This repository contains terraform code to deploy a sample architecture to try AWS Network Firewall. The resources deployed and the architectural pattern they follow is purely for demonstration/testing purposes. If you are looking for a set of approved architectures, read this blog post.
The image below is a graphical representation of what resources are defined in the Terraform code in this repository:
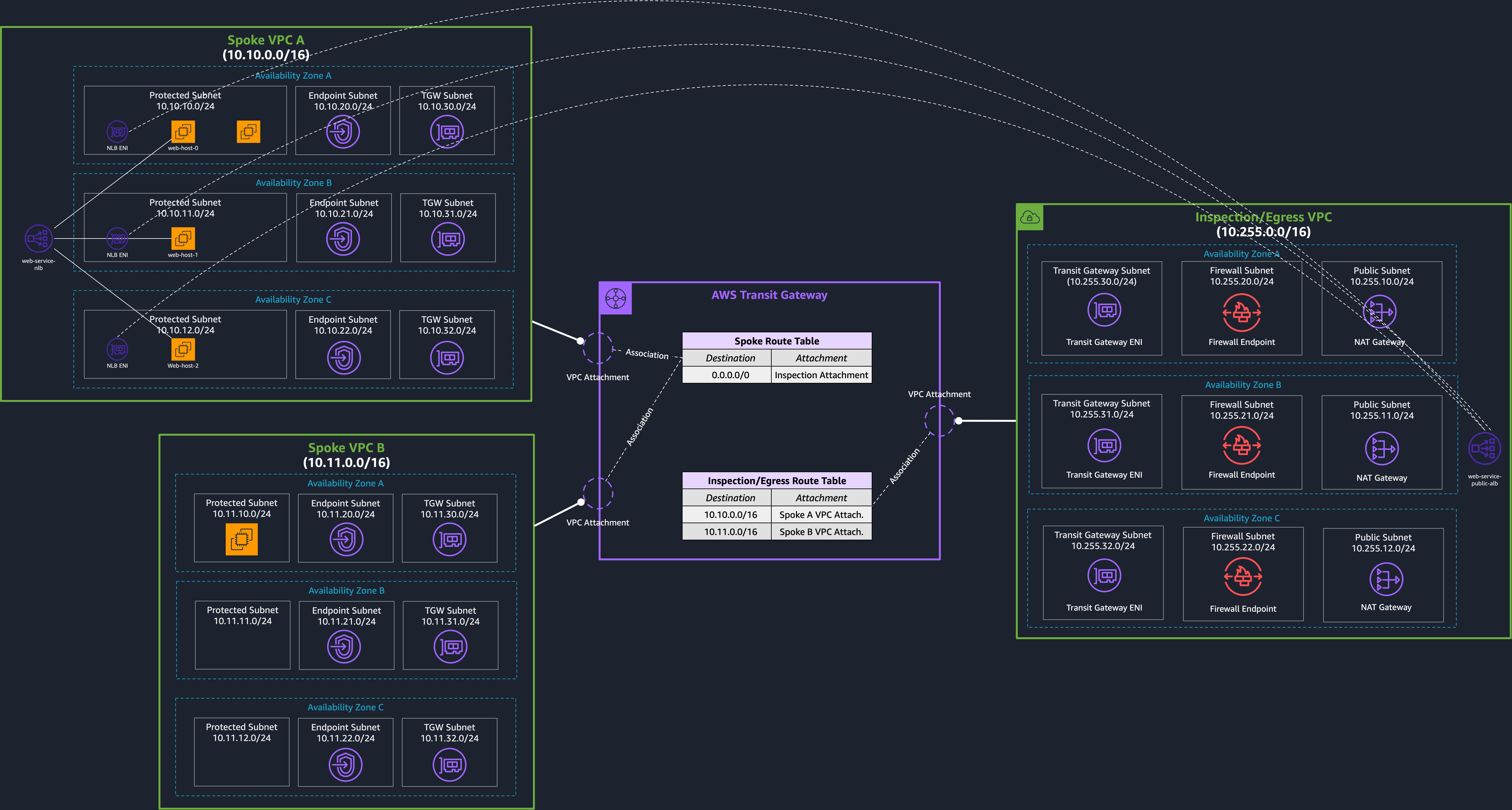
The templates deploy three VPCs (spoke-a, spoke-b, and inspection).
AWS Network Firewall endpoints are deployed in the Inspection VPC.
Internet egress is also configured in the inspection VPC, by deploying NAT Gateways in Public Subnets.
The template deploys two EC2 instances in spoke-vpc-a and spoke-vpc-b for testing purposes.
It also deploys resources so that connecting to these instances is enabled via AWS Systems Manager Session Manager.
The templates also deploy a webservice implemented by three EC2 instances web-host[1-3] in the spoke-a VPC, fronted by a private NLB.
Ingress is centralised in the inspection VPC by the use of a public ALB with an associated Target Group with the private IPs of the private NLB as targets.
The firewall.tf template file contains the definitions of the FW rule-groups that these templates come with by default.
The default action taken by the stateless engine is Forward to stateful rule groups.
Alert logs are persisted in a dedicated Cloudwatch Log Group (/aws/network-firewall/alert).
Flow logs are persisted in a dedicated S3 Bucket (network-firewall-flow-bucket-*).
The rule-groups configured in the policy are the following:
drop-icmp: this is a stateless rule group that drops all ICMP trafficdrop-non-http-between-vpcs: this stateful rules drops anything but HTTP traffic between spoke VPCs.block-domains: this stateful rule prevents any HTTP traffic to occur to two FQDNs specified in the rule itself.
The template deploys two instances in spoke-vpc-a and spoke-vpc-b in the protected subnets that you can use to test east-west connectivity (and north-south).
By default, the templates deploy in the eu-west-1 AWS Region.
If you wish to deploy in any other AWS Region, edit the corresponding setting in the provider.tf file.
- Install Terraform (0.14.6 or higher)
- Clone this repository
- Initialise Terraform
terraform init - Deploy the template with
terraform apply.
- try a ping between instances in
spoke-vpc-aandspoke-vpc-b: this shouldn't work - try to SSH to the EC2 Instance in
spoke-vpc-bfrom the EC2 Instance inspoke-vpc-a(or vice-versa): this shouldn't work - try to curl the private IP of the EC2 Instance in
spoke-vpc-bfrom the EC2 Instance inspoke-vpc-a(or vice-versa): this should work - try a ping to a public IP address: this shouldn't work
- try to
digusing a public DNS resolver: this shouldn't work - try to curl https://facebook.com or https://twitter.com: this shouldn't work
- try to curl any other public URL: this should work
- from any browser naviate to http://<public_alb_dns_name> where <public_alb_dns_name> is the DNS name of the ALB created by your Terraform code in the Inspection VPC.
Remember to clean up after your work is complete. You can do that by doing