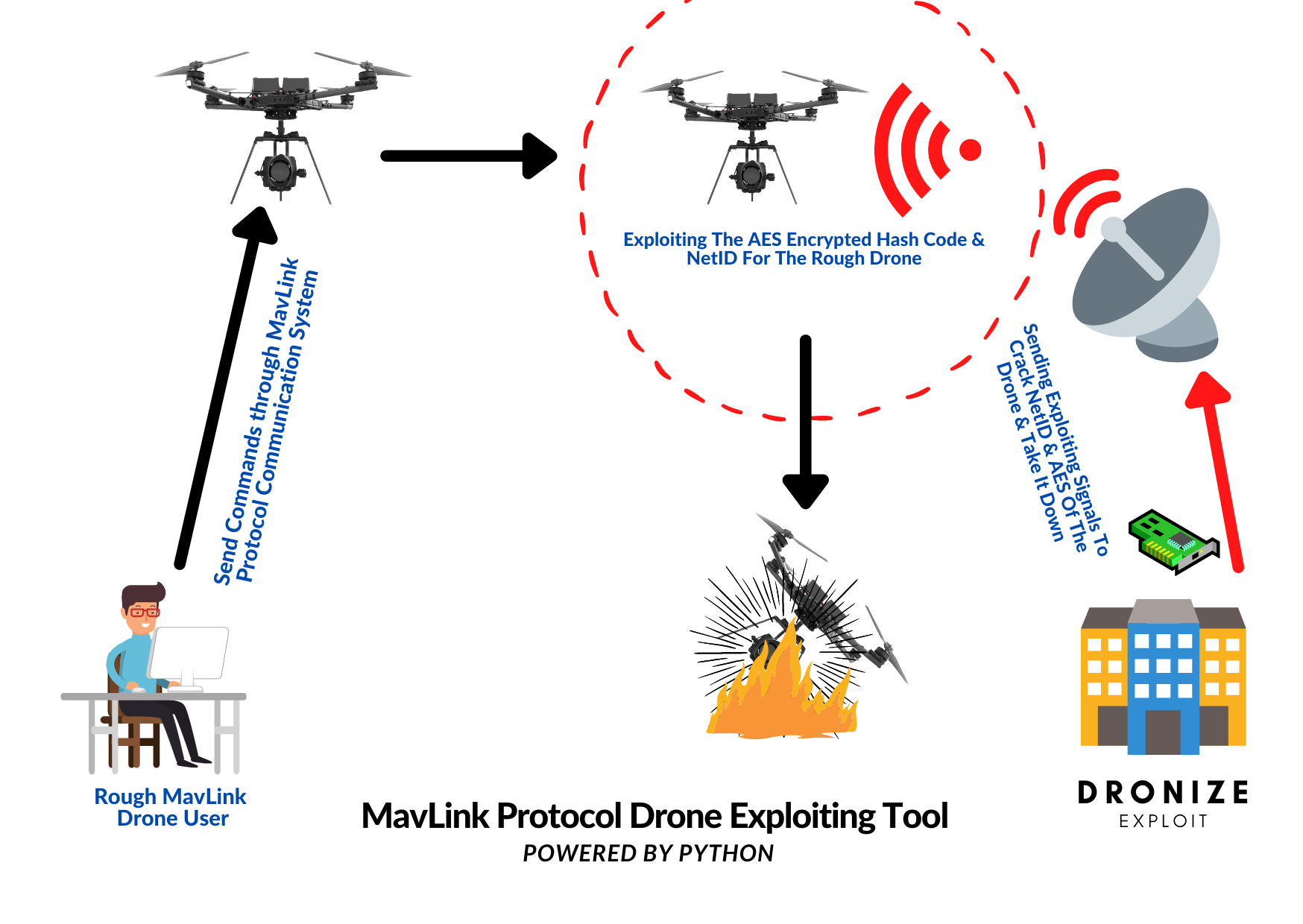
MavLink Protocol Drone Exploiting Tool
dronize-exploit is based on the concept of mimicking ID also called NetID codes in the Mavlink sik radio communication protocol to shut down the nearby drone within the range.
To use this software package you will need to buy a SiK Radio Telemetry Communication System, which can be purchased at online stores.
On the software side you will need Docker and a Unix based system like MacOs or Linux. Though this project is dockerized, it requires access to the /dev/ directory so dronize-exploit can automatically interact with your SiK radio.
Once you have Docker downloaded, you may need to use sudo, use this command to pull the image:
docker pull moayyad57/dronize-exploit Run this to launch the dronize-exploit system:
docker run -it --rm -v /dev/:/dev/ moayyad57/dronize-exploit Now plug the SiK or MavLink radio into any available usb port. Finnaly run this to start disarming any system in the area:
./start_disarming