In this sample we introduce a way to build CI/CD pipelines using the CDK to realize multi account/region deployments. An example use case for this is deployment of software and infrastructure to multiple environments such as Development, QA, Staging, and Production.
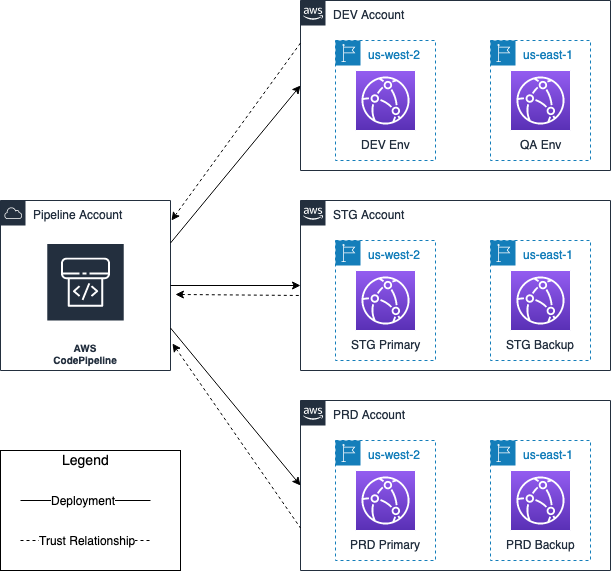
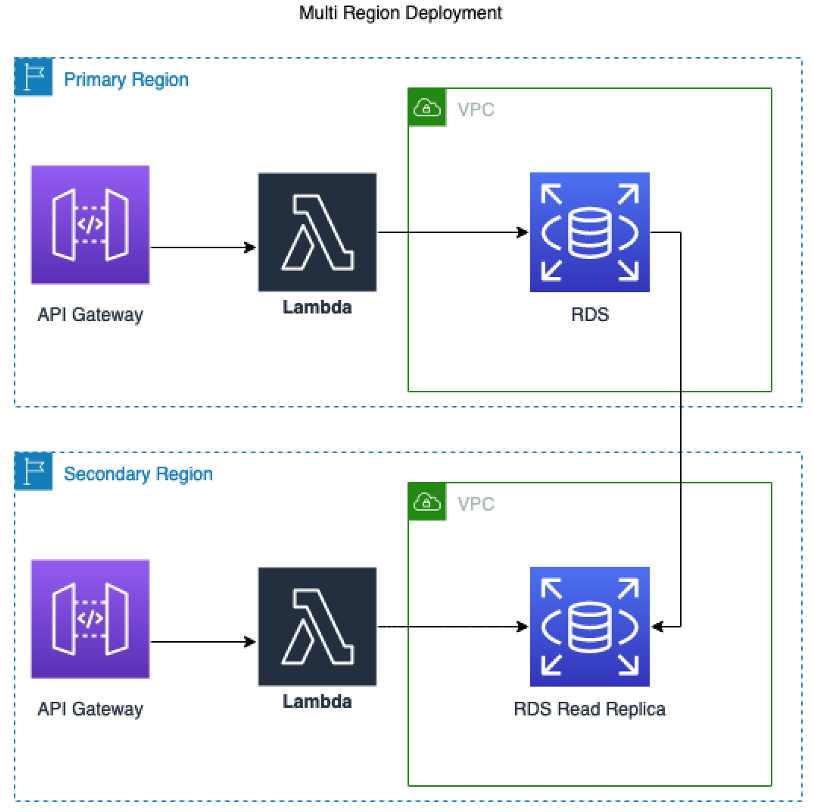
The following diagram shows the pipeline and target accounts’ regional architecture. The entire architecture spans four accounts. One account is for the deployment pipeline, and the other three accounts are the accounts that the application is deployed to:
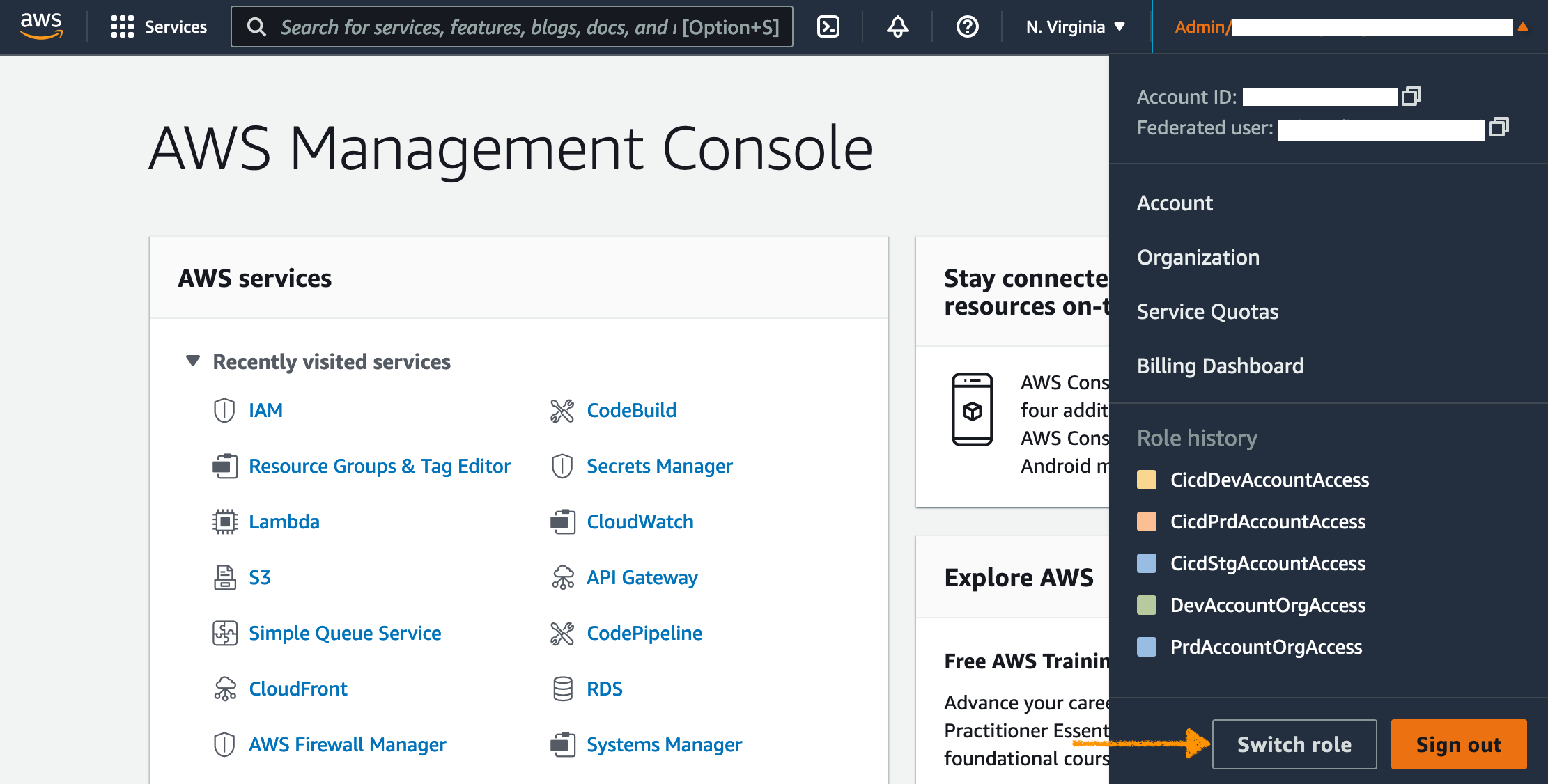
