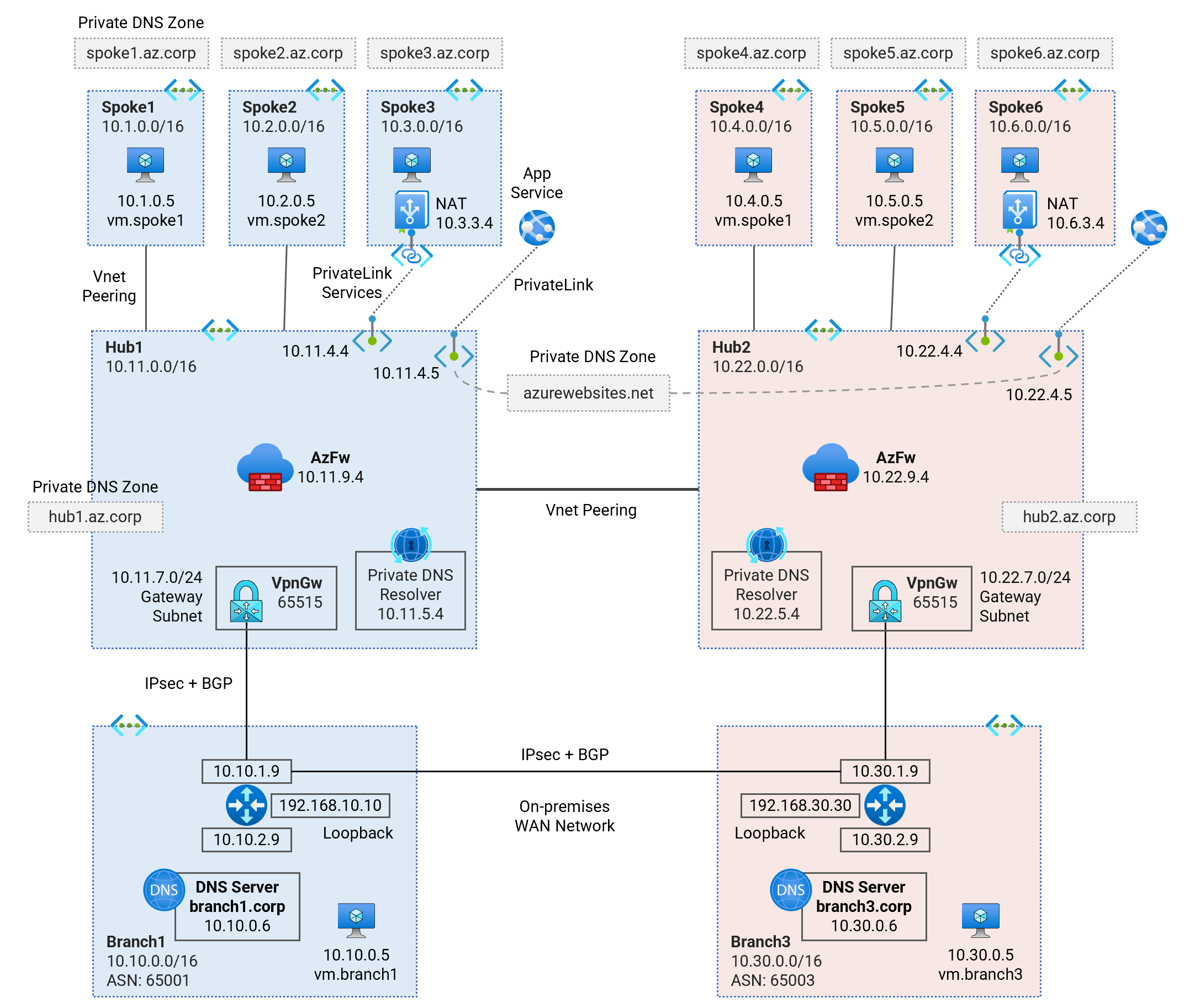
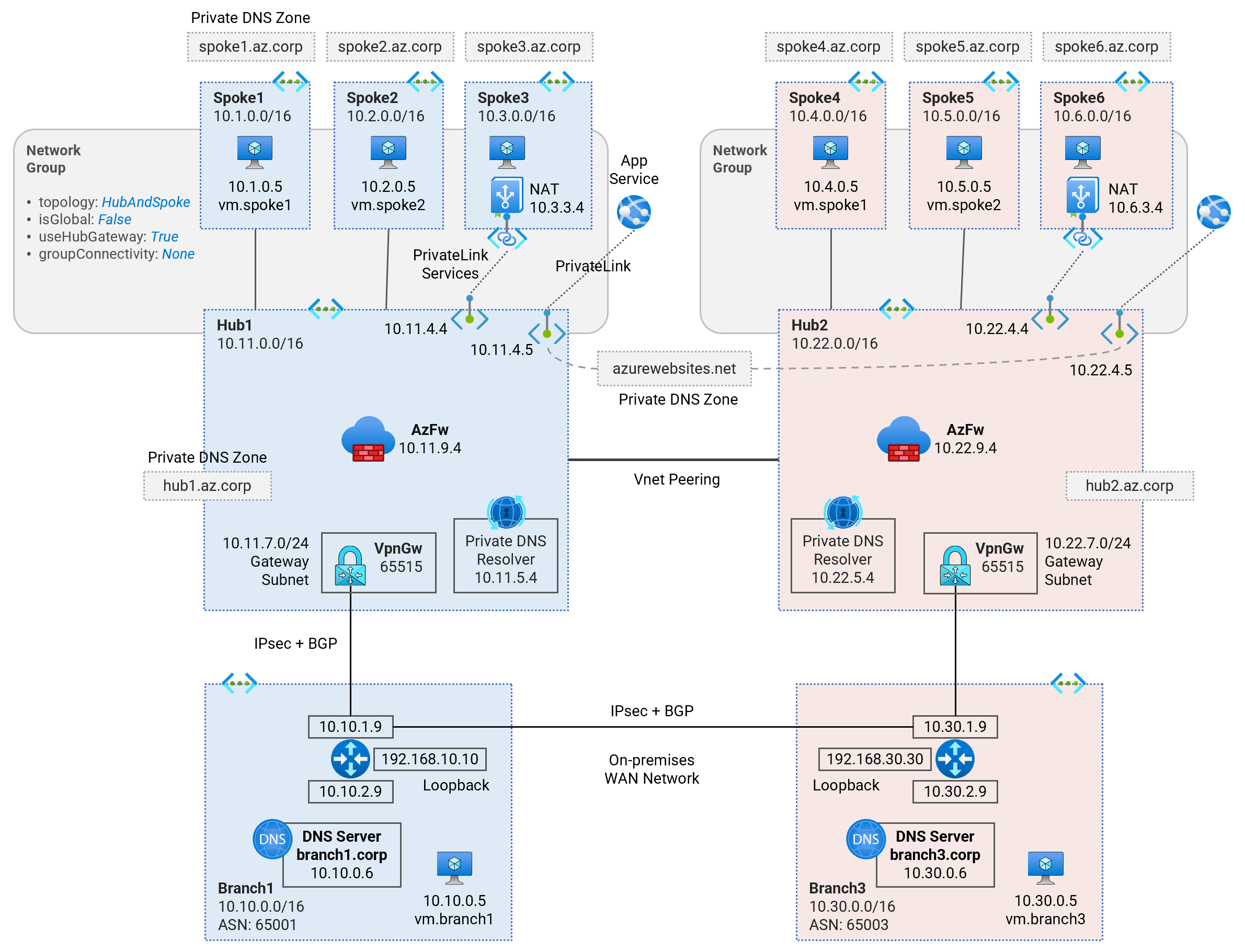
Deploy a dual-region Secured Hub and Spoke Vnet topology using Azure Firewalls for traffic inspection. Learn about multi-region traffic routing patterns, hybrid DNS resolution, firewall security policies, and PrivateLink Services access to IaaS, PrivateLink access to PaaS services.
