Find the vulnerabilities in the container images using vulnerability advisor on IBM Cloud. Complete the following steps:
- Sign up/Log in to IBM Cloud
- Create a kubernetes cluster on IBM Cloud
- Push the container images into your private registry
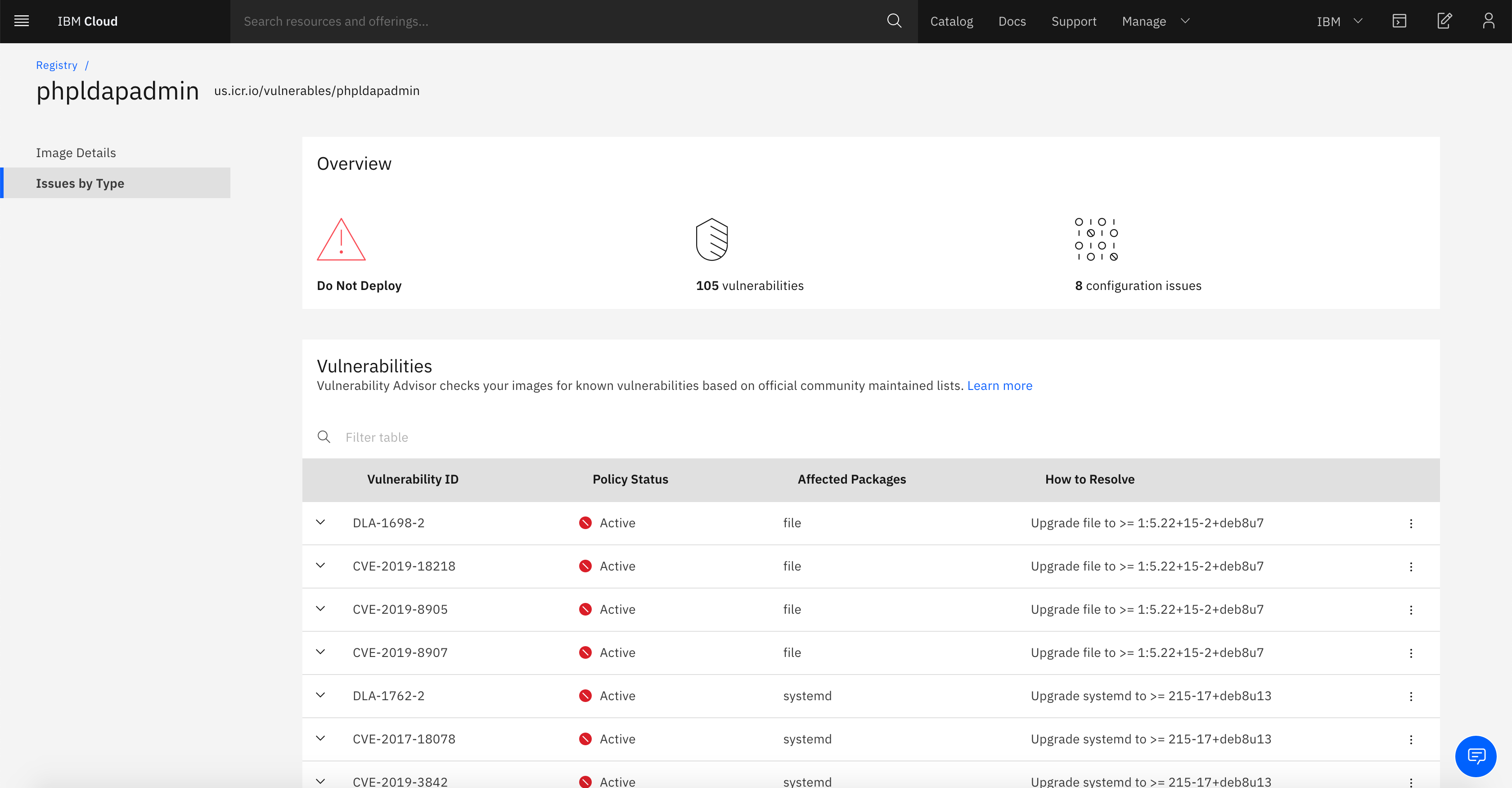
- Use vulnerability advisor to find the following:
i) Configuration issues identified, such as corrective actions needed, description of the issue, if the issue is exempt according to defined policies, and the type of check the issue failed.