During the deployment, we will need to switch between four AWS accounts to check resources. To avoid the time spent to log in and out of accounts, we will leverage roles to get access to different accounts in the console. This step will facilitate switching accounts in the console with 1-click. The alternative to this approach would be to continuously log in and out of the accounts used by the pipeline, and the accounts the pipeline deploys to.
-
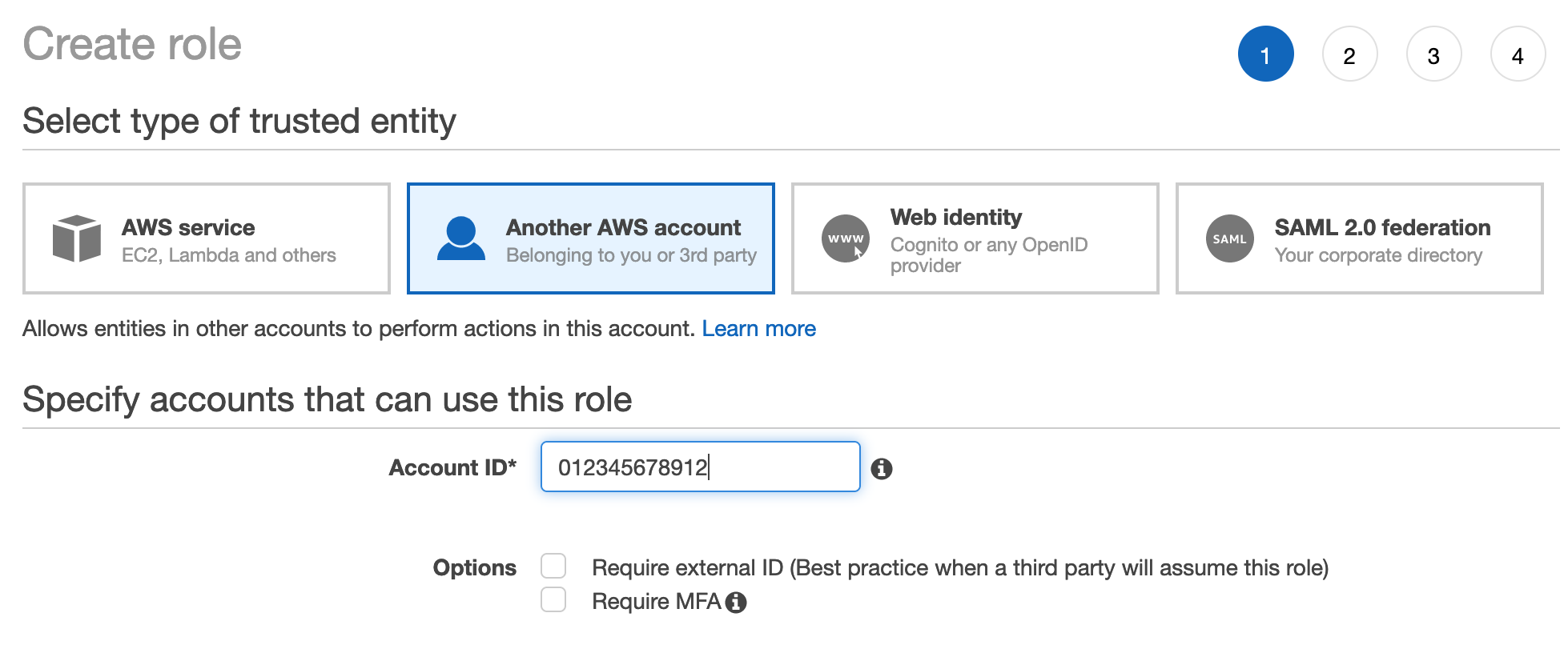
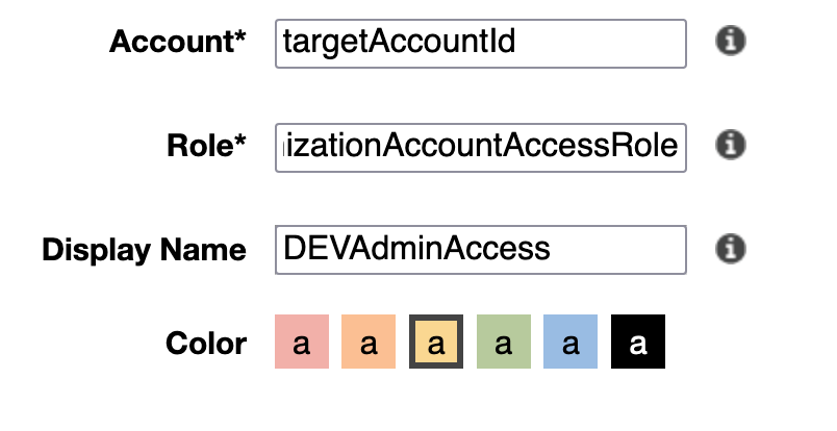
In each of target accounts (prd, stg, dev), using the IAM (Identity and Access Management) service, create a role