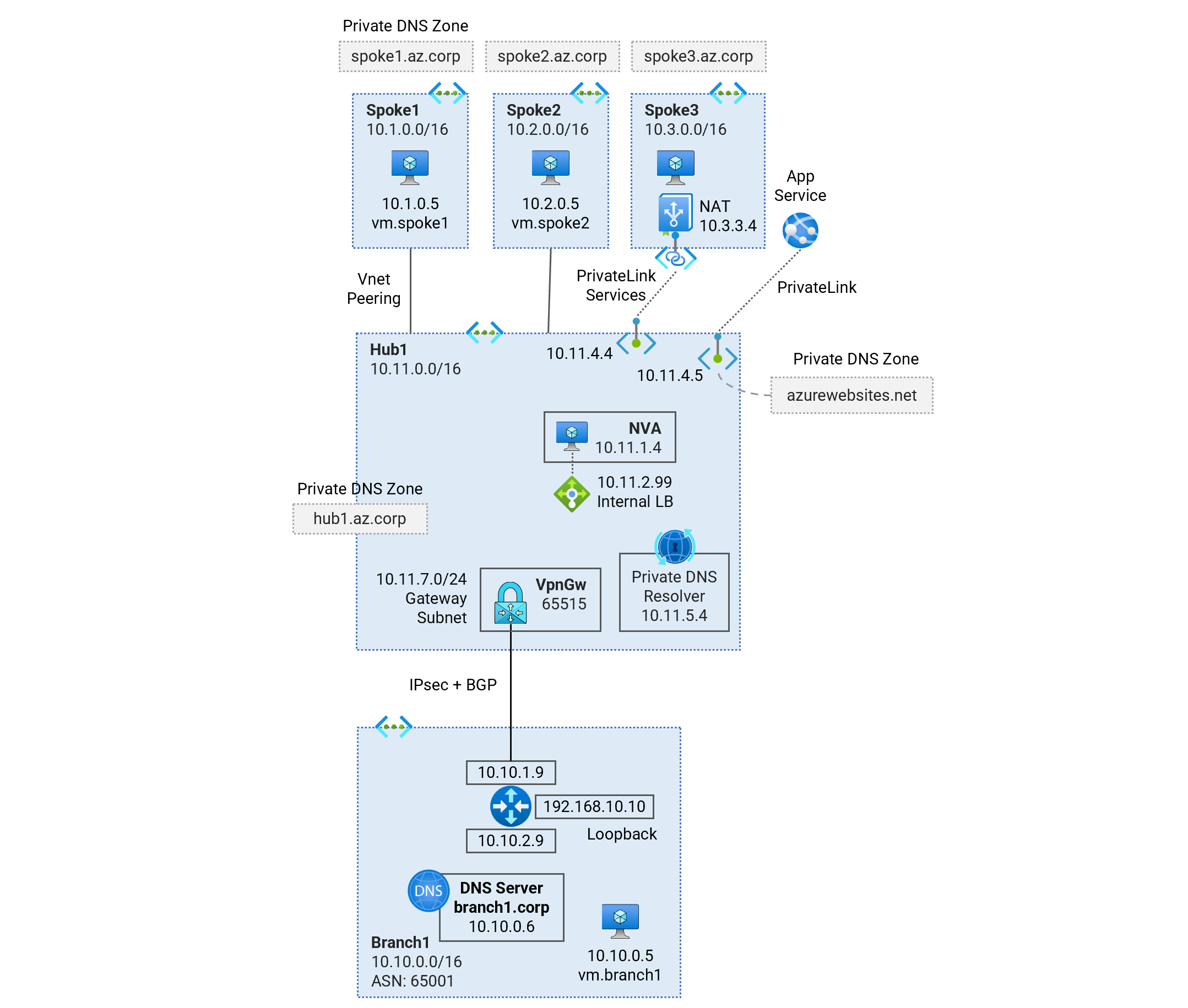
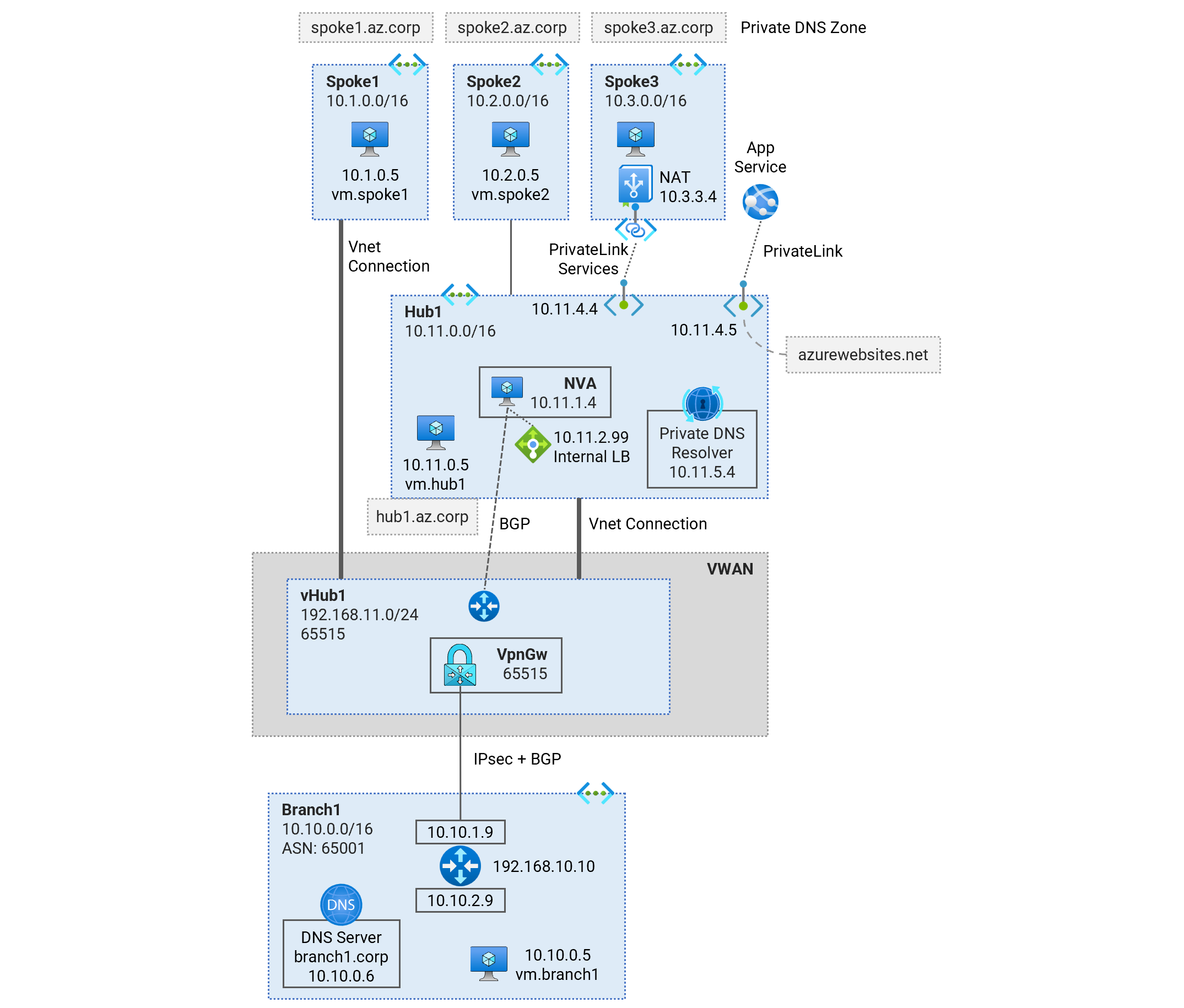
Deploy a single-region Hub and Spoke Vnet topology using Virtual Network Appliances (NVA) for traffic inspection. Learn about traffic routing patterns, hybrid DNS resolution, NVA deployment, and PrivateLink Services access to IaaS, PrivateLink access to PaaS services.
