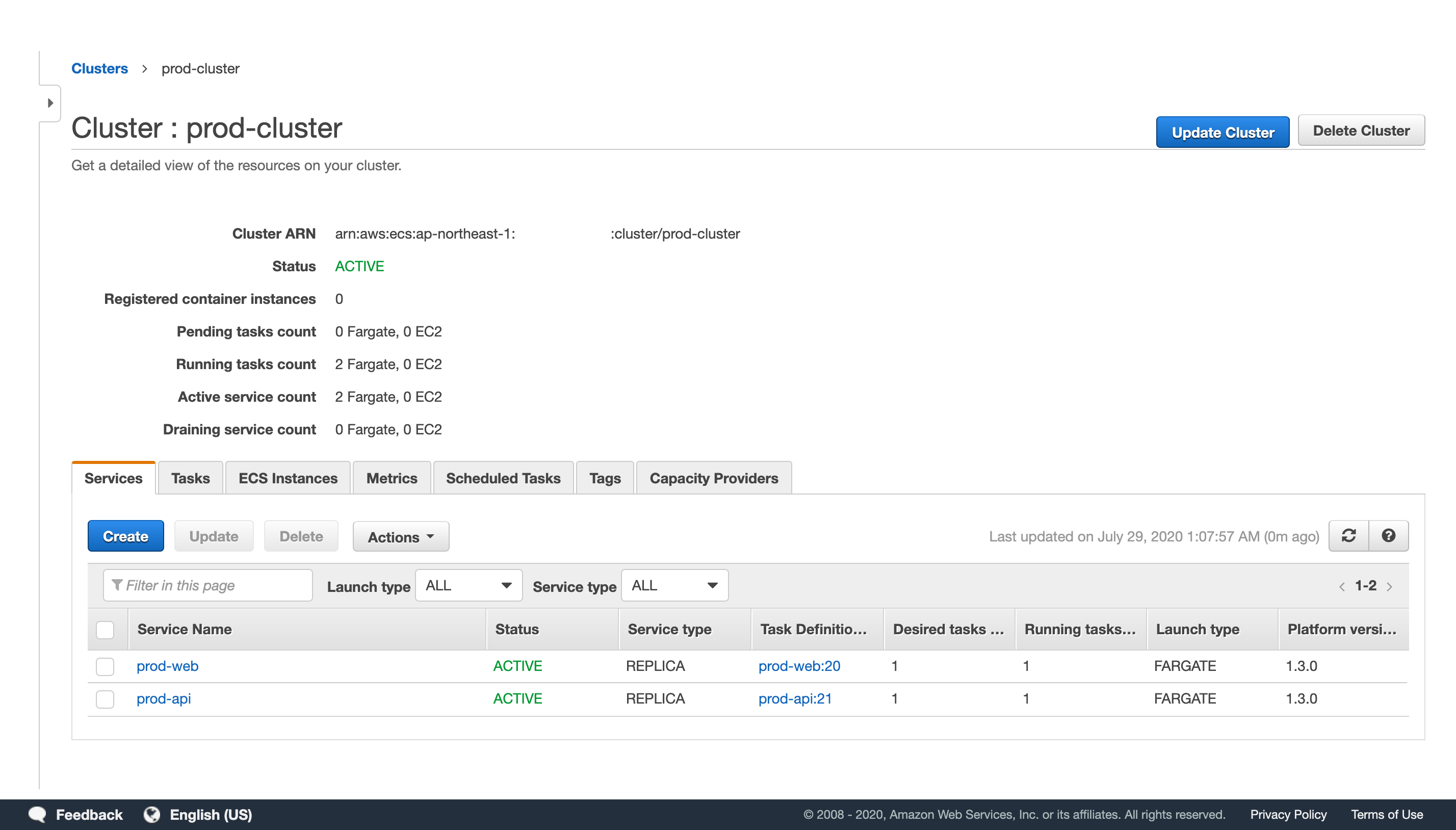
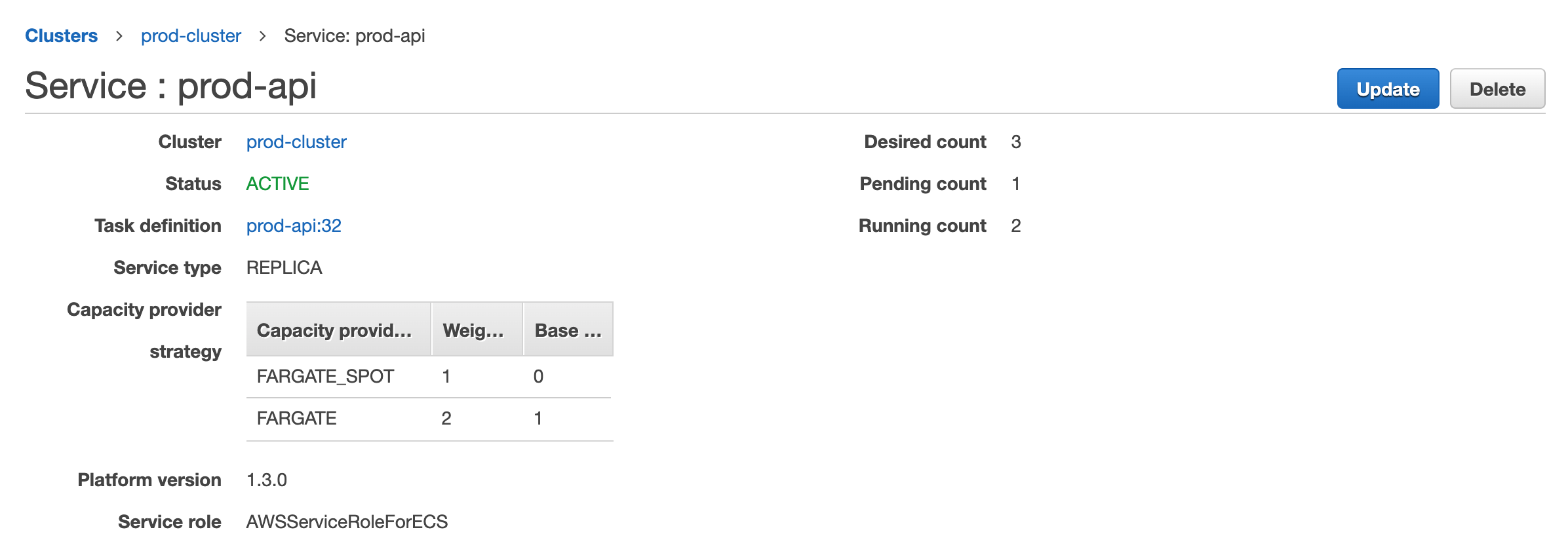
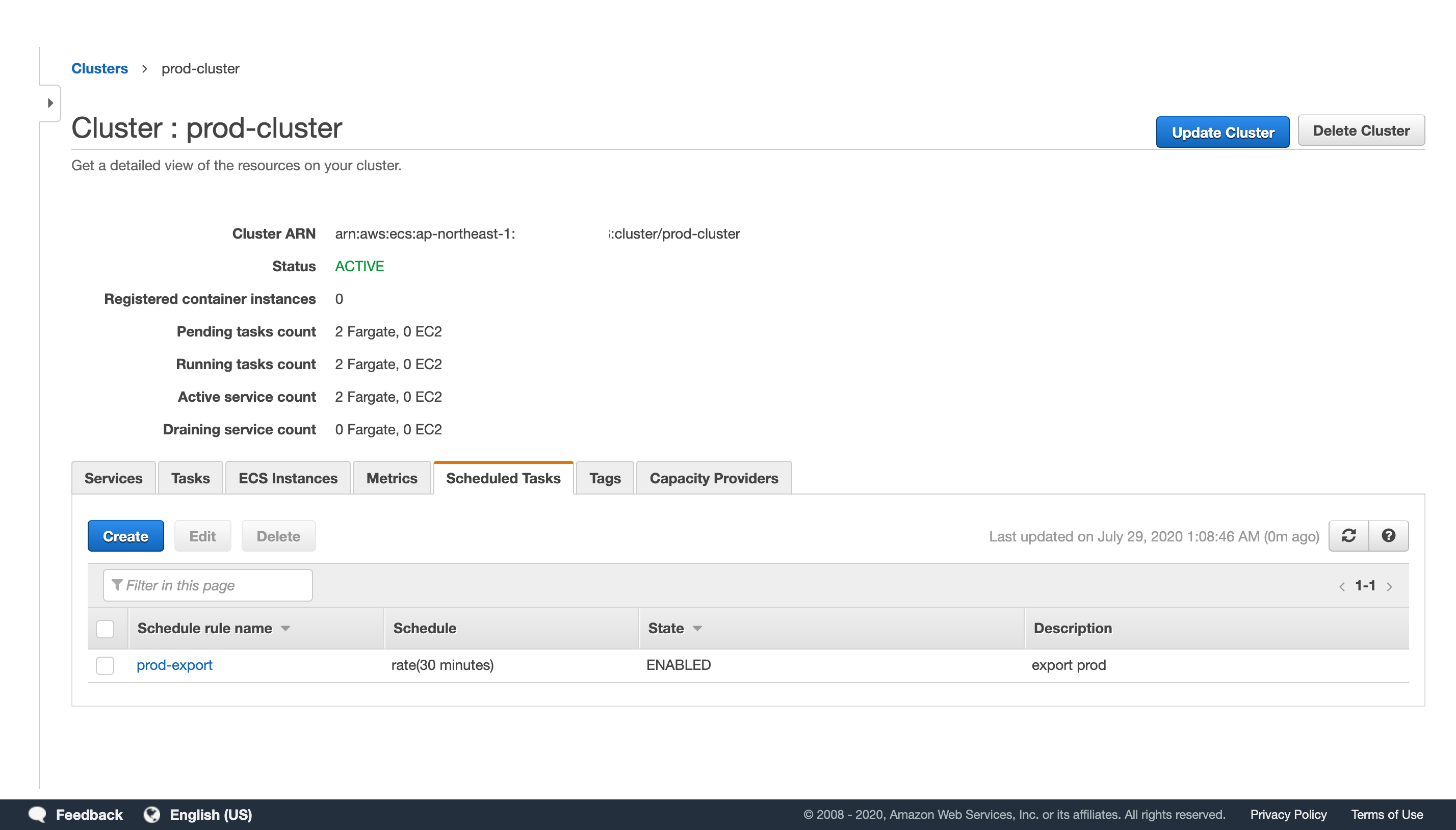
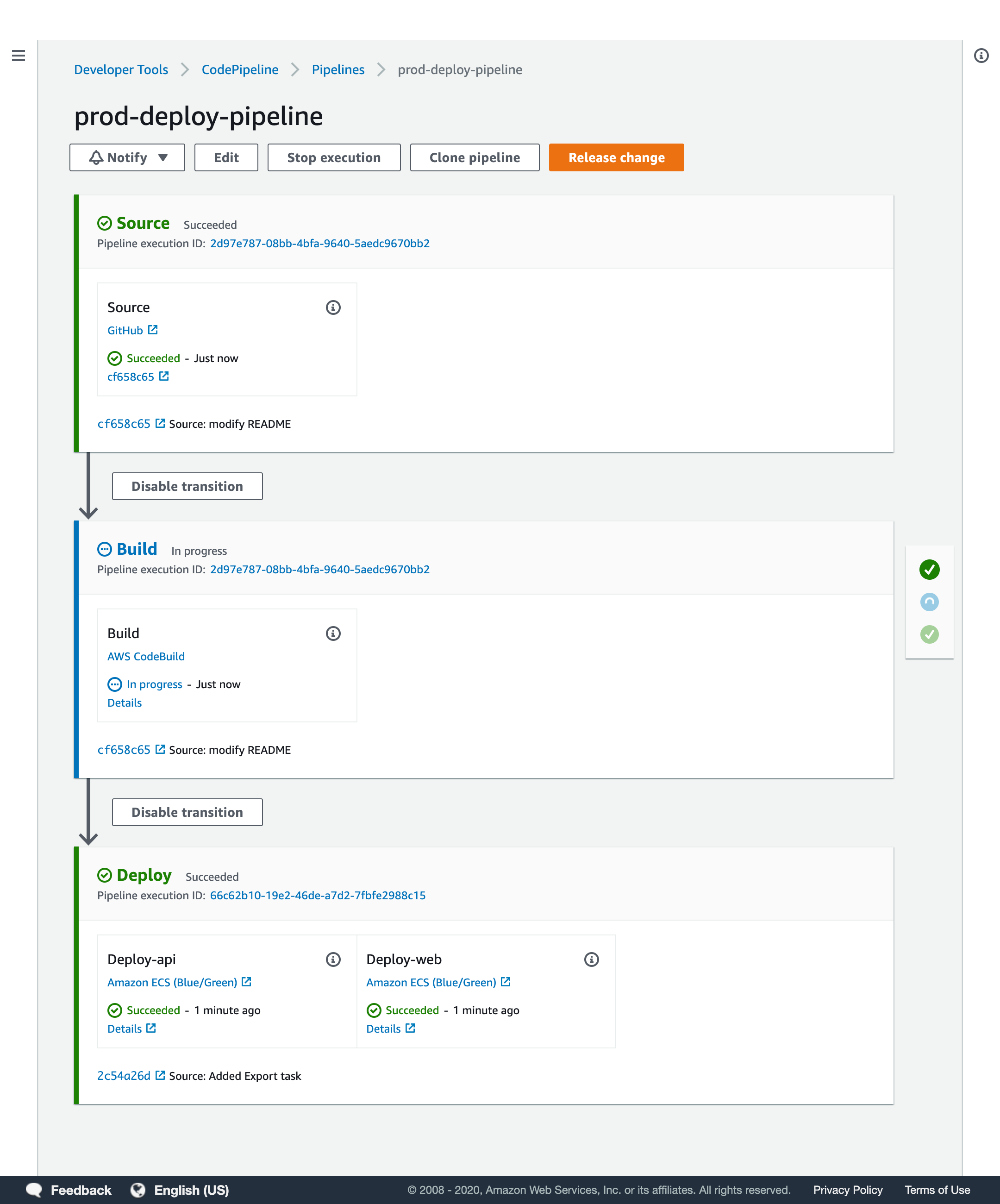
This is a terraform configuration for deploying a sample Rails application mpon/rails-blog-example in Fargate.
This repository is just an example, but we are aiming for a level that can be used even for production operations, and to complete the CI/CD only with AWS services, also without using shell like sed to replace image tag.
You can use this repository to try creating your own AWS infrastructure!
- VPC
- ECS on Fargate and Fargate Spot with capacity provider
- ECS Application Auto Scaling by Target Tracking Scaling Policies
- ECS Scheduled Task
- CodePipline triggerd by GitHub
- CodeBuild
- CodeDeploy with B/G Deployments