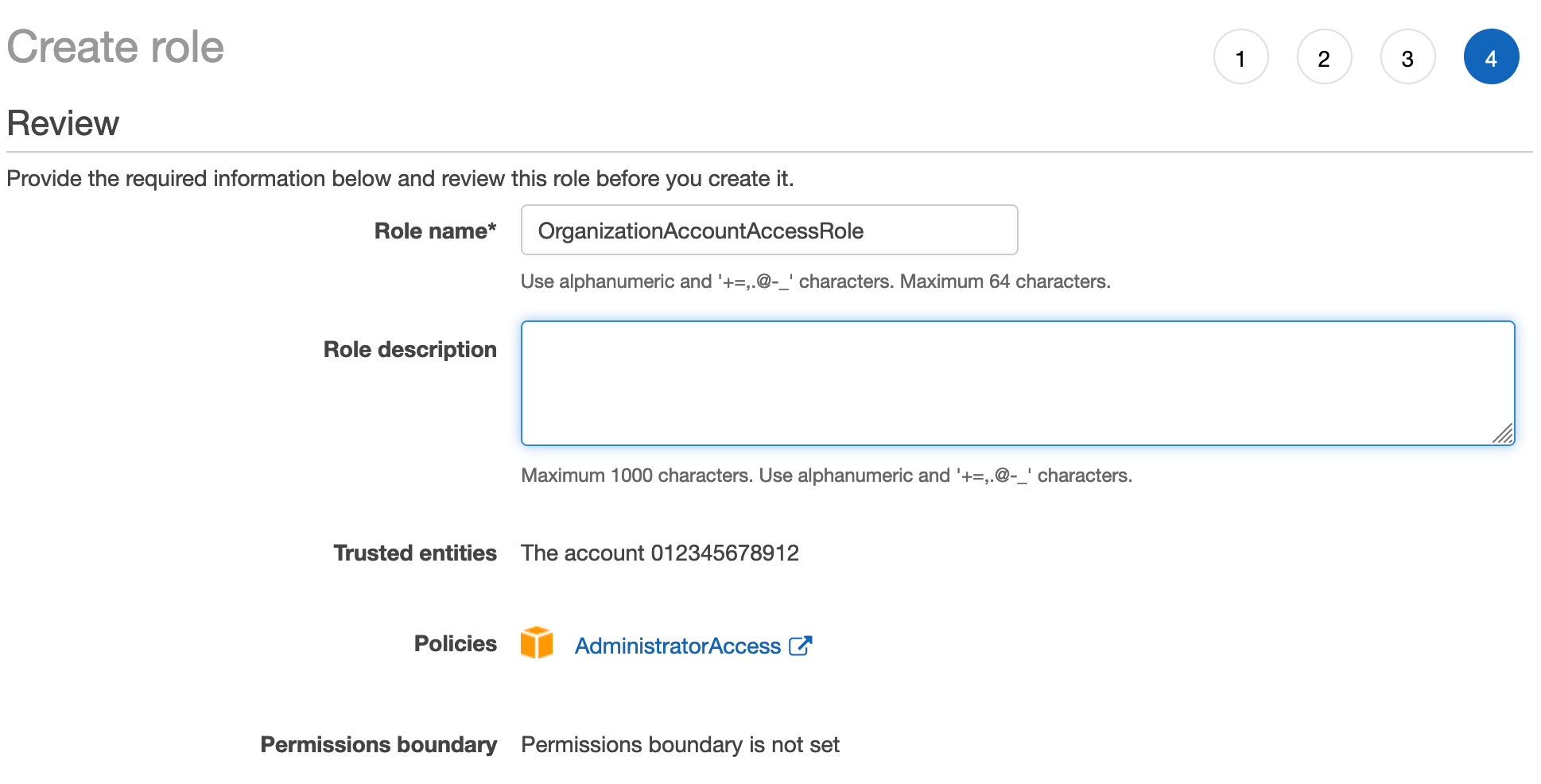
OrganizationAccountAccessRoleand configure it to trust the pipeline account, attach policy, add tags, and confirm creation: -
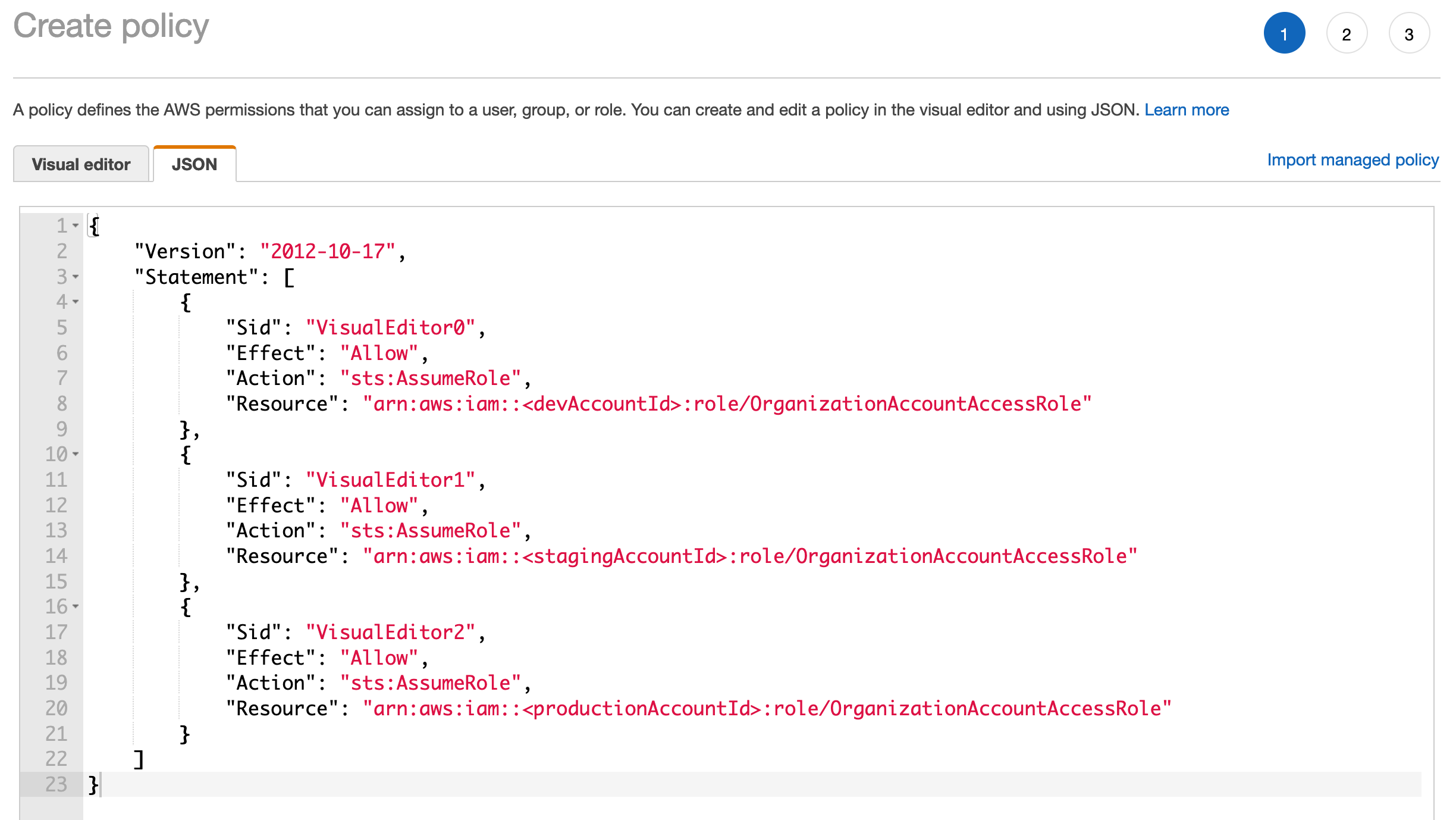
In the pipeline account, create a policy as below for each of the target accounts and attach to a role your account can access.
- Policy template:
{ "Version": "2012-10-17", "Statement": [ { "Sid": "VisualEditor0", "Effect": "Allow", "Action": "sts:AssumeRole", "Resource": "arn:aws:iam::<devAccountId>:role/OrganizationAccountAccessRole" }, { "Sid": "VisualEditor1", "Effect": "Allow", "Action": "sts:AssumeRole", "Resource": "arn:aws:iam::<stagingAccountId>:role/OrganizationAccountAccessRole" }, { "Sid": "VisualEditor2", "Effect": "Allow", "Action": "sts:AssumeRole", "Resource": "arn:aws:iam::<productionAccountId>:role/OrganizationAccountAccessRole" } ] } -
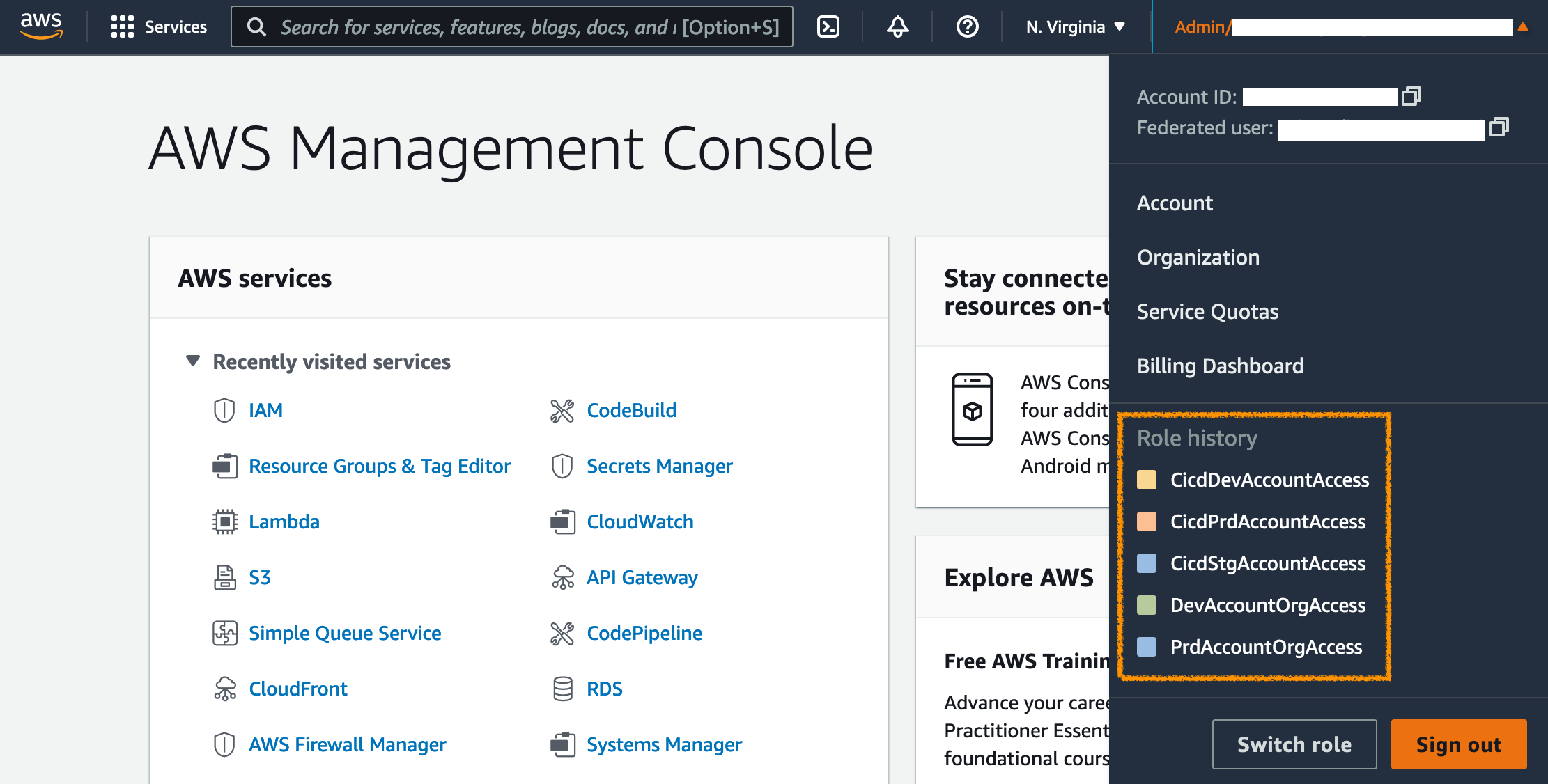
Use drop-down menu at top-right of the console to switch between accounts.
Each account region combo that is deployed to must be bootstrapped. Since it is a cross-account deployment, a trust must be established during this process.
Deploying AWS CDK apps into an AWS environment may require that you provision resources the AWS CDK needs to perform the deployment. These resources include an Amazon S3 bucket