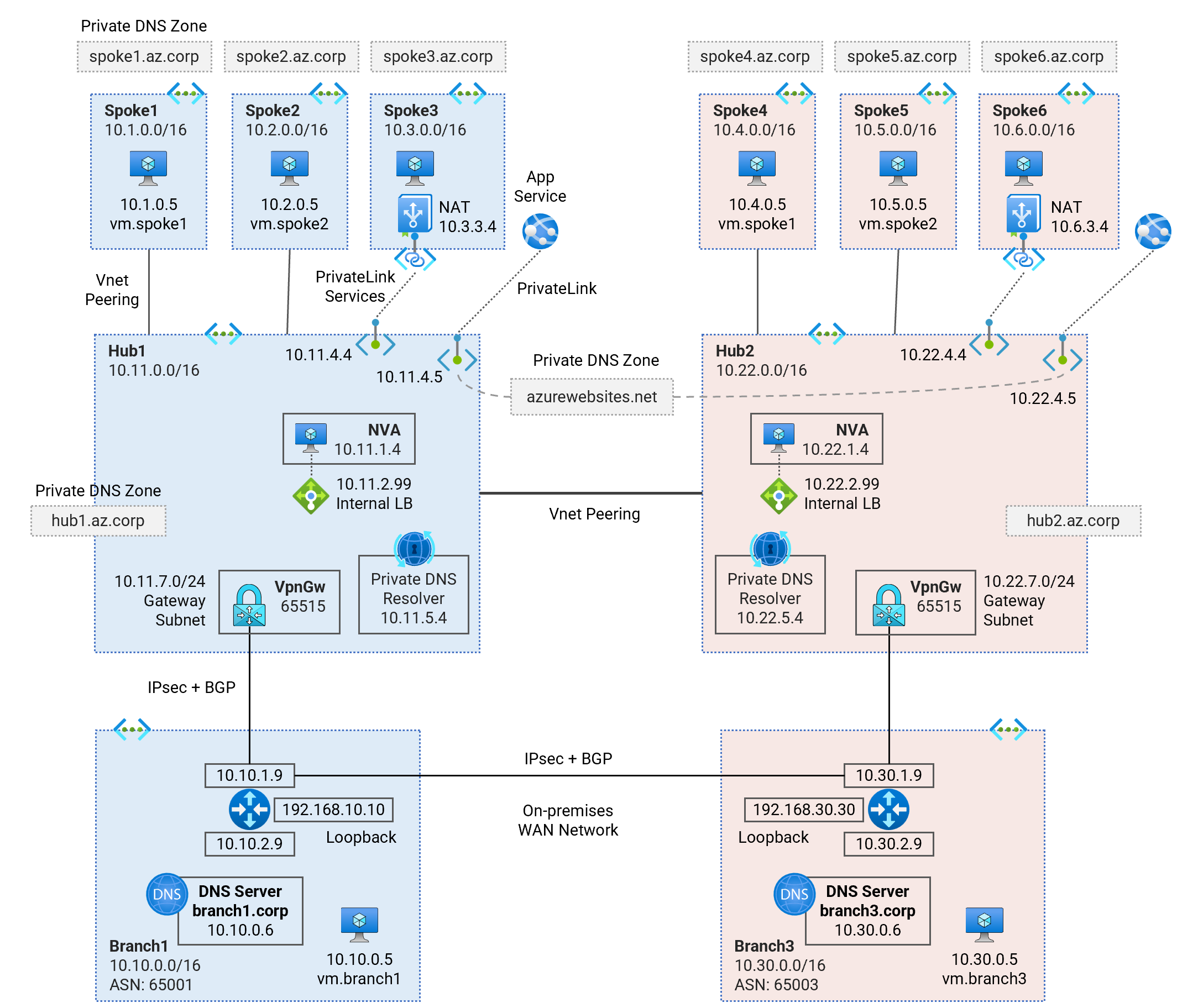
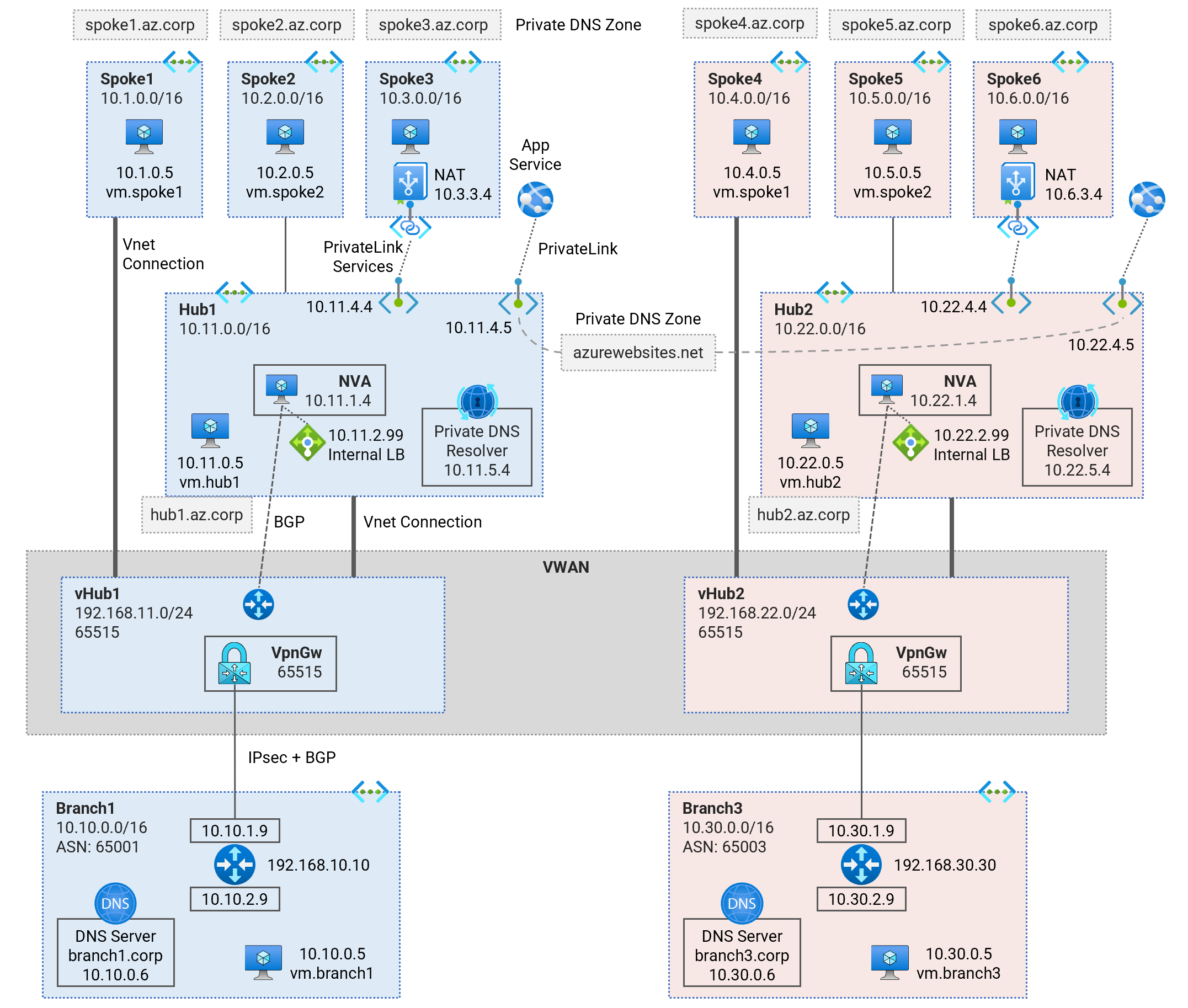
Deploy a dual-region Hub and Spoke Vnet topology using Virtual Network Appliances (NVA) for traffic inspection. Learn about multi-region traffic routing patterns, hybrid DNS resolution, NVA deployment, and PrivateLink Services access to IaaS, PrivateLink access to PaaS services.
Terraform codes in this collection cover different hub and spoke network patterns using Virtual WAN.
