This repository contains a number of CloudFormation templates that are intended to:
- Create a Transit Gateway with a single, non-default route table.
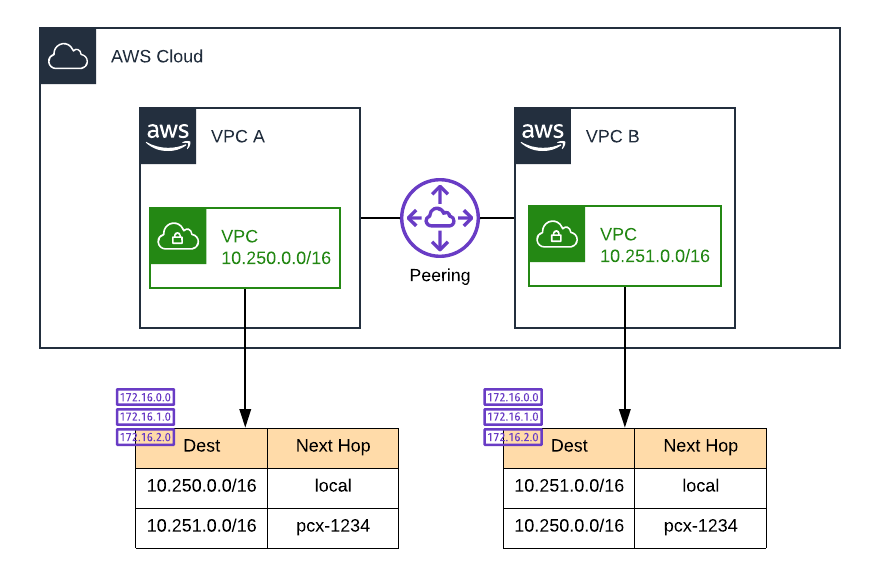
- Stand up an environment of 2 VPCs, VPC A and VPC B, and establish a peering connection between them.
- Create an EC2 instance in each VPC, and using Systems Manager Session Manager, connect to each and stand up a ping. This should validate connectivity between the two VPCs.
- Once connectivity has been established across the peering connection, attach the VPCs to the Transit Gateway and update the route tables.
- Remove the peering connection and confirm connectivity still exists between VPC A and VPC B via Transit Gateway.
First we want to create a Transit Gateway with a single, non-default route table. This route table will be used for the "spoke" VPCs when they are attached to the Transit Gateway. In this step, though, we will simply create the Transit Gateway and route table with no attachments.
- Clone this repository so all of the templates are stored locally.
- Change into the
templatesdirectory. - Run the following command:
Important!! To make things easy, copy the commands below verbatim. Otherwise, you will need to update the parameters JSON files appropriately.
aws cloudformation create-stack --stack-name bidmc-poc-tgw \
--template-body file://1-tgw.yaml --region us-east-1Now we will stand up 2 VPCs, each with a single EC2 instance in them. Once complete, we will establish a peering connection between them.
- From the
templatesdirectory, run the following to create VPC A:
aws cloudformation create-stack --stack-name bidmc-poc-vpc-a \
--template-body file://2-vpc.yaml \
--parameters file://vpc-a-parameters.json \
--region us-east-1 --capabilities CAPABILITY_IAM- Once that completes, run the following to create VPC B:
aws cloudformation create-stack --stack-name bidmc-poc-vpc-b \
--template-body file://2-vpc.yaml \
--parameters file://vpc-b-parameters.json \
--region us-east-1 --capabilities CAPABILITY_IAMNow we need to establish a peering connection between these two VPCs. This requires standing up a peering connection and updating the route tables of each VPC to use the peering connection appropriately.
