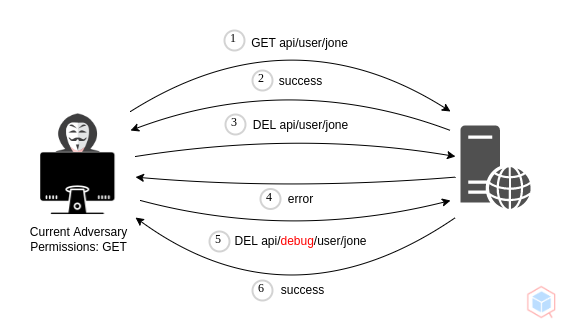
A threat actor may perform unauthorized functions by bypassing or abusing the target authorization mechanism
- Developer forgets to remove an in-house debugging mechanism associated with user-agent
- A threat actor finds out changing the user-agent header to debug grants different or higher privileges
Vary
- read & modify data
- execute commands
- validate access control
91f9b046-b802-425a-b71b-64c21c6b1c0f