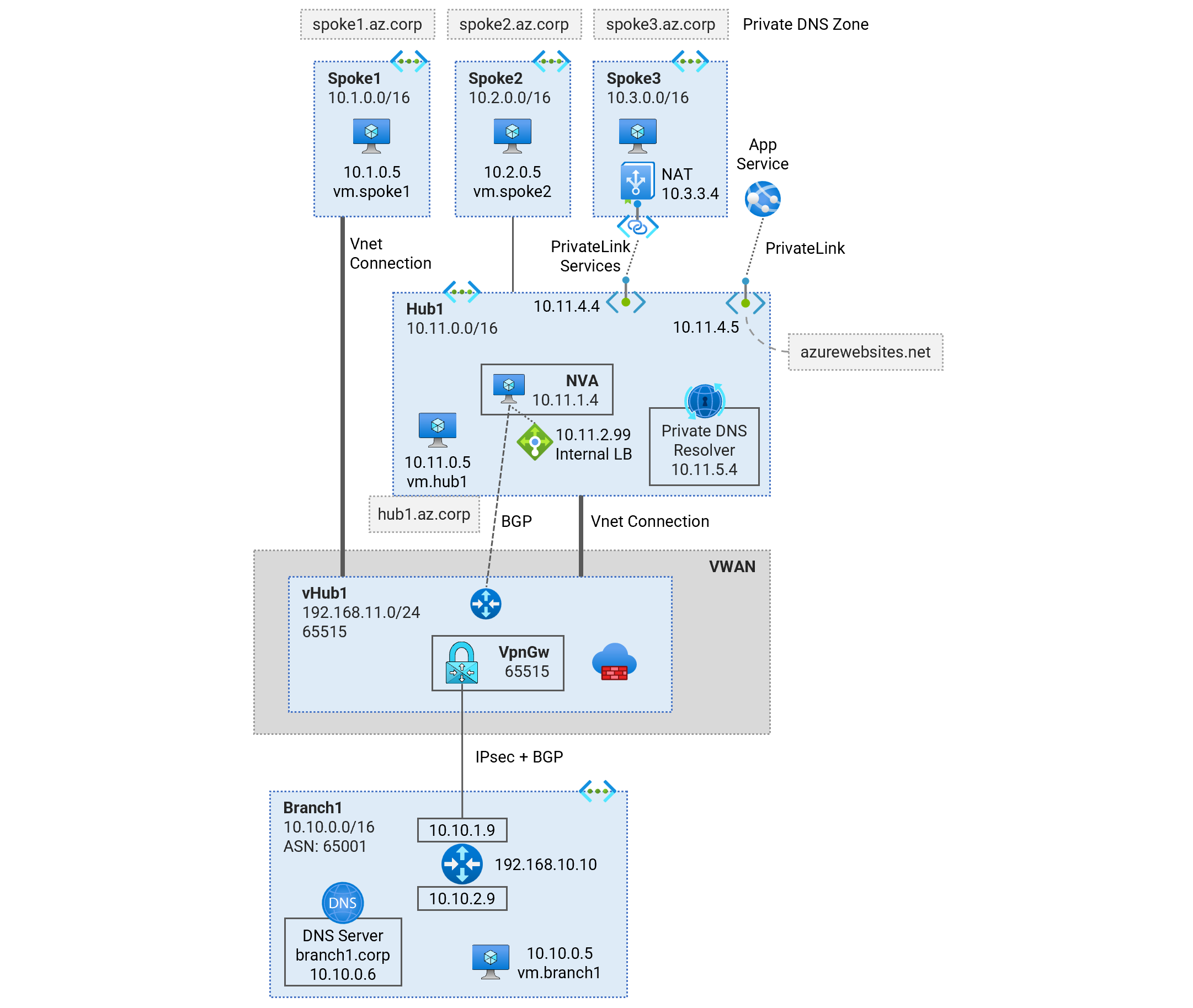
Deploy a single-region Virtual WAN (Vwan) topology to observe traffic routing patterns. Learn about traffic routing patterns, hybrid DNS resolution, connecting NVA into the virtual hub, and PrivateLink Services access to IaaS, PrivateLink access to PaaS services.
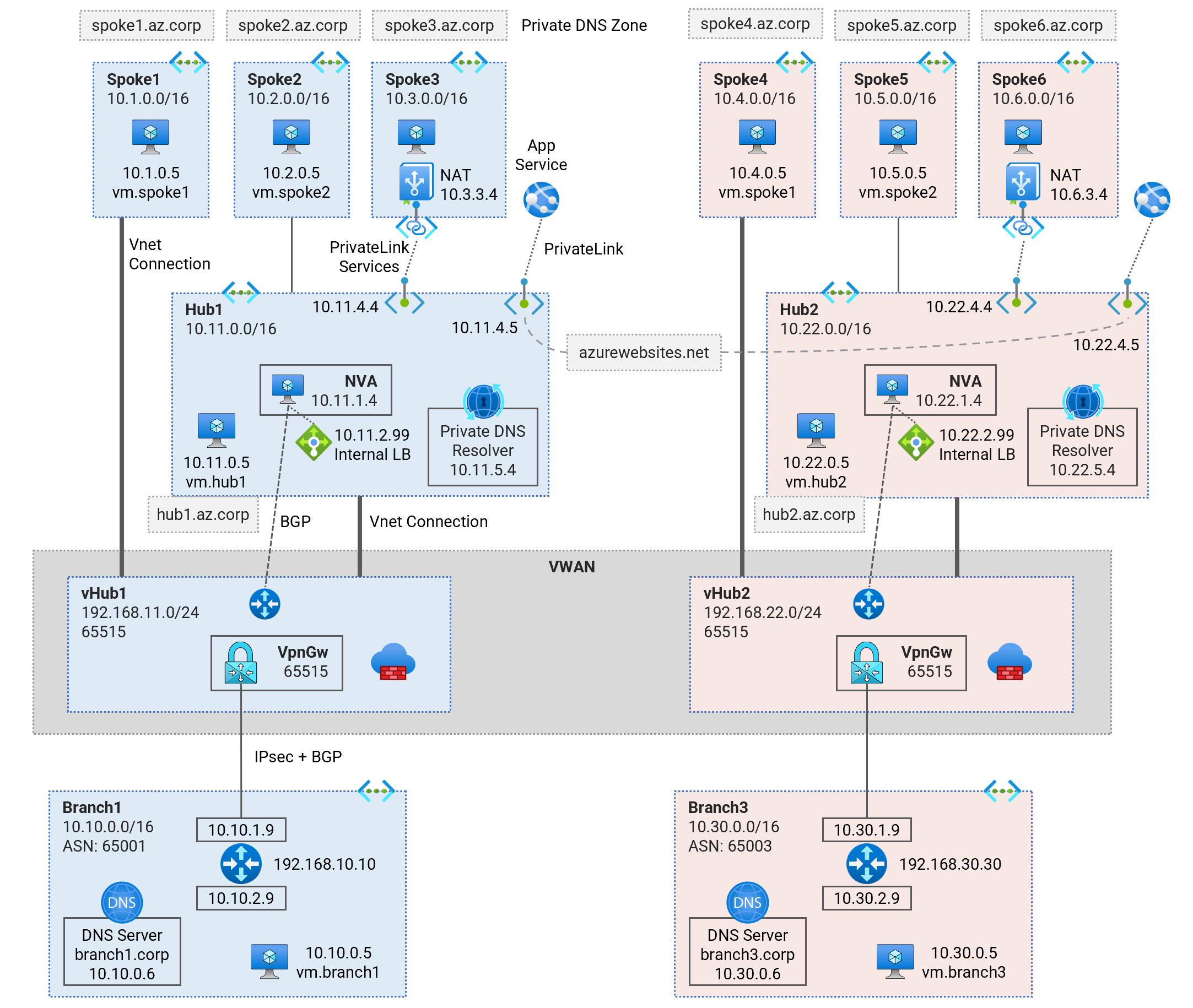
Deploy a dual-region Virtual WAN (Vwan) topology to observe traffic routing patterns. Learn about multi-region traffic routing patterns, hybrid DNS resolution, connecting NVA into the virtual hubs, and PrivateLink Services access to IaaS, PrivateLink access to PaaS services.
Deploy a single-region Secured Virtual WAN (Vwan) topology to observe traffic routing patterns. Routing Intent feature is enabled to allow traffic inspection through the Azure firewall in the virtual hub. Learn about traffic routing patterns, routing intent security policies, hybrid DNS resolution, NVA integration into the virtual hub, and PrivateLink Services access to IaaS, PrivateLink access to PaaS services.
Deploy a dual-region Secured Virtual WAN (Vwan) topology to observe traffic routing patterns. Routing Intent feature is enabled to allow traffic inspection through the Azure firewalls in the virtual hubs. Learn about multi-region traffic routing patterns, routing intent security policies, hybrid DNS resolution, connecting NVA into the virtual hubs, and PrivateLink Services access to IaaS, PrivateLink access to PaaS services.
Deploy a single-region Hub and Spoke Secured Virtual Network (Vnet) topology using the Azure Virtual Network Manager (AVNM) service. Learn about traffic routing patterns, hybrid DNS resolution, firewall security policies, and PrivateLink Services access to IaaS, PrivateLink access to PaaS services.
Deploy a dual-region Hub and Spoke Secured Virtual Network (Vnet) topology using the Azure Virtual Network Manager (AVNM) service. Learn about traffic routing patterns, hybrid DNS resolution, firewall security policies, and PrivateLink Services access to IaaS, PrivateLink access to PaaS services.
(In progress)