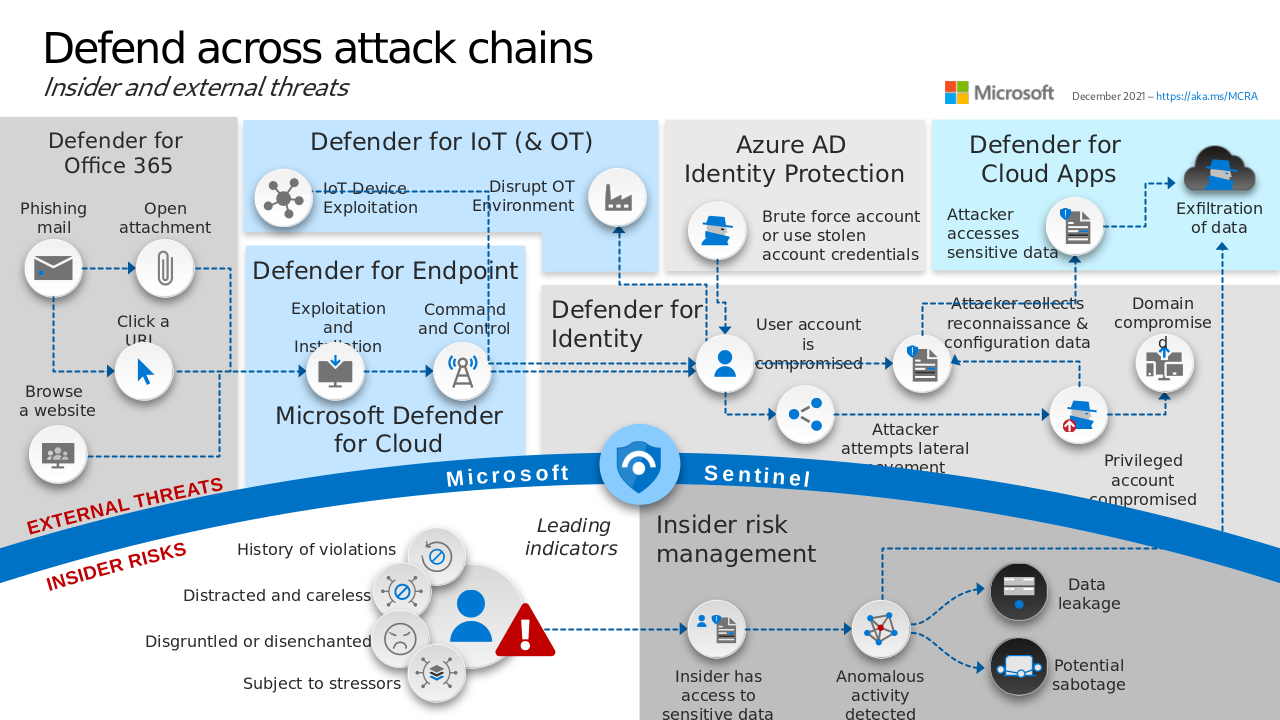
Slide 15 of Microsoft Cybersecurity Reference Architectures
Comprehensive resource for understanding, implementing, and optimizing Microsoft Defender.
This field guide is meticulously curated to provide security professionals, system administrators, and IT enthusiasts with in-depth knowledge and practical insights to effectively secure their systems and networks using Microsoft Defender.
Pull requests are welcome.
Security & Compliance, Exchange Online (EXO), and Exchange Online Protection (EOP) and others have PowerShell modules.
Install PowerShell modules.
Install-Module -Name Microsoft.Graph.DeviceManagement
Install-Module -Name AzureADPreview
Install-Module -Name ExchangeOnlineManagement
Install-Module -Name Microsoft.Online.SharePoint.PowerShell
Install-Module -Name MicrosoftTeamsImport module and connect to Entra ID tenant to access cmdlets.
Import-Module AzureADPreview
Connect-AzureADConnect to Security & Compliance PowerShell using Connect-IPPSSession from the
ExchangeOnlineManagement module.
Connect-IPPSSessionThe modules all have their respective connection cmdlets, Connect-MicrosoftTeams,
Connect-SPOService, and Connect-ExchangeOnline.
Supported hardware and software has Defender for Endpoint (MDE) builtin, making the deployment phase to these devices easier. Older versions of Windows and Other devices require agents for provide data to MDE.
Minimum hardware requirements for MDE on Windows devices are the same as the requirements for the operating system (that is, they aren't in addition to the requirements for the operating system).
Create a new Group to target Users or Devices with an Endpoint detection and response (EDR) policy that turns on MDE.
$group = New-AzureADMSGroup -DisplayName "New MDE Group" -MailEnabled $false -SecurityEnabled $true -MailNickName "NotSet"Create an EDR policy device configuration.
$params = @{
"@odata.type" = "#microsoft.graph.windowsDefenderAdvancedThreatProtectionConfiguration"
description = "New EDR Policy"
displayName = "New EDR Policy"
version = 7
allowSampleSharing = $true
enableExpeditedTelemetryReporting = $true
}
$deviceConfiguration = New-MgDeviceManagementDeviceConfiguration -BodyParameter $paramsCreate device configuration assignment to security group.
$params = @{
"@odata.type" = "#microsoft.graph.deviceConfigurationAssignment"
target = @{
"@odata.type" = "microsoft.graph.configurationManagerCollectionAssignmentTarget"
collectionId = $group.Id
}
}
New-MgDeviceManagementDeviceConfigurationAssignment -DeviceConfigurationId $deviceConfiguration.Id -BodyParameter $paramsInstructions to deploy with Configuration Manager.
MDE intergrates with Microsoft Intune, Defender for Office 365, and Defender for Cloud Apps.
Protect Office 365 users With message safety features like Anti-Spam, Anti-Phishing, Safe Links, Safe Attachments, and Safe Documents.
An umbra of Microsoft products and services that protect cloud assets. Defender for Key Vault, Defender for Servers, Defender for DNS, and others.
On-premise identity protection.
The single pane application that aggregate signals.