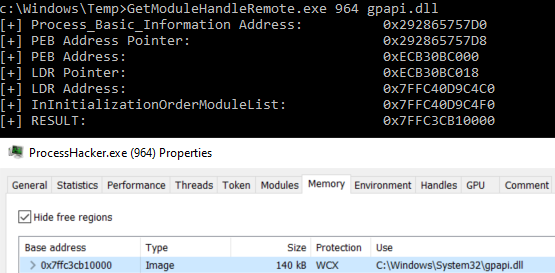
It works like the GetModuleHandle WinAPI but for remote processes: it takes a PID and DLL name, walks the PEB structure and returns the remote DLL base address.
This is useful to get the base address of a DLL in the system which is not loaded in your current process but you know is loaded in other process.
It uses the NtQueryInformationProcess and NtReadVirtualMemory NTAPIs to get the base address and NtOpenProcess to open the process handle. However, NtOpenProcess code is outside the function in case you want to use process handles directly.
Usage of the compiled binary:
GetModuleHandleRemote.exe PROCESS_PID DLL_NAME.dll
For example, to get the base address of gpapi.dll from Process Hacker: