A GitHub Action for using Mayhem for Code to check for reliability, performance and security issues in your application binary (packaged as a containerized Docker image).
🧪 Modern App Testing: Mayhem for Code is an application security testing tool that catches reliability, performance and security bugs before they hit production.
🧑💻 For Developers, by developers: The engineers building software are the best equipped to fix bugs, including security bugs. As engineers ourselves, we're building tools that we wish existed to make our job easier!
🤖 Simple to Automate in CI: Tests belong in CI, running on every commit and PRs. We make it easy, and provide results right in your PRs where you want them. Adding Mayhem for Code to a DevOps pipeline is easy.
Want to try it? Get started for free today!
To use the Mayhem for Code GitHub Action, perform the following steps:
-
Navigate to mayhem.forallsecure.com to register an account.
-
Create a
mayhem.ymlfile in your GitHub repository located at:.github/workflows/mayhem.yml
🤔 Still need some help? Take a look at our working mCode Action examples at: https://github.com/forallsecure/mcode-action-examples.
Your mayhem.yml file should look like the following:
name: Mayhem
on:
push:
pull_request:
workflow_dispatch:
env:
REGISTRY: ghcr.io
IMAGE_NAME: ${{ github.repository }}
jobs:
build:
name: '${{ matrix.os }} shared=${{ matrix.shared }} ${{ matrix.build_type }}'
runs-on: ${{ matrix.os }}
strategy:
matrix:
os: [ubuntu-latest]
shared: [false]
build_type: [Release]
include:
- os: ubuntu-latest
triplet: x64-linux
steps:
- uses: actions/checkout@v2
- name: Log in to the Container registry
uses: docker/login-action@f054a8b539a109f9f41c372932f1ae047eff08c9
with:
registry: ${{ env.REGISTRY }}
username: ${{ github.actor }}
password: ${{ secrets.GITHUB_TOKEN }}
- name: Extract metadata (tags, labels) for Docker
id: meta
uses: docker/metadata-action@98669ae865ea3cffbcbaa878cf57c20bbf1c6c38
with:
images: ${{ env.REGISTRY }}/${{ env.IMAGE_NAME }}
- name: Build and push Docker image
uses: docker/build-push-action@ad44023a93711e3deb337508980b4b5e9bcdc5dc
with:
context: .
push: true
tags: ${{ steps.meta.outputs.tags }}
labels: ${{ steps.meta.outputs.labels }}
- name: Start analysis
uses: ForAllSecure/mcode-action@v1
with:
args: --image ${{ steps.meta.outputs.tags }}
sarif-output: sarif
- name: Upload SARIF file(s)
uses: github/codeql-action/upload-sarif@v1
with:
sarif_file: sarifThe mCode Action accepts the following inputs:
| Required | Input Name | Type | Description | Default |
|---|---|---|---|---|
mayhem-url |
string | Path to a custom Mayhem for Code instance. | https://mayhem.forallsecure.com | |
mayhem-token |
string | Mayhem for Code account token. Only required if overriding mayhem-url |
||
args |
string | Additional CLI override arguments such as specifying the --tests directory path for a seed test suite |
||
sarif-output |
string | Path for generating a SARIF report output file |
📖 See the CI/CD docs for more information and guides on using the mCode GitHub Action!
