Continuous reconnaissance and vulnerability assessment using GitHub Actions
- Free 2000 minutes/month of cloud scans.
- Fully automated and simple to deploy
- Continuous scheduled scans & monitoring of assets
- Integrate any tool of your choice in workflow
- Native git diff support for change visualization
- Create a new private repository from here with name
pd-actions - Execute below commands, make sure to update
USER_NAMEwith your GitHub username.
▶ git clone --bare https://github.com/projectdiscovery/pd-actions.git; cd pd-actions.git
▶ git push --mirror https://github.com/USER_NAME/pd-actions.git- Update
input/domains.txtwith the target of your interest. - Make required changes in
.github/workflows/pd-actions.yaml - Now you will be able to see the "pd-actions" under Actions tab in your repository.
For running continuous periodic scan, remove the below comments form your actions file.
name: pd-actions
on:
# schedule:
# - cron: '0 0 * * *'
workflow_dispatch:As default, scans are scheduled to run at 12 AM on daily basis, you can update schedule and flag values of various tools as per your need in .github/workflows/pd-actions.yaml file on your forked version.
|
You can configure keys for sources to use in subfinder in To send output from any project directly to Slack, Discord, Telegram, add/update notify flags in the |
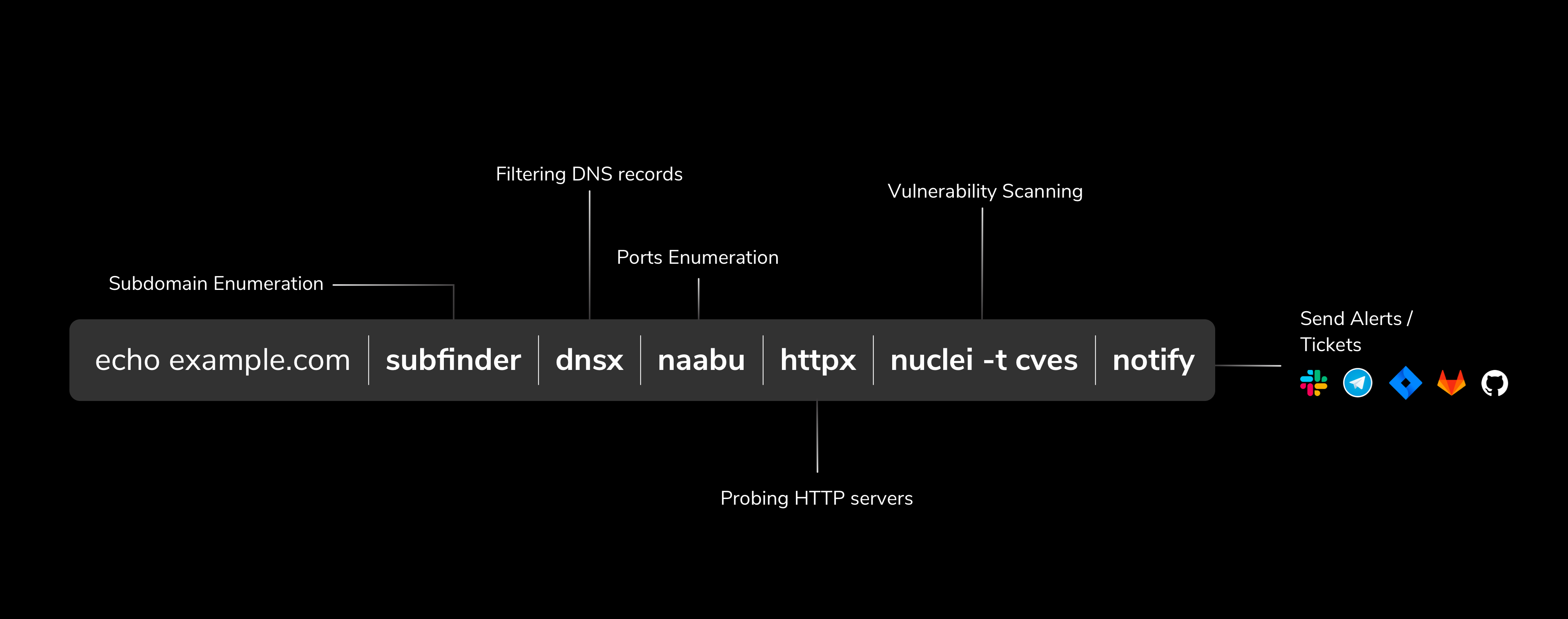
As described in the picture, PD action workflow takes root domain as input from input/domains.txt file,
- Performs passive subdomain enumeration using SubFinder
- Filter the inactive / invalid subdomains using dnsx
- Performs port scan for top 100 ports using Naabu
- Run HTTP webserver probing on the discovered ports using httpx
- Run CVEs based various nuclei templates using Nuclei
- Send alerts to Slack,Discord,Telegram using Notify - (Optional)
- Create tickets for bugs found using Nuclei on Github,Gitlab,Jira - (Optional)
Results from each tool stored in the output/ directory, upon changes after each scan you can also view the all changes using built in git diff UI and CLI.
