This repo has a sample application using theKeycloak JavaScript Adapter to implement an step-up mechanism.
The workflow implemented is:
First Login Step
- Users authenticate using their username and password credentials
Second Login Step
- Only the users with the
super-userrole enabled can login into the secured area of the application (/securedurl)
This app was tested with Red Hat Single Sign-On 7.6 using a realm called demo.
NOTE: This repo requires to have installed in Red Hat Single Sign-On the Email OTP provider from this repository.
To install the required node modules:
npm install The KC_URL environment variable identify the Red Hat Single Sign-On url, for
example http://localhost:8180.
To start:
npm startThe application will be available at http://localhost:8280.
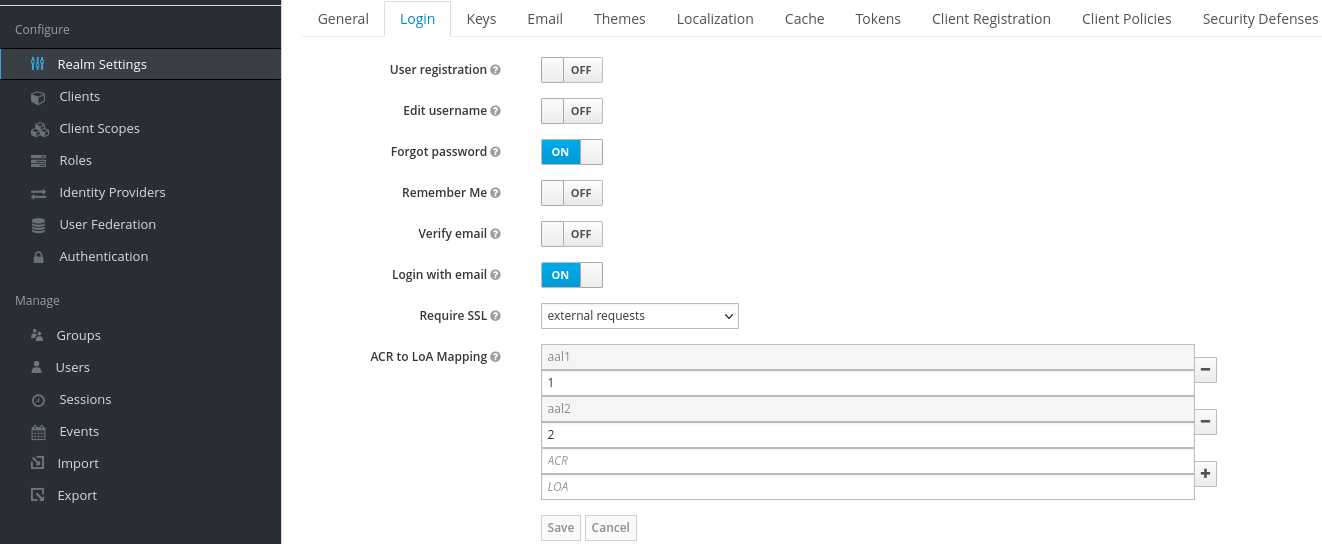
- Create the ACR to LoA mapping in the realm settings with the following values:
aal1to define the first step loginaal2to define the second step login
