ObjectivePGP is an implementation of OpenPGP protocol for iOS and macOS. OpenPGP is the most widely used email encryption standard. It is defined by the OpenPGP Working Group of the Internet Engineering Task Force (IETF).
Here is the blog post story.
target 'MyTargetName' do
use_frameworks!
pod 'ObjectivePGP'
endObjectivePGP comes with the Frameworks for the latest release.
- Download ObjectivePGP.framework or build a framework with the build-frameworks.sh script.
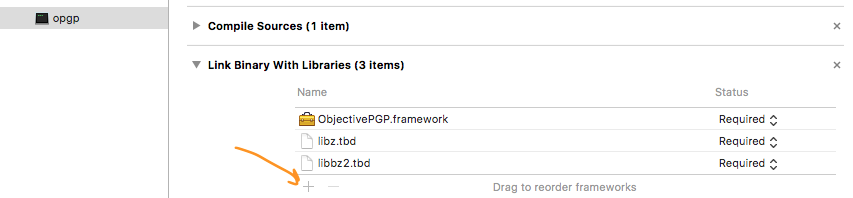
- Link framework with the target
- Link libraries and frameworks
- Add
Security.frameworkto "Link Binary With Libraries" list for the target. These are system libraries. - Add
libzandlibbz2to "Link Binary With Libraries" list for the target. These are system libraries.
- Add
- In the Build Phases tab, click the + button at the top and select “New Run Script Phase”. Enter the following code into the script text field:
bash "${BUILT_PRODUCTS_DIR}/${FRAMEWORKS_FOLDER_PATH}/ObjectivePGP.framework/strip-frameworks.sh"(The last step, is required for working around an iOS App Store bug when archiving universal binaries.)
You are welcome to contribute. Please create Pull Request against develop branch.
#import <ObjectivePGP/ObjectivePGP.h>
ObjectivePGP *pgp = [[ObjectivePGP alloc] init];/* Load keys from a keyring file */
NSArray *keys = [ObjectivePGP readKeysFromFile:@"/path/to/secring.gpg"];
/* Load eys from a keys file */
NSArray *keys = [ObjectivePGP readKeysFromFile:@"/path/to/key.asc"];
/* Import keys */
[pgp importKeys:keys];
/* Import selected key from a keyring */
[pgp importKey:@"979E4B03DFFE30C6" fromFile:@"/path/to/secring.gpg"];
/* long identifier 979E4B03DFFE30C6 */
PGPKey *key = [pgp findKeyWithIdentifier:@"979E4B03DFFE30C6"];
/* Short identifier 979E4B03 (the same result as previous) */
PGPKey *key = [pgp findKeyWithIdentifier:@"979E4B03"];
/* First key that match given user identifier string. */
PGPKey *key = [pgp findKeysForUserID:@"Name <email@example.com>"];/* Export all public keys to file */
if ([pgp exportKeysOfType:PGPPartialKeyPublic toFile:@"pubring.gpg" error:nil]) {
// success
}
/* Export a key and save as armored (ASCII) file */
PGPKey *key = [self.pgp findKeyWithIdentifier:@"979E4B03DFFE30C6"];
NSData *armoredKeyData = [pgp exportKey:key armored:YES];
[armoredKeyData writeToFile:@"pubkey.asc" atomically:YES];NSData *fileContent = [NSData dataWithContentsOfFile:@"/path/file/to/data.txt"];
/* Choose a key to use to sign the data */
PGPKey *key = [self.pgp findKeyWithIdentifier:@"979E4B03DFFE30C6"];
/* Sign and return only a signature data (detached = YES) */
NSData *signature = [pgp sign:fileContent usingKey:key passphrase:nil detached:YES error:nil];
/* Sign and return a data with the signature (detached = NO) */
NSData *signedData = [pgp sign:fileContent usingSecretKey:key passphrase:nil detached:NO error:nil];/* embedded signature */
NSData *signedContent = [NSData dataWithContentsOfFile:@"/path/file/to/data.signed"];
if ([pgp verify:signedContent error:nil]) {
// Success
}
/* detached signature */
NSData *signatureContent = [NSData dataWithContentsOfFile:@"/path/file/to/signature"];
NSData *dataContent = [NSData dataWithContentsOfFile:@"/path/file/to/data.txt"];
if ([pgp verify:dataContent withSignature:signatureContent error:nil]) {
// Success
}NSData *fileContent = [NSData dataWithContentsOfFile:@"/path/plaintext.txt"];
/* Choose the public key to use to encrypt data. Must be imported previously */
PGPKey *key = [self.pgp findKeyWithIdentifier:@"979E4B03DFFE30C6"];
/* Encrypt data. Armor output (ASCII file) */
NSData *encryptedData = [pgp encrypt:fileContent usingKeys:@[key] armored:YES error:nil];
if (encryptedData) {
// Success
}
NSData *encryptedFileContent = [NSData dataWithContentsOfFile:@"/path/data.enc"];
/* If key is encrypted with the passphrase, you can provide a passphrase key here. */
NSData *decryptedData = [pgp decrypt:encryptedFileContent passphrase:nil error:nil];
if (decryptedData) {
// Success
}PGPKeyGenerator *generator = [[PGPKeyGenerator alloc] init];
PGPKey *key = [generator generateFor:@"Marcin <marcin@example.com>" passphrase:nil];
NSData *publicKeyData = [key export:PGPPartialKeyPublic error:nil];
NSData *secretKeyData = [key export:PGPPartialKeySecret error:nil];See CHANGELOG
Known limitations:
- Blowfish, Twofish and Elgamal are not supported.
- Missing external configuration for default values.
The ObjectivePGP stays under a dual license:
-
Free for non-commercial use, covered by the standard 2-clause BSD license. That means you have to mention Marcin Krzyżanowski as the original author of this code and reproduce the LICENSE text inside your app.
-
Commercial-use license to use in commercial products. Please bear in mind that some free products remain commercial products. Please contact me via email for details.
Not sure what to choose? check this thread
This product uses software developed by the OpenSSL Project for use in the OpenSSL Toolkit. (http://www.openssl.org/)