ii) The ID of the assessment.
iii) A list of Common Vulnerabilities and Exposures (CVE) that are identified for the image: whether it is exempt, the CVE ID, security notice information, and a summary of the vulnerability.
iv) An overall status of the image based on vulnerabilities, identified configuration issues, and applied exemptions.
i) Operating system (OS) vulnerabilities: unpatched libraries and OS components, vulnerable kernel versions, and vulnerable network library versions.
ii) Configuration vulnerabilities: nonsecure OS settings, such as passwords or logins as well as network configuration, including allow root, no whitelisting of IPs, and lack of Secure Shell (SSH).
iii) Application weaknesses: XSS, buffer overloading, and SQL injection.
Use the following reference steps
-
Login to you IBM Cloud account
-
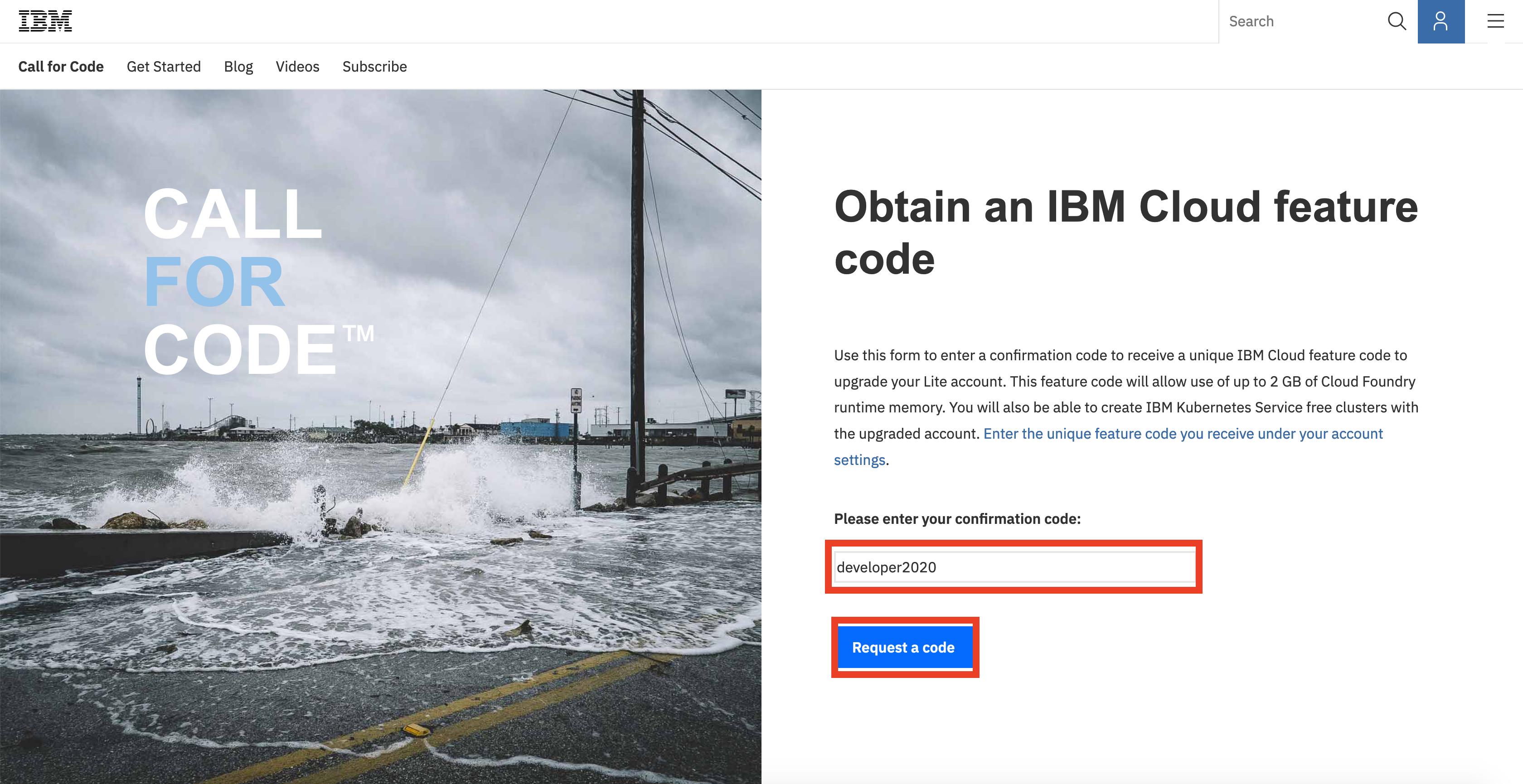
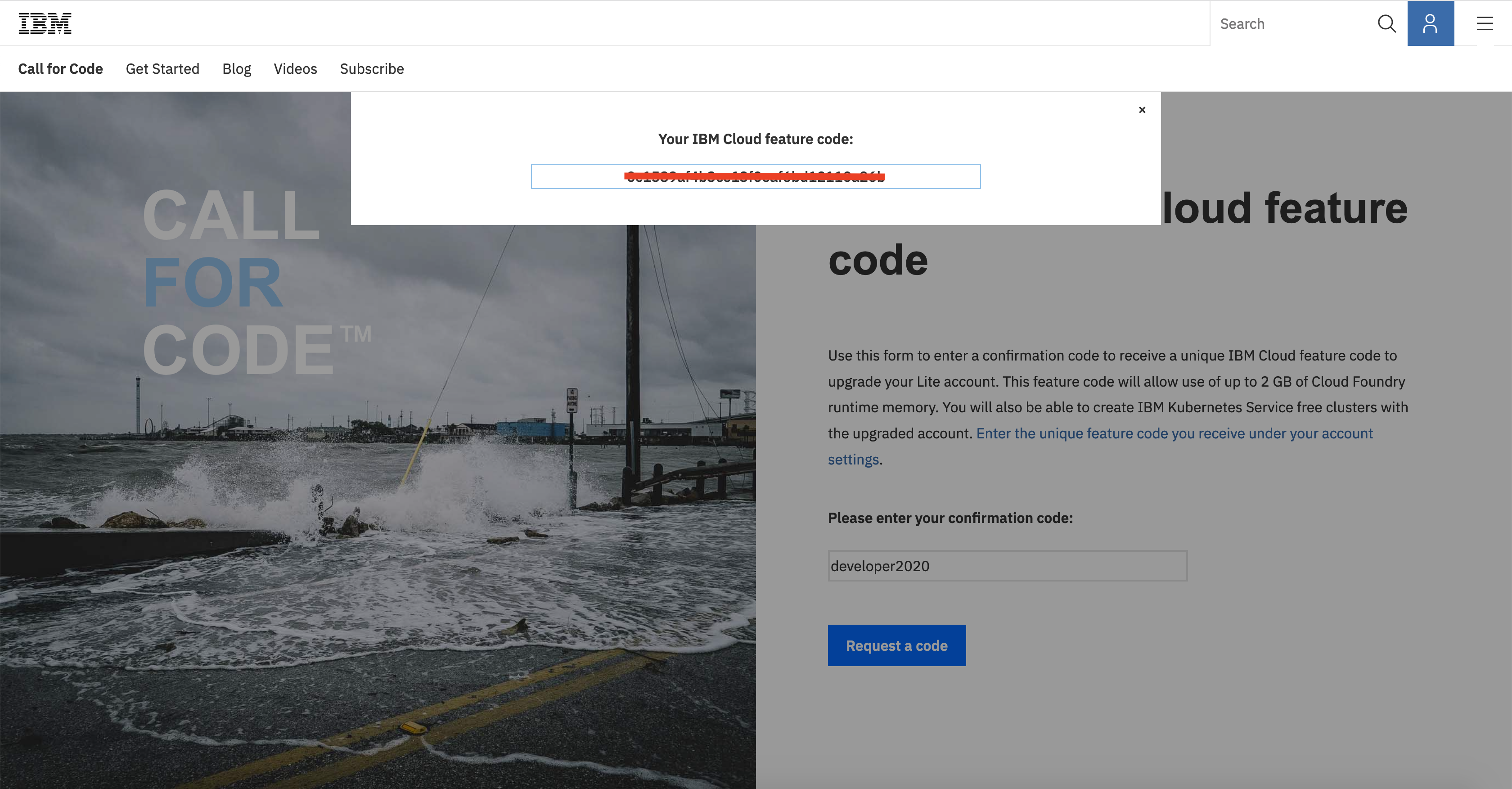
Go to here to get a promo code, login to your IBM Cloud account, enter the code developer2020 to get a promo code.