- Run the following to create the VPC peering connection:
aws cloudformation create-stack --stack-name bidmc-poc-peering \
--template-body file://3-vpc-peering.yaml \
--parameters file://vpc-peering-parameters.json \
--region us-east-1So what did we just build? At a high level:
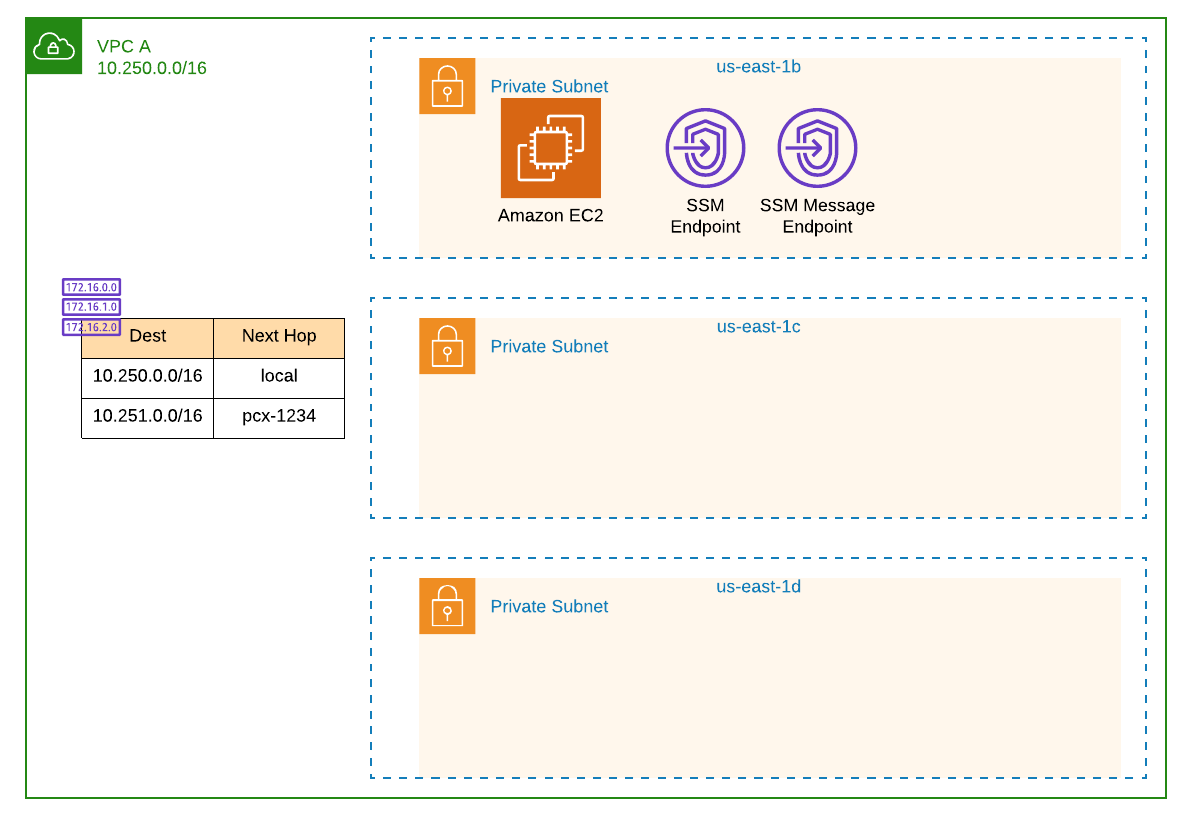
Drilling in to VPC A we have:
In the previous step we deployed 2 VPCs, each with a single EC2 instance in them. Now we will use Systems Manager Session Manager to connect to one of the two instances and ping the instance in the other VPC. We will do this to confirm connectivity between the two VPCs, and once we cutover to Transit Gateway, ensure this connectivity remains.
- In your console, ensure you are in the region where you deployed these VPCs.
- From the Services dropdown, go to CloudFormation.
- Select the stack for VPC B. If you copied the commands above, this should be
bidmc-poc-vpc-b. - Select the Outputs tab and copy the value of
EC2InstanceIP. - From the Services dropdown, go to Systems Manager.
- Click on Session Manager from the column on the left.
- Click the Start session button at the top right.
- Select
bidmc-poc-vpc-aand click Start session. - Using the IP address from step 4, run the following, being sure to replace
<IP address>:
ping <IP address>If successful, you should see output similar to:
64 bytes from 10.250.0.160: icmp_seq=1 ttl=255 time=0.143 ms
64 bytes from 10.250.0.160: icmp_seq=2 ttl=255 time=0.559 ms
64 bytes from 10.250.0.160: icmp_seq=3 ttl=255 time=0.160 ms
64 bytes from 10.250.0.160: icmp_seq=4 ttl=255 time=0.213 ms
64 bytes from 10.250.0.160: icmp_seq=5 ttl=255 time=0.157 msLeave this going in the background and move on to Step 4.