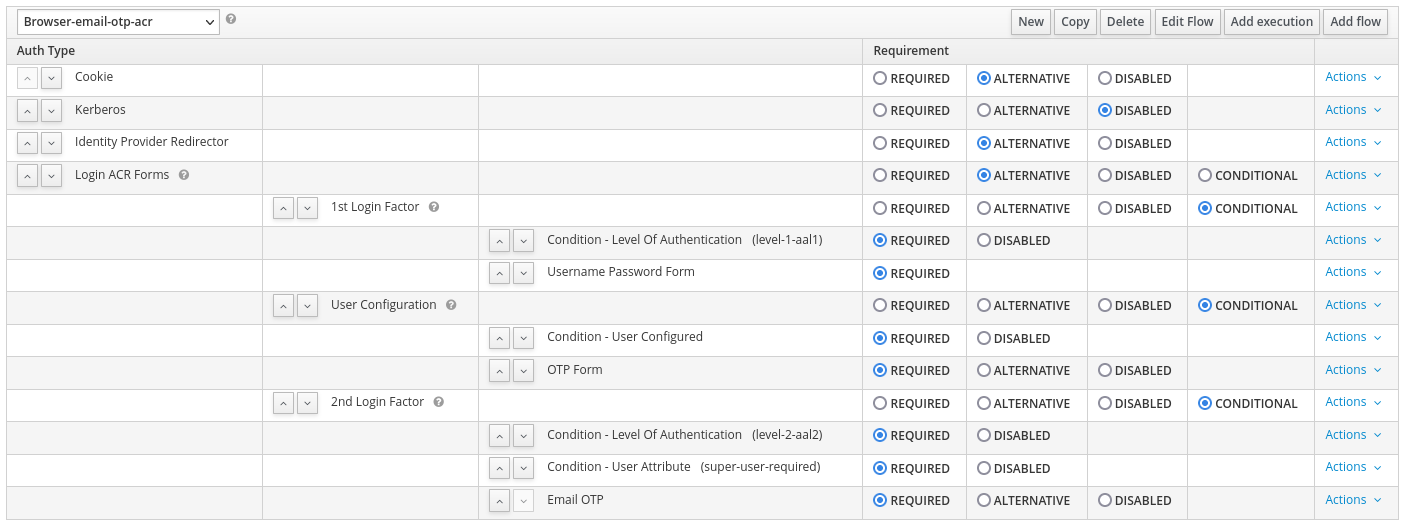
- Create the browser login flow with step-up mechanism similar to the following screenshot:
Each Condition - Level of Authentication should be similar to:
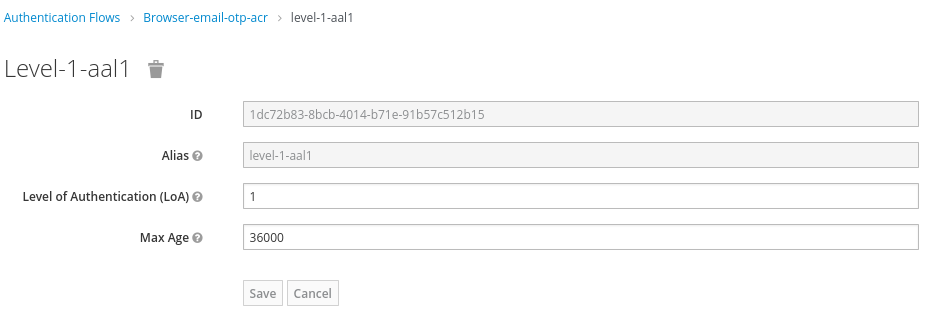
- For the first step login (
aal1):
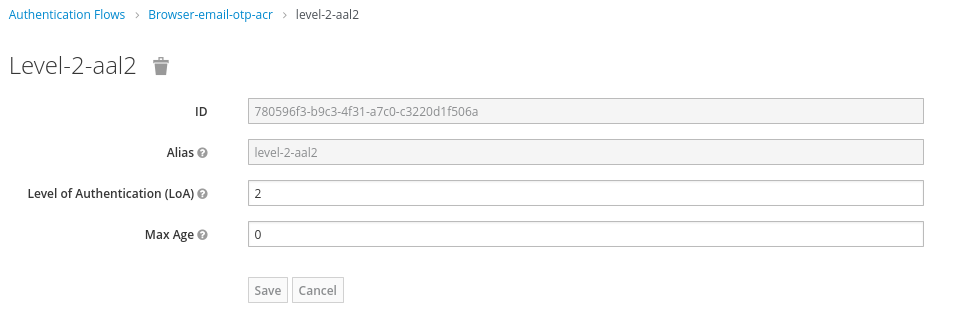
- For the second step login (
aal2):
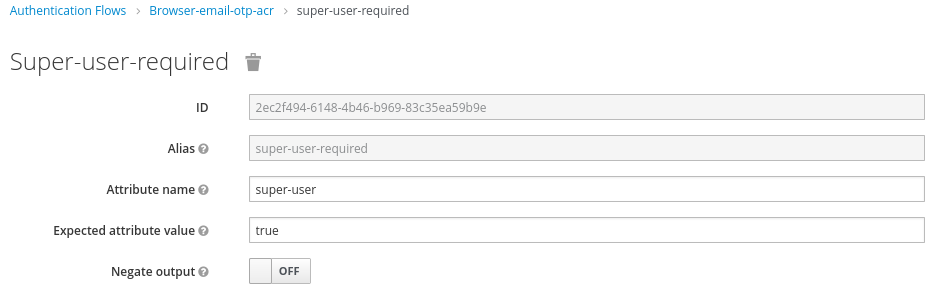
The second login step adds another condition to check the right user attribute,
in our case the super-user attribute.
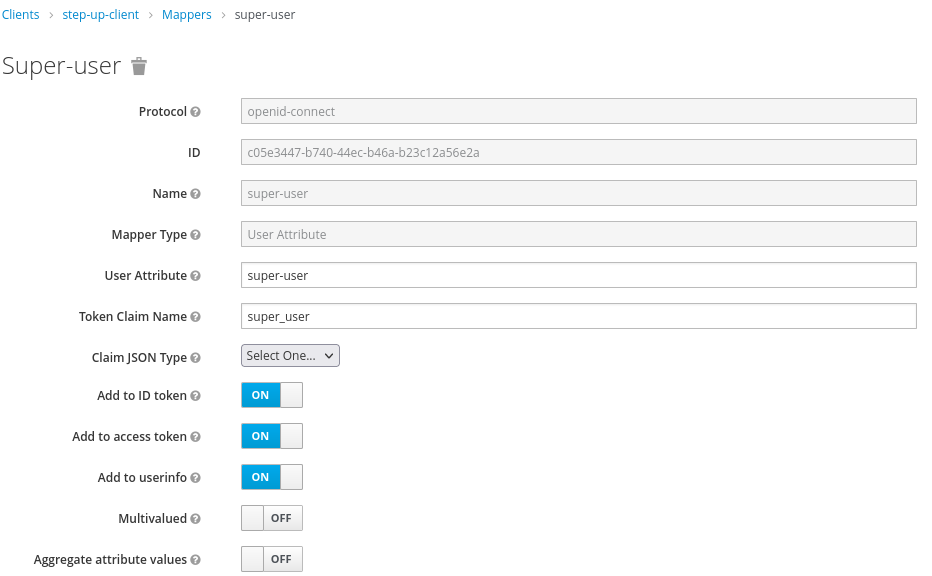
Create the a client identified as step-up-client in the demo realm. This client definition
will include a Mapper to map the user attribute into the token, such as:
-
Create a common user (adding the value
falseto thesuper-userattribute, or without any attribute). This user will not be able to login into the secured area. -
Create a super user (adding the value
trueto thesuper-userattribute). This user will be able to login into the secured area.