Copy the feature code
- Go to IBM Cloud
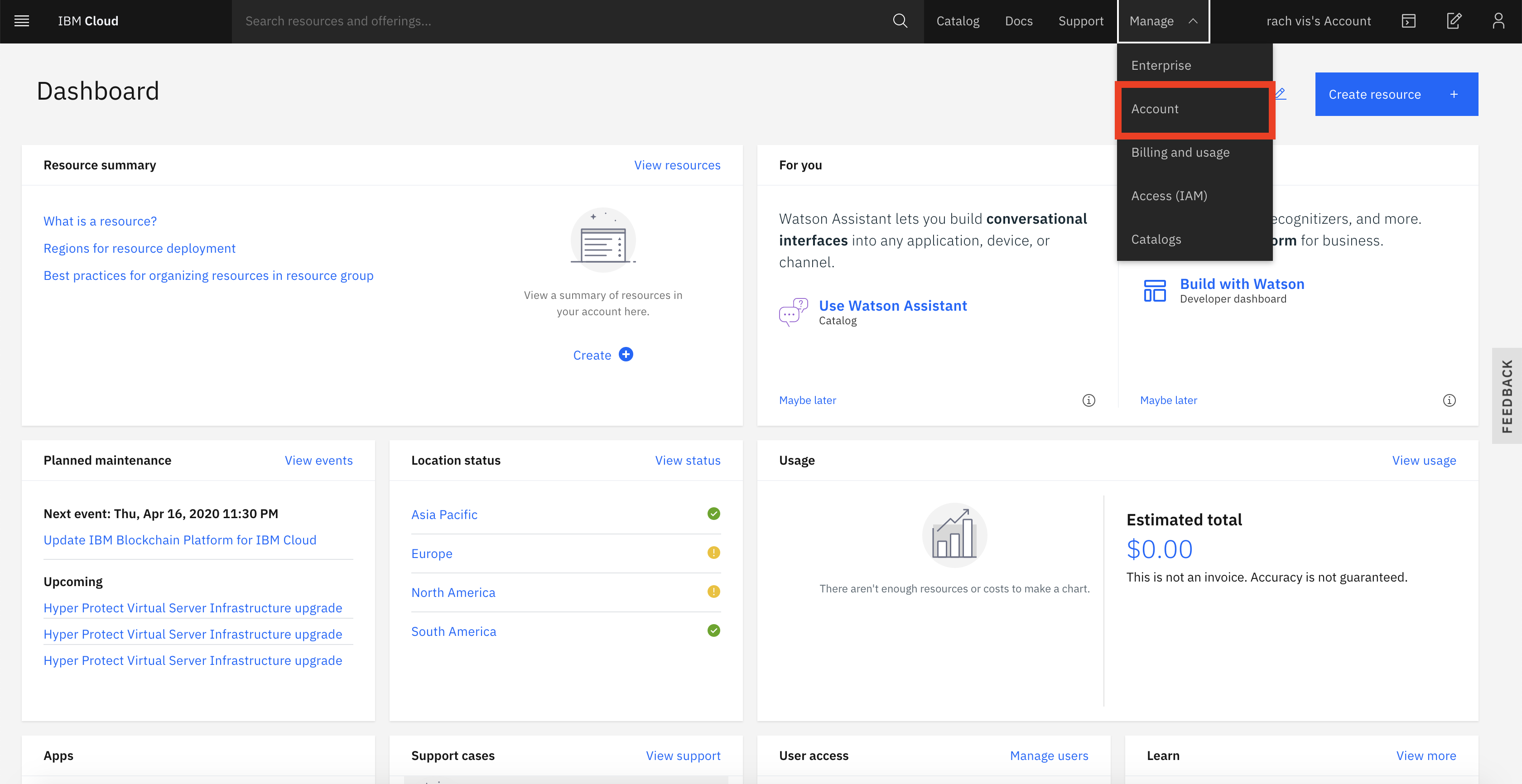