But wait - how does this work without a NAT instance? Or an EIP and an Internet Gateway?
In the VPC template, we set up PrivateLink endpoints for the Systems Manager Service. Essentially, a network interface was placed into the VPC with an appropriate security group to allow connections to it from within the VPC. A DNS entry in a private hosted zone was also added so that the requests to the SSM endpoint would resolve to the interface within the VPC and not the public endpoint. Check this out to learn more about PrivateLink.
Now that we know the VPCs can communicate over the VPC peering connection, lets establish connectivity via the Transit Gateway which will be used to replace the VPC peering connection.
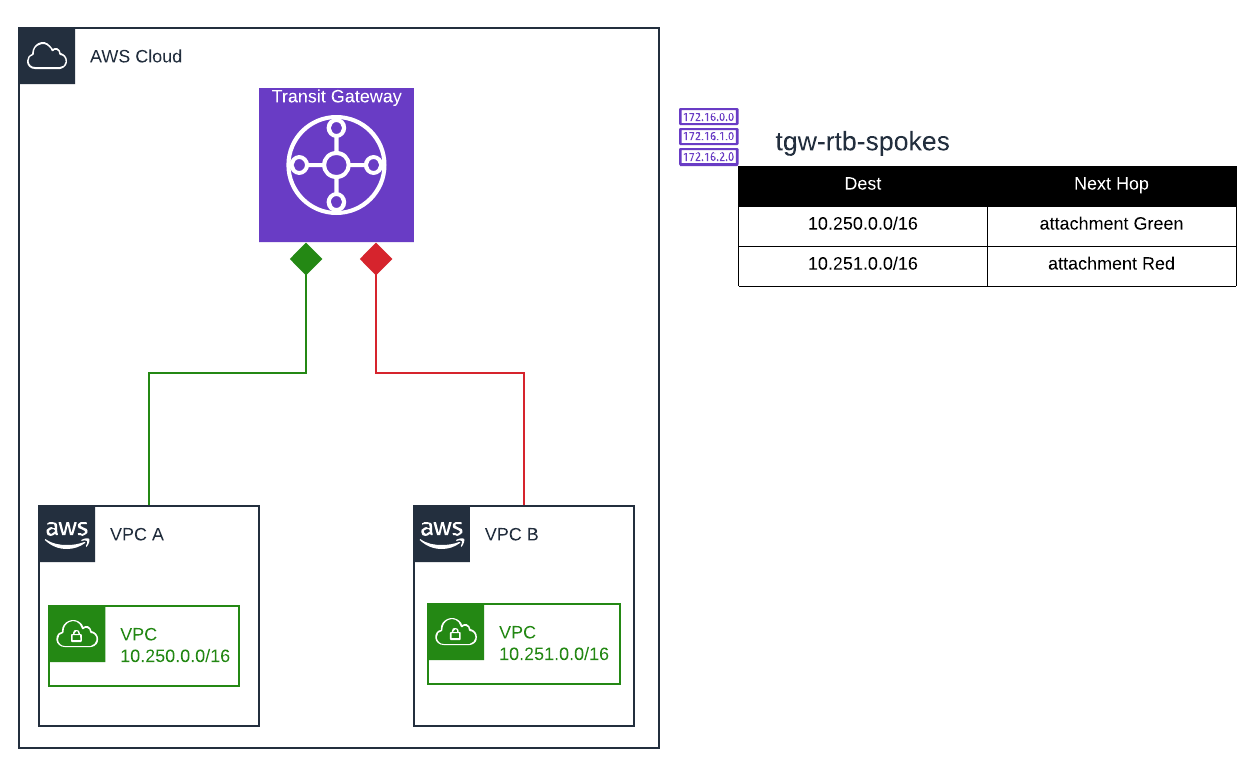
By the end of this step, the VPCs should look like this:
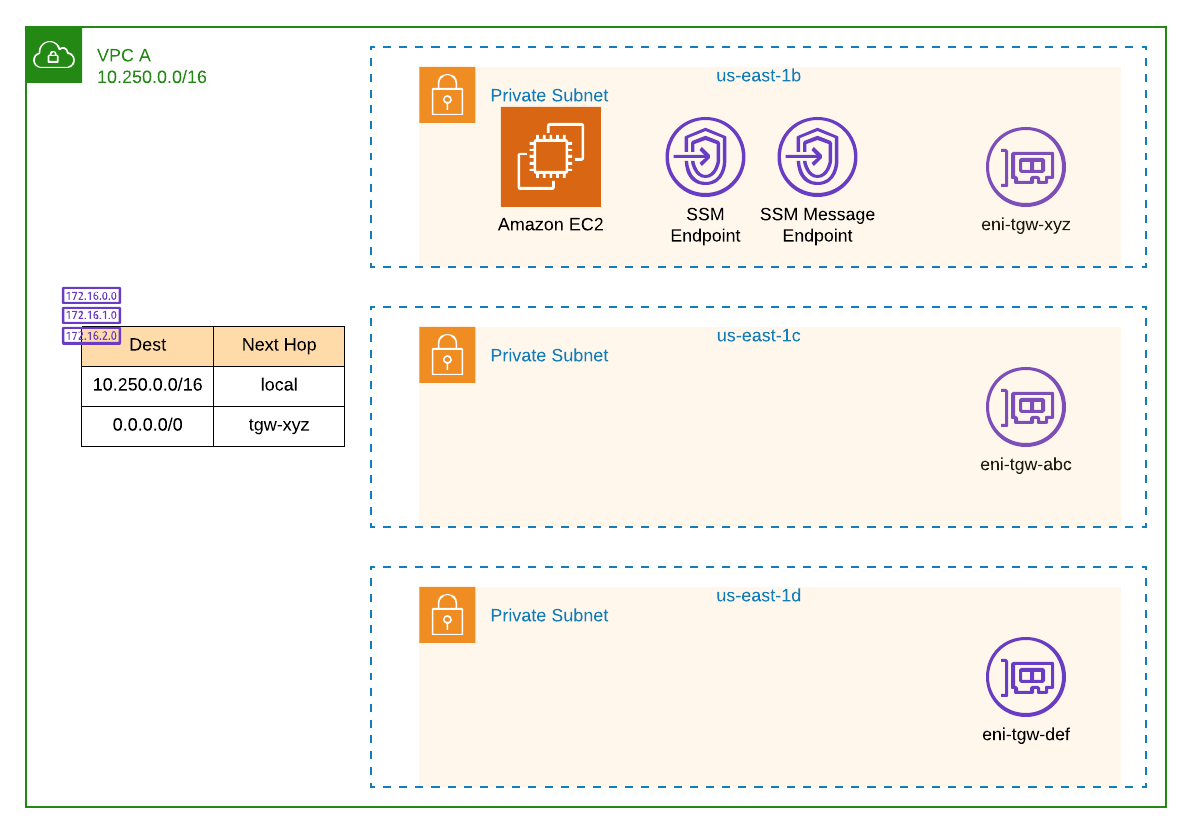
VPC A will look similar to:
- From the Services dropdown, go to CloudFormation.
- Click on the stack for VPC A. If you followed the steps above, this should be
bidmc-poc-vpc-a. - Click the Update button.
- With Use current template selected, click Next.
- Change the value of
AttachToTransitGatewayto true. - Change the value of
ConnectToSpokeVpcto true. - Click Next.
- Click Next.
- Select the checkbox to acknowledge creation of IAM resources, and click Update stack.
- Repeat steps 2-9 but for VPC B, or stack
bidmc-poc-vpc-b.
Once complete, you should now have attached the VPCs to the Transit Gateway and updated the rtb-spokes route table with each of the VPC's CIDR range. Additionally, a new default route should have been added to each VPC that specifies the Transit Gateway as the next hop.
With the Transit Gateway connectivity in place, let's delete the VPC peering stack and ensure the connectivity remains.
- From the Services dropdown, go to CloudFormation.
- Find the stack named
bidmc-poc-peering. Select it and click the Delete button. - Jump back to the Session Manager window and ensure the ping is still running. If so, success!
We have now proven connectivity between the two VPCs exist, and we successfully continuted that connectivity from an existing VPC peering connection to a Transit Gateway.