for storing files and IAM roles that grant permissions needed to perform deployments. The process of provisioning these initial resources is called bootstrapping.
-
For each target account/region run the following CLI command (Must be ran as user with appropriate privs in the target account):
cdk bootstrap --trust <pipelineAccountId> --cloudformation-execution-policies arn:aws:iam::aws:policy/AdministratorAccess aws://<targetAccountId>/<targetRegion> -
Given we are deploying to 2 regions in 3 different accounts, we must run this command 6 times
./cdk/bin/pipeline.ts: Creation of CDK App for Pipeline
./cdk/lib/cdk-pipeline-stack.ts: Definition of stacks to deploy, as well as environments to deploy to.
-
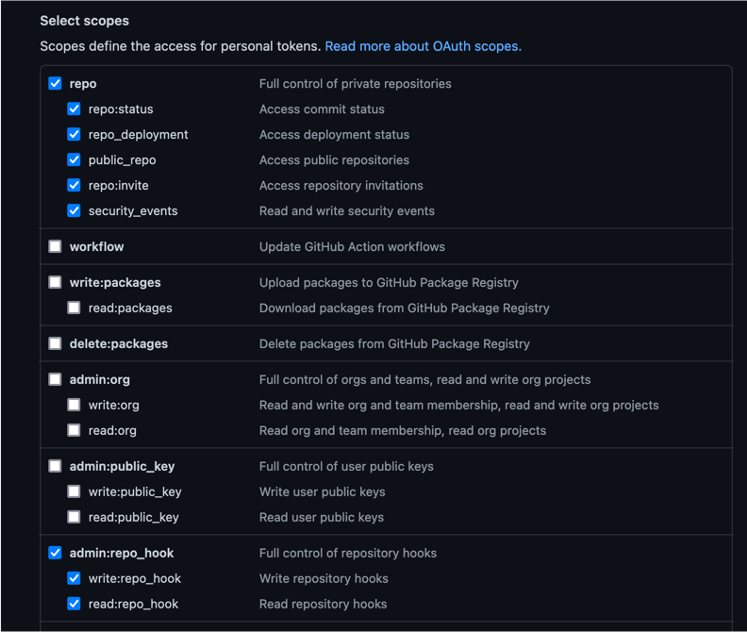
Create a github token here. Set the permission as below
-
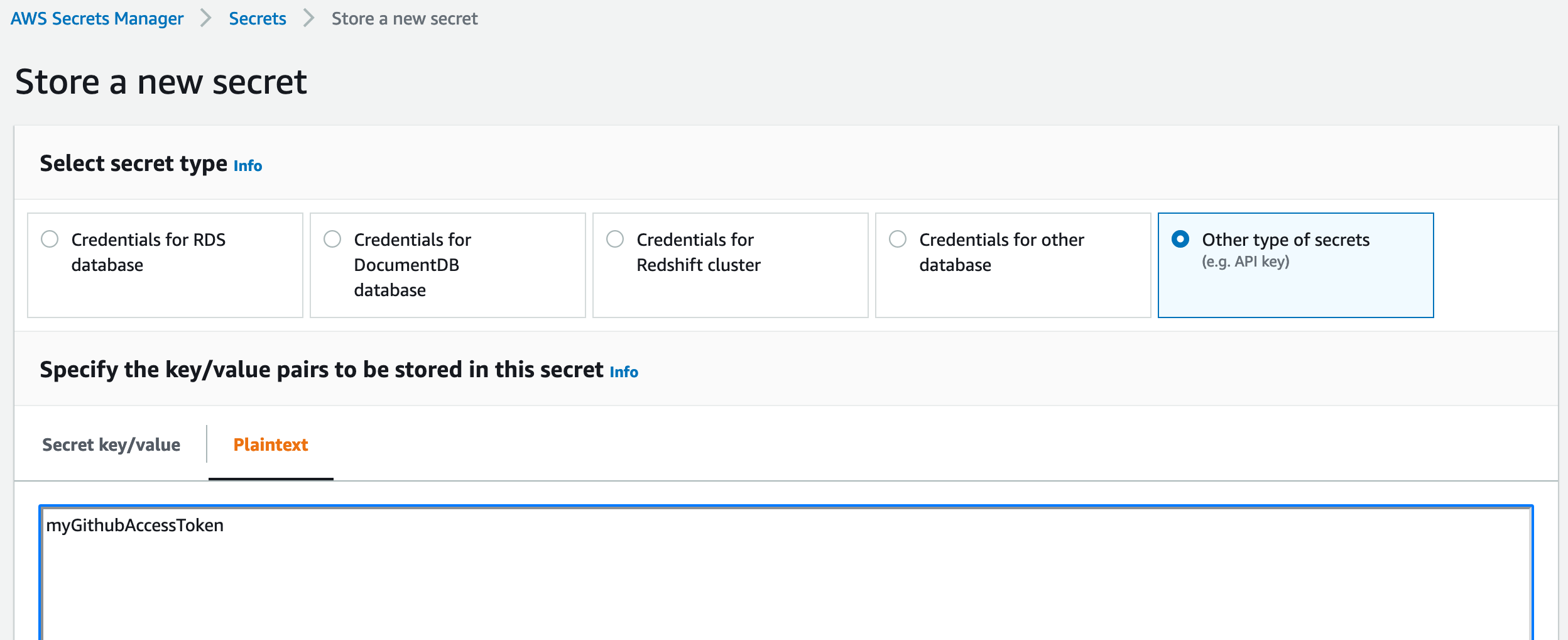
In pipeline account/region, create Secret Manager secret to store access token for GitHub repo. The token must stored as a plaintext secret with a name of
github-token:
-
Clone the repo and run command. When prompted to create security groups/deploy, accept.
cdk deploy CdkPipelineStack -
Navigate to CodePipeline in Console and cancel the initial build.
-
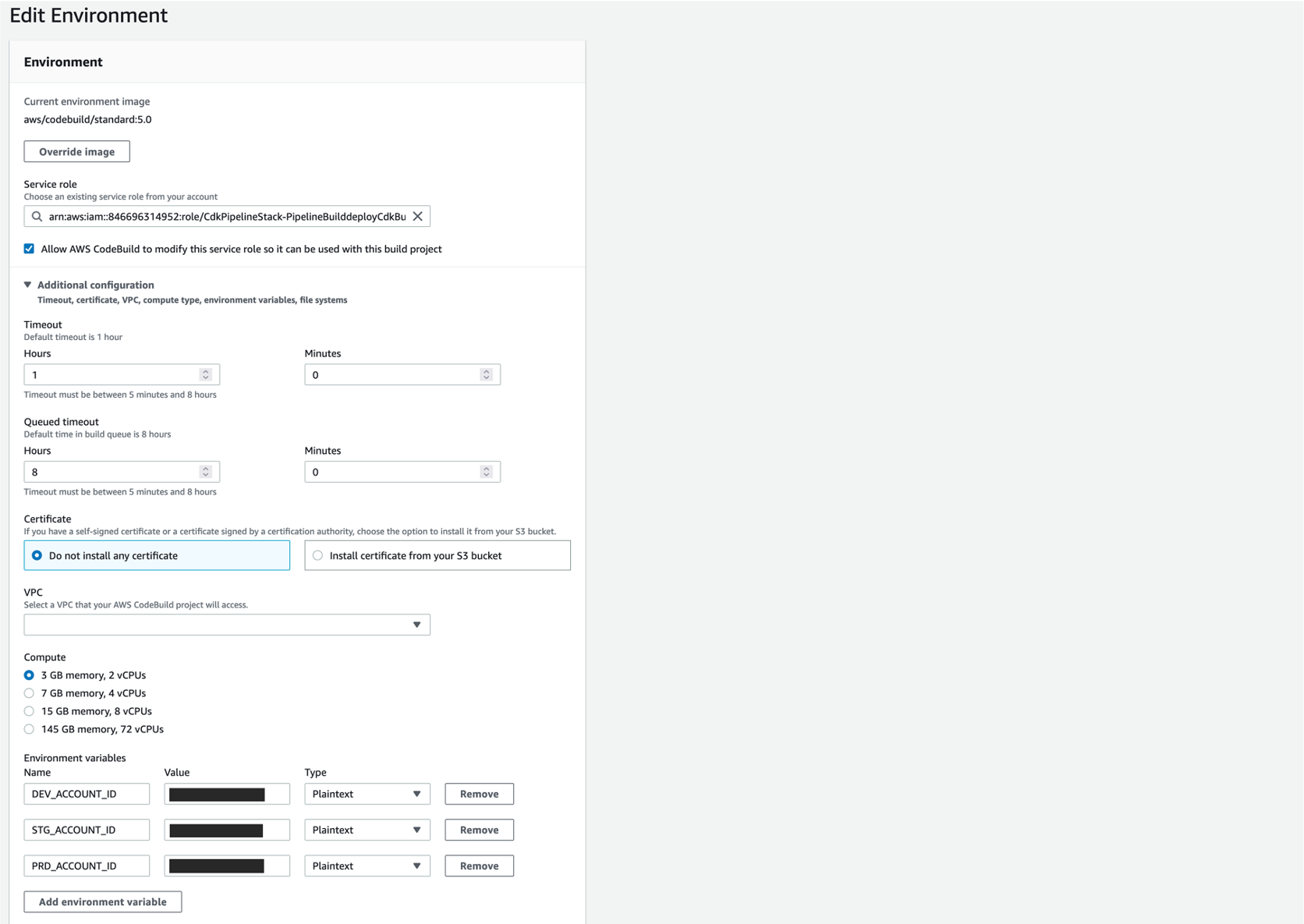
Set Env Vars in the Build step of the pipeline as below.
