Proof of concept demonstrating how to sign data using Azure Key Vault (.NET SDK) and how to verify this signature locally, without calling the Key Vault service again.
There are two variants of this implementation:
- The Key Vault SDK has added the capability to provide cached
JsonWebKeyto theCryptographyClientand make it work locally. It is currently available in version 4.2.0-beta.- As an alternative, we provide "manual" signature verification, using
RSAPKCS1SignatureDeformatter.
Follow the Getting started - Create/Get credentials steps described in the Key Vault .NET SDK documentation to set up the application.
High-level initialization steps:
- Create Azure Key Vault resource.
- Create service principal for this application.
az ad sp create-for-rbac -n <your-application-name> --skip-assignment
- Set
AZURE_CLIENT_ID,AZURE_CLIENT_SECRET, andAZURE_TENANT_IDappropriately. - Grant the service principal authorization to perform key operations on the Key Vault.
az keyvault set-policy --name <your-key-vault-name> --spn <AZURE_CLIENT_ID> --key-permissions backup delete get list create encrypt decrypt update sign verify
- Create a Key in Azure Key Vault.
- Update
keyVaultNameandkeyNameconstants inSigningController.csto your respective resource names.
Once this configuration is done, you should be able to start the app and navigate to API endpoints.
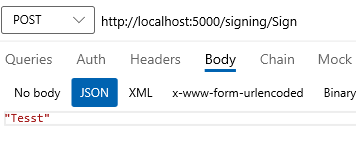
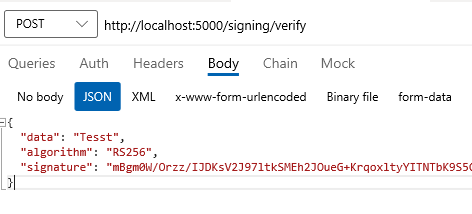
POST http://localhost:5000/signing/sign- This endpoint expects simple string body with content type of "application/json".POST http://localhost:5000/signing/verify- This endpoint expects JSON object containingdata,algorithmandsignature.
First request to this API (for any of the operations) fetches the public portion of specified key from Azure Key Vault and caches it in memory.
The sign operation is then using the standard .NET SDK to generate a data signature using key stored in Azure Key Vault. The signing operation itself takes place outside of the application - in Key Vault.
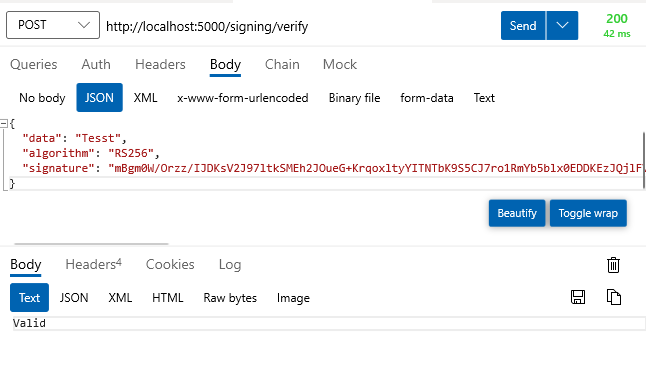
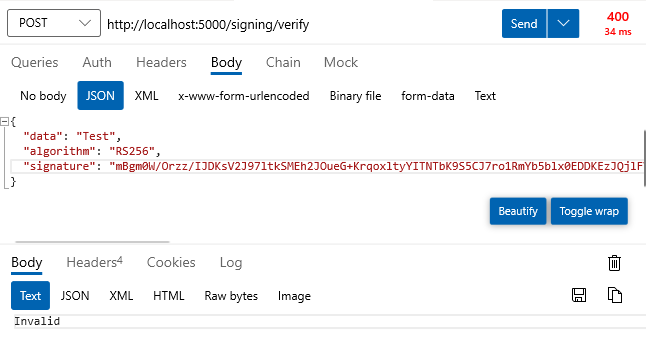
The verify operation doesn't reach out to Key Vault anymore, but uses the cached public key and .NET crypto APIs to validate signature of the provided data.