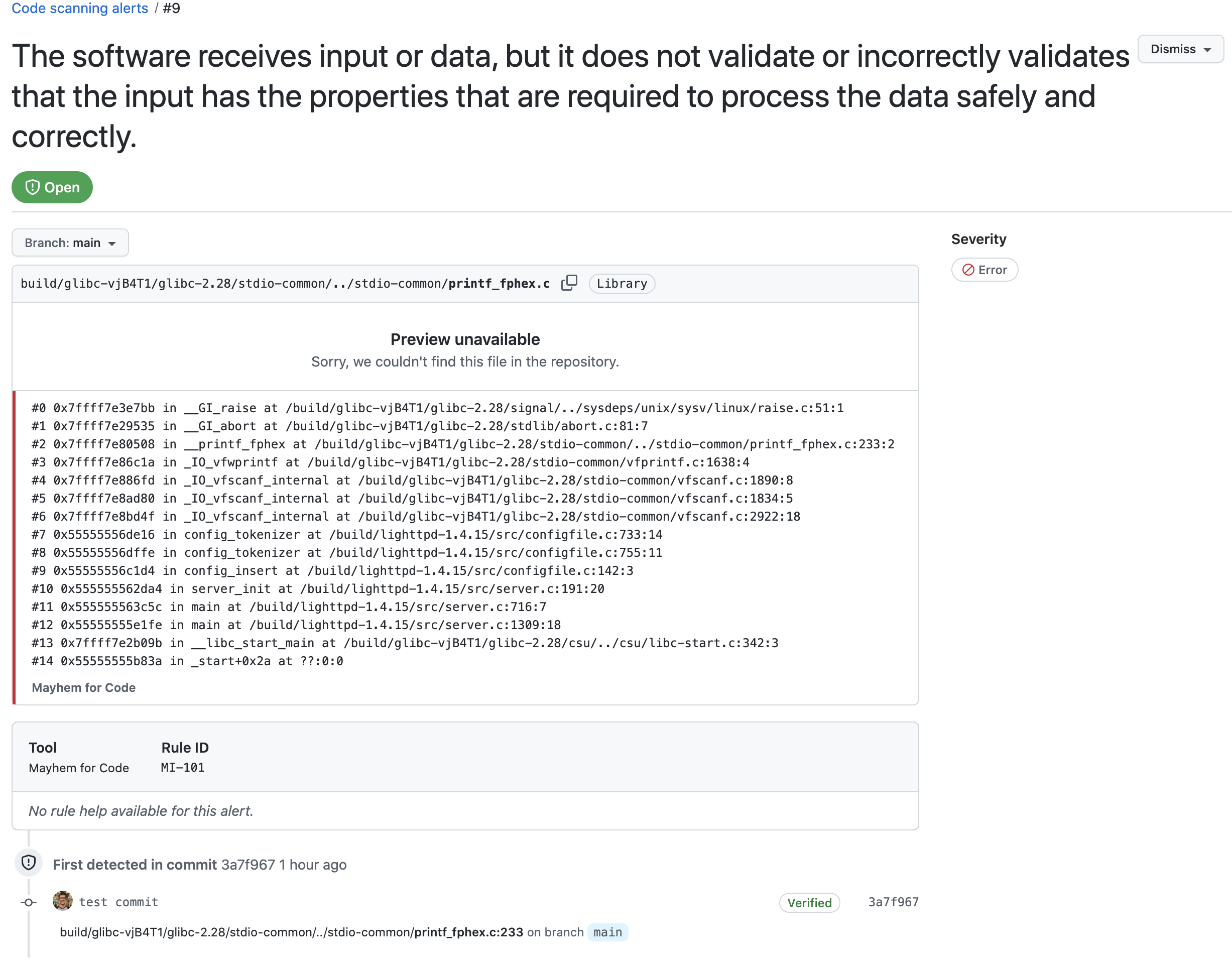
Mayhem for Code generates SARIF reports for your application security testing results.
SARIF reports are generated using the sarif-output parameter, which specifies an output file path.
To upload the SARIF report to GitHub, use the github/codeql-action/upload-sarif@v1 action with the sarif_file parameter to specify the location of a path containing SARIF results to upload to GitHub.
- name: Start analysis
uses: ForAllSecure/mcode-action@v1
with:
args: --image ${{ steps.meta.outputs.tags }}
sarif-output: sarif
- name: Upload SARIF file(s)
uses: github/codeql-action/upload-sarif@v1
with:
sarif_file: sarifOnce uploaded to GitHub, you can view test results in the Security tab of your repository as well as for your individual pull requests.
Fork this repository and modify the main.ts file. Then, re-compile the mCode GitHub Action by executing the following commands at the root of your forked repository:
Note: You will have to install
npmandyarn. See the official documentation for more info.
yarn run build && yarn run packageFinally, submit a pull request for your changes from your forked repository to this repository and we'll review!
ForAllSecure was founded with the mission to make the world’s critical software safe. The company has been applying its patented technology from over a decade of CMU research to solving the difficult challenge of making software safer. ForAllSecure has partnered with Fortune 1000 companies in aerospace, automotive and high-tech industries, as well as the US Department of Defense to integrate Mayhem into software development cycles for continuous security. Profitable and revenue-funded, the company is scaling rapidly.