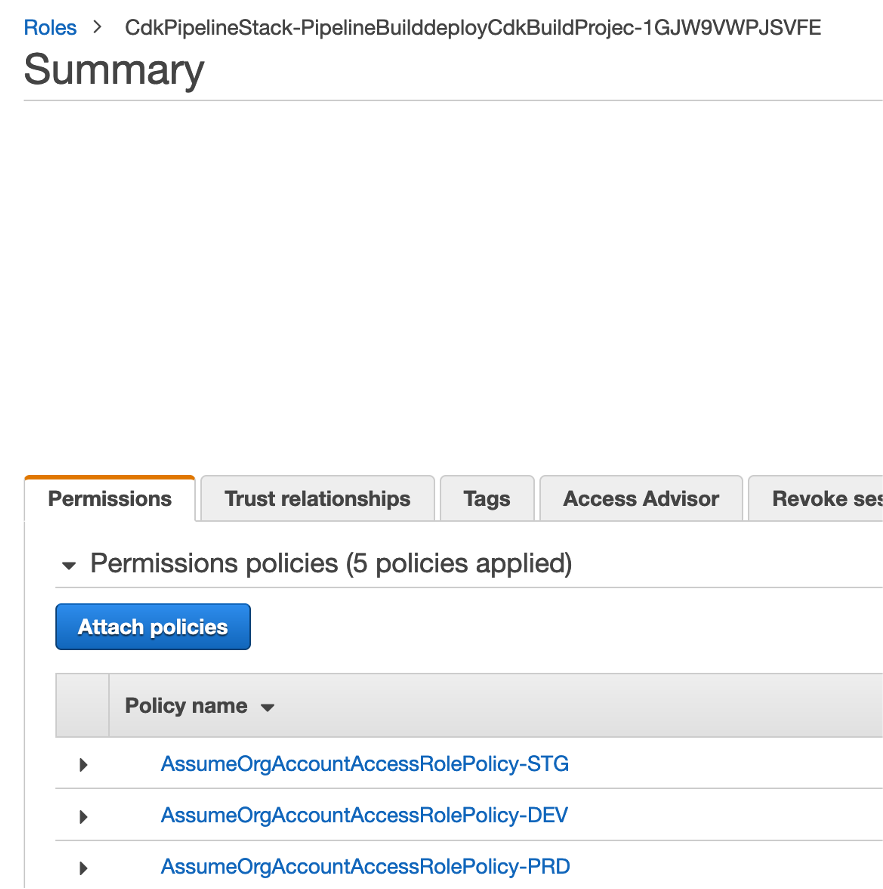
In pipeline account, create a Policy for each target account to allow Pipeline role to assume Roles created during bootstrap process
-
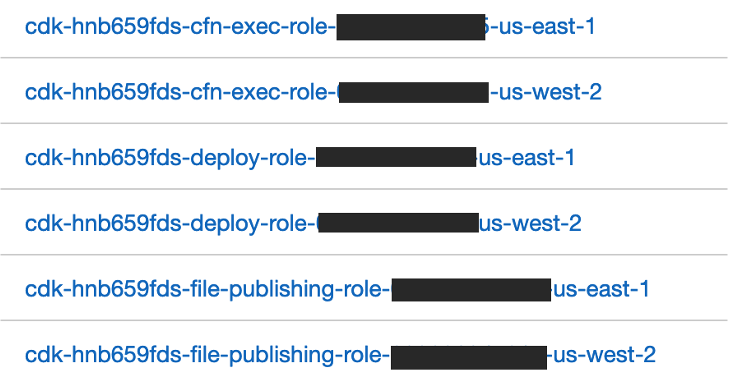
Get CDK prefix from a target account
-
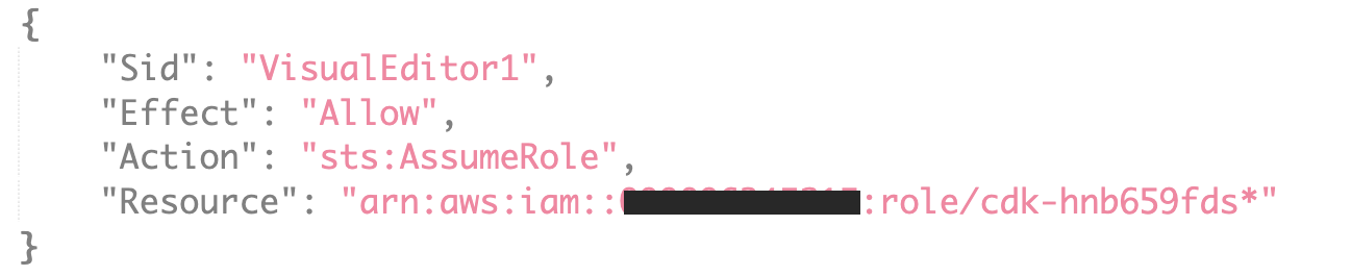
Create policy for all 3 accounts
-
Attach all 3 policies to the Pipeline Build role (Very similar to what we did for cross account access in console)
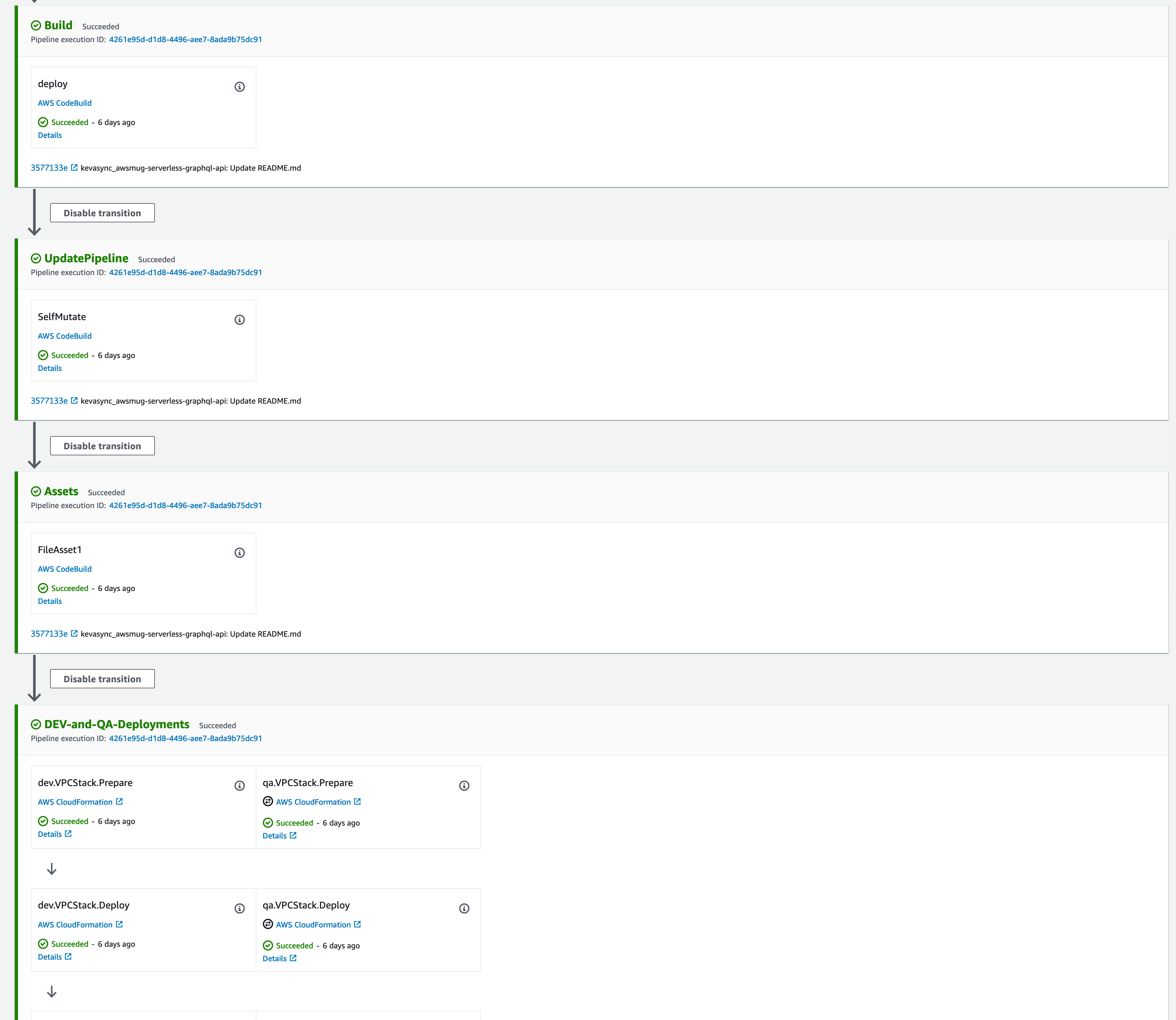
Navigate to Pipeline and Release Changes, app resources will be deployed in three accounts and two regions in each account.
Waves can be used to deploy multiple stages in parallel. In this example:
- DEV and QA
- PRD and STG Primary
- PRD and STG Secondary
App structure contains three stacks:
- VPC: Core networking
- RDS: RDS Postgres Instance (or read replica in multi-region deployment)
- API: Lambda w/ VPC attachment and API gateway
Each Stack (VPC, RDS, API) is deployed independently to each account/region This allows each to be updated separately.
You will need to go CloudFormation in each account/region and delete the stacks when you want to clean up the resources.
Explore nested stacks if this behavior is not acceptable
See CONTRIBUTING for more information.
This library is licensed under the MIT-0 License. See the LICENSE file.