You can always tweak the flags from each project as per your need directly at .github/workflows/pd-actions.yaml.
Checkout our blog-post https://blog.projectdiscovery.io/github-actions-for-application-security/ for a detailed breakdown of PD actions workflow and steps to write your own custom workflow using Github actions, PD actions is an idea to showcase utilization of GitHub Actions for Application security automation, you can do a lot of things with your custom workflows and tooling.
We have also added a few example workflows to run individual projects, we will add more workflows example to cover different use cases to improve security of organization, if you got more workflows example to share with community? please don't hesitate to open a PR 😄
|
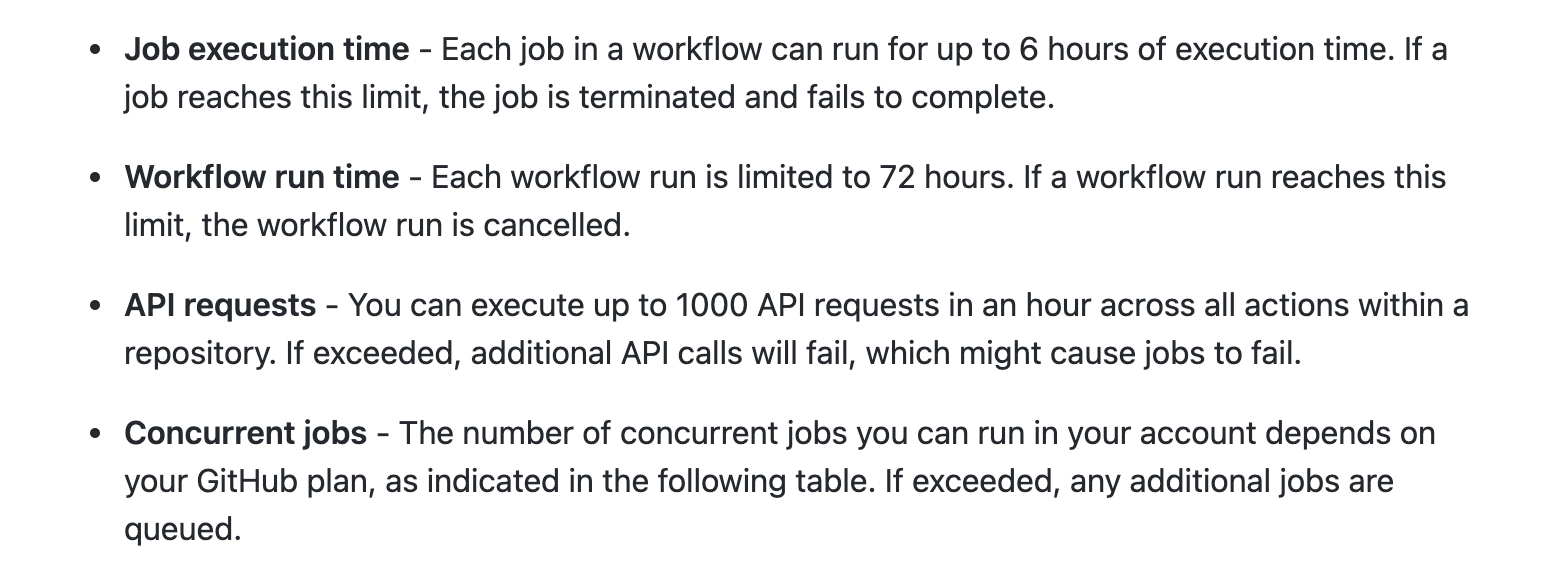
GitHub free account comes with 2000 minutes/month of free scans, making it practically free to run your continuous scans in the cloud. Few noticeable limits that are worth mentioning are listed below.