- RDS
.
└── terraform
├── common # resources that exist throught account, like a iam, ecr registry etc.
│ ├── main.tf # provider, terraform backend settings etc.
│ ├── outputs.tf # to use value from another terraform.state
│ └── variables.tf # for constant variables
├── dev # development environments
├── stg # staging environments
├── prod # production environments
└── modules # terraform module# You can set any region
export AWS_DEFAULT_REGION=ap-northeast-1
# S3 bucket to be used by Terraform remote backend
export TF_VAR_remote_backend=<your s3 bucket>
# GitHub personal token to be used by github provider
export GITHUB_TOKEN=***********************
# Configure aws-cli.
# We have not confirmed the minimum policy, it works AdministratorAccess at least.
# NOTE: In production environments, you have to reduce policy.
aws configureaws s3api create-bucket --bucket $TF_VAR_remote_backend --region $AWS_DEFAULT_REGION \
--create-bucket-configuration LocationConstraint=$AWS_DEFAULT_REGION
aws s3api put-bucket-versioning --bucket $TF_VAR_remote_backend --versioning-configuration Status=EnabledWe have to create ECR, IAM, and so on first. This output value will be used by another environments.
cd terraform/common
make init
make plan
make applyNext, create some environments. If you would fail to apply, please retry once or twice.
cd terraform/stg # also terraform/prod
make init
make plan
make applyThen, it shows ALB DNS name in terminal, you can access it. At the same time, CodePipeline will be started and deploy rails application after a while.
cd terraform/stg
terraform destroy
cd terraform/prod
terraform destroy
cd terraform/common
terraform destroy- push
stagingbranch in mpon/rails-blog-example - start staging CodePipeline
- start CodeBuild
- build docker image and push ECR
- migrate database
- sync assets
- get files to deploy ECS from S3 (taskdef, appspec)
- start CodeDeploy B/G Deployments
- push
masterbranch in mpon/rails-blog-example - start production CodePipeline
- start CodeBuild
- build docker image and push ECR
- migrate database
- sync assets
- get files to deploy ECS from S3 (taskdef, appspec)
- start CodeDeploy B/G Deployments
- Use HTTPS listener
- Set enable_deletion_protection of ALB to true
- Set force_destroy of S3 bucket to false
- Change RDS username/password
- Change resource name using random_pet that makes it unique in this example