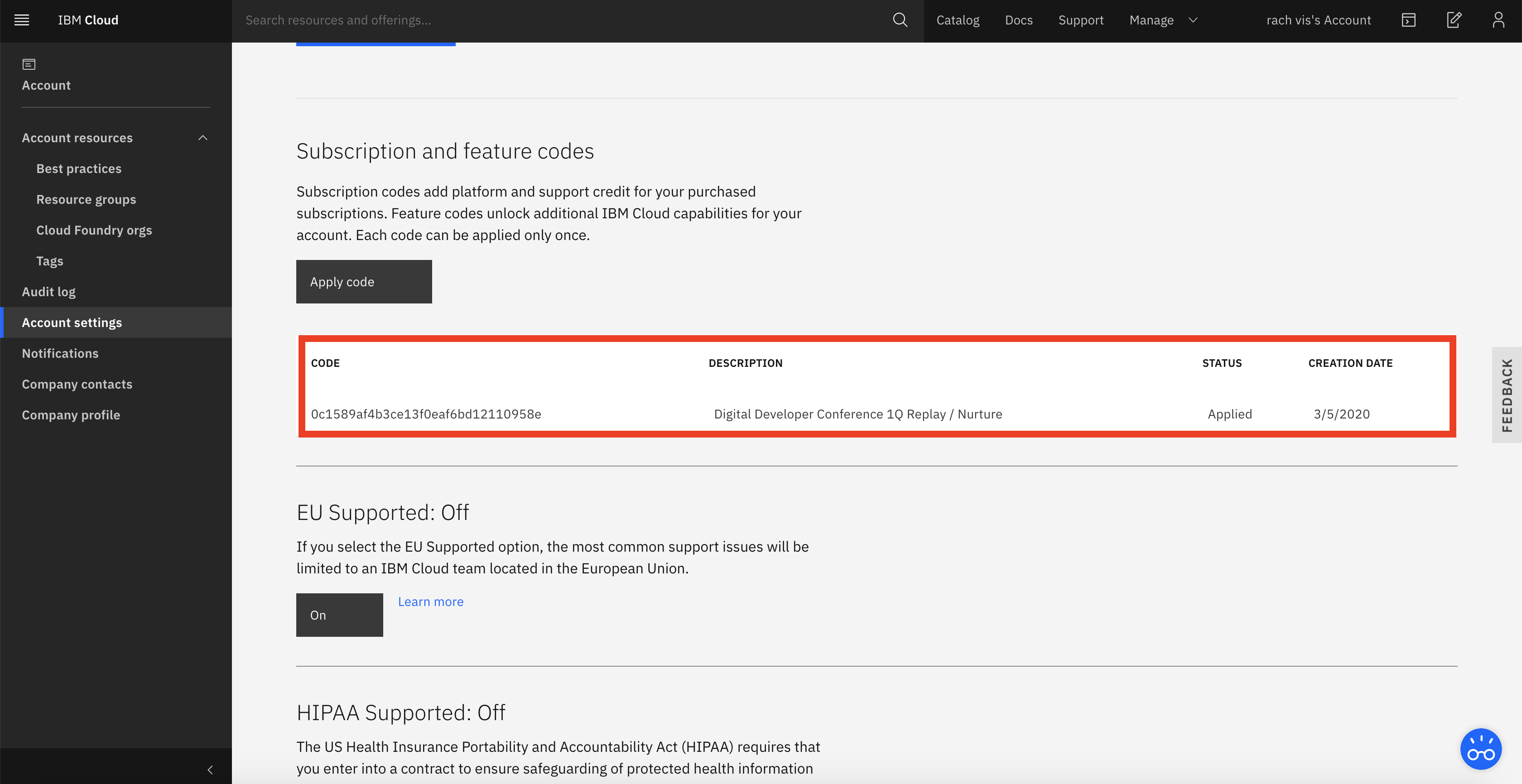
Click on Manage, select Account.
