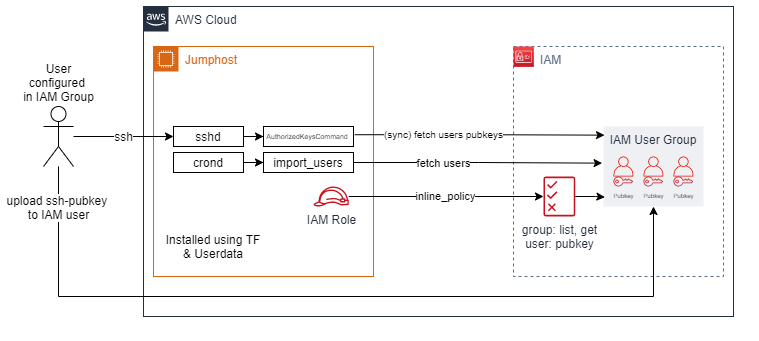
Only tested on Amazon Linux. Requires binaries (useradd, usermod, userdel, groupadd)
- Add the IAM-policy to the role of the ec2-instance. Make sure to replace
<name>with the actual IAM group name - Log into the ec2 instance or configure its userdata
- Make sure git is installed
- Execute
git clone https://github.com/ron96G/aws-ec2-iam-ssh.git - cd aws-ec2-iam-ssh/scripts
- Make sure you are root:
whoami - Setup variables in the configfile
- Execute the install script:
./install.sh <configfile>. It is installed into/opt/iam-ssh/
- Go to IAM -> Users -> YOUR_USER -> Security credentials -> SSH Keys for AWS CodeCommit
- Click
Upload SSH public key, paste your ssh pubkey into the field and save - When trying to connect using ssh, use your corresponding private key like
ssh -i <privkey_file> <user>@<host>
ssh-keygen -t rsa -b 4096 -f <filename>
- Automatically create users on the ec2-instance that are defined in the IAM group
- Automatically remove these users when they are no longer defined in the IAM group
- Execute custom scripts when a new user is created (requires absolute path to script)
- Authorize ssh requests using the public keys configured for the users in the IAM group