This is a finding for address randomization. There could be no gap between the bss segment and the heap area.
It's not a secure design since people can overflow from bss to heap and partially write important data on the tcache management structure.
We can brute force 0x2000 times (ideally) to perform BeapOverflow.
But we need to overflow at least more than one page on bss, which is rare.
I reported this issue to linux kernel security team and this issue is fixed at this commit
But the .bss can still connect to the heap. The chance is 1024/1G, which is too small to exploit in most case
unsigned long arch_randomize_brk(struct mm_struct *mm)
{
- return randomize_page(mm->brk, 0x02000000);
+ if (mmap_is_ia32())
+ return randomize_page(mm->brk, SZ_32M);
+
+ return randomize_page(mm->brk, SZ_1G);
}
- Compile the c coude: main.c
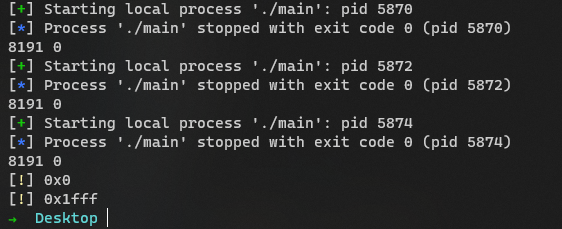
- Run the Python script several times to see the range of the offset: exp.py
0 - 0x1fff
I located the file after reading this article and the source code confirmed the correctness of my code:
https://elixir.bootlin.com/linux/v6.8/source/arch/x86/kernel/process.c#L1031
Still using x86's value(0x2000) even though we have more space.