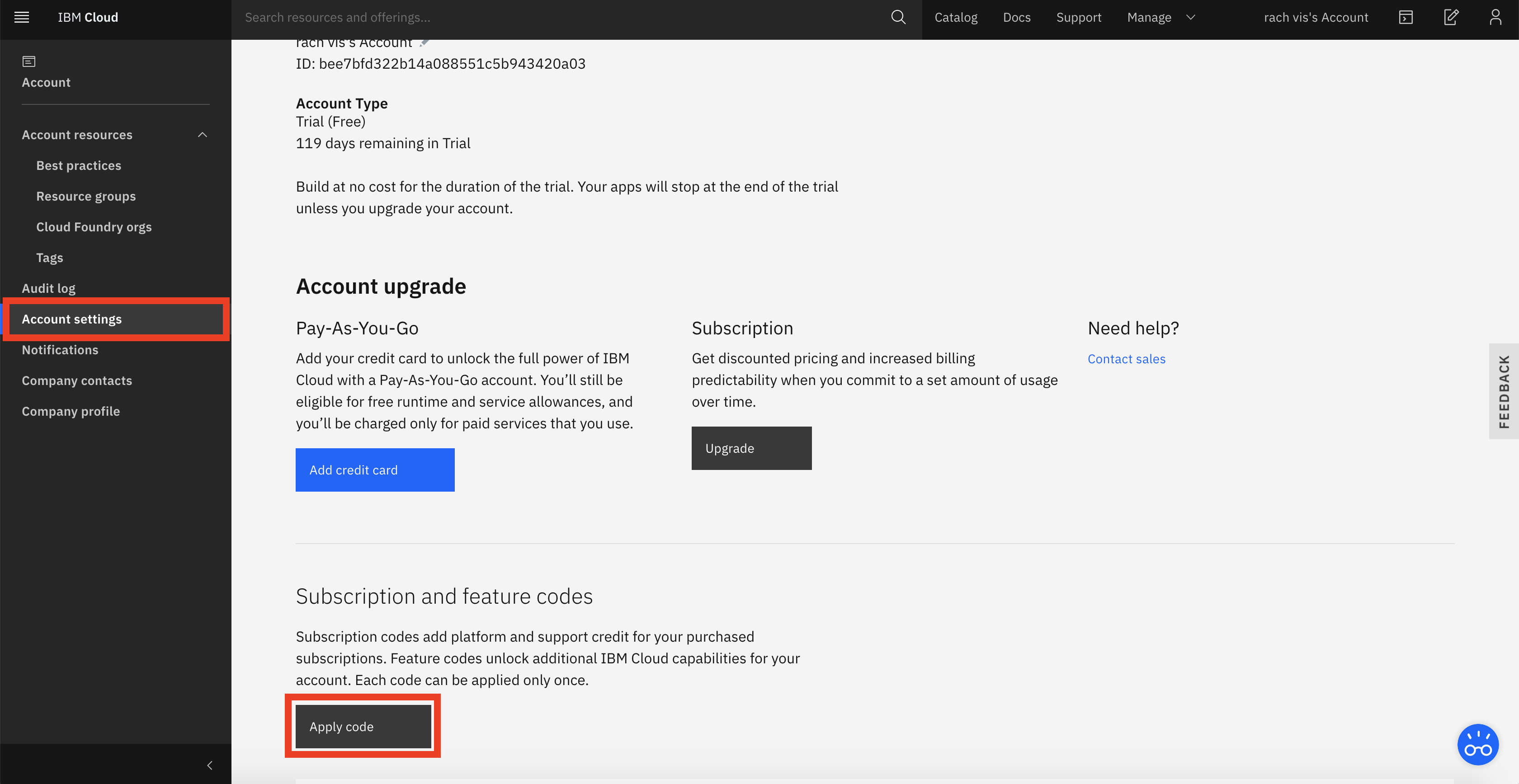
Click on Account settings, apply code, paste the feature code you have copied.
Make sure your feature code is applied to your account
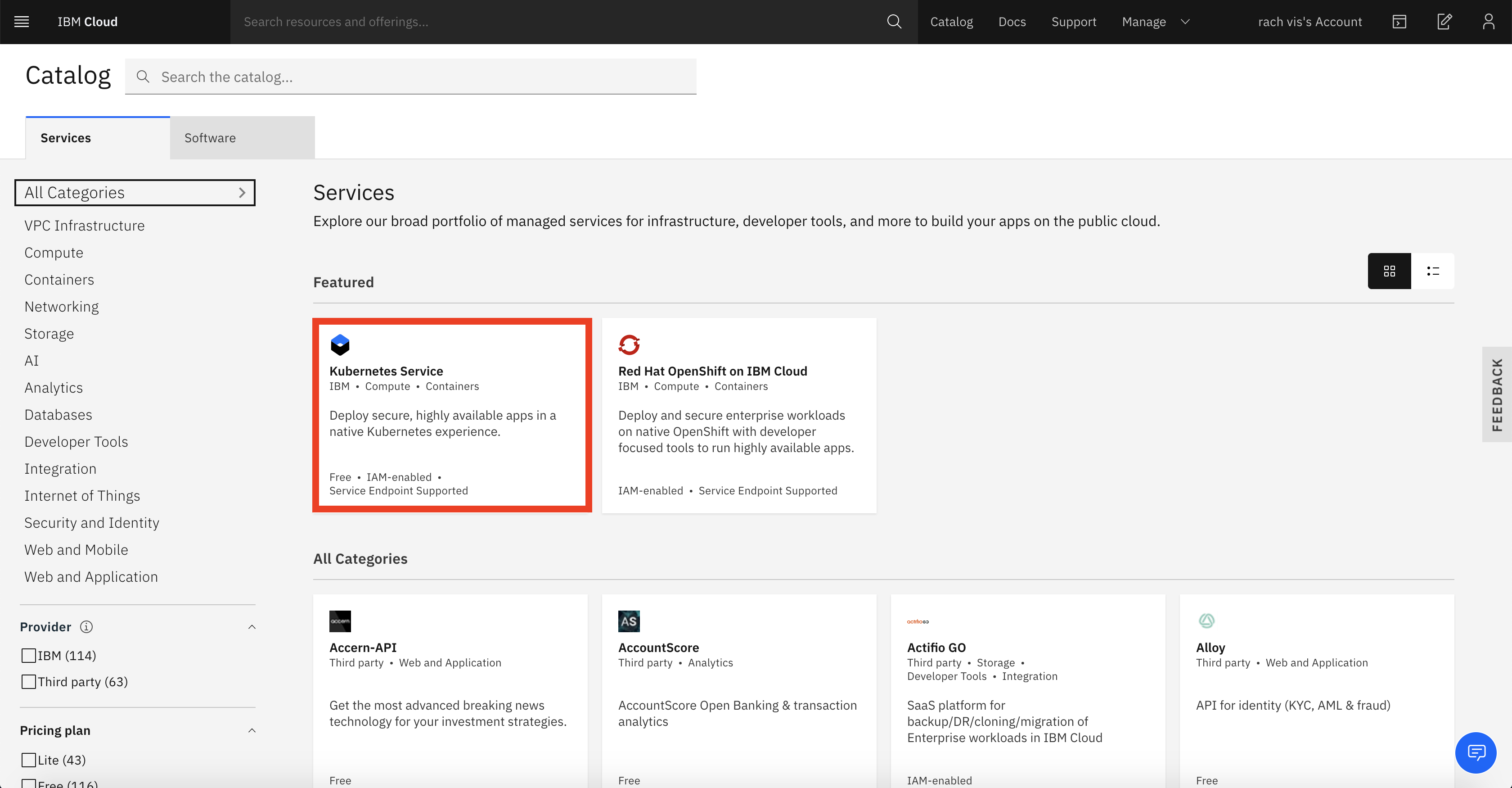
- Create a kubernetes cluster
Click on catalog and look for Kubernetes Service
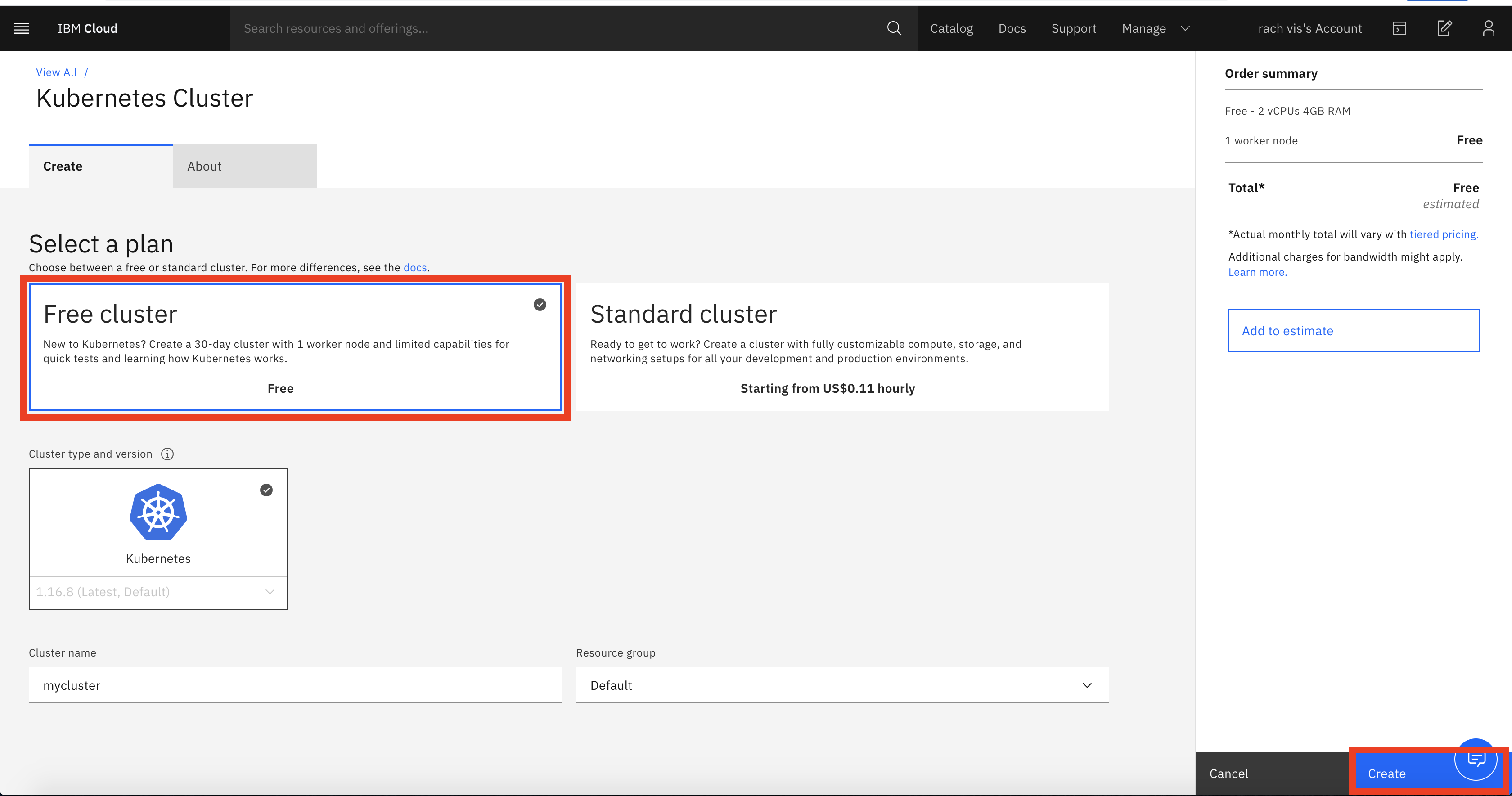
Select the plan - Free Cluster and click on create
You have successfully provisioned a Kubernetes cluster on IBM Cloud. Creation of cluster will take 15-20 minutes. Once the cluster is up and running, create a namespace and push the following images to see the vulnerabilities in them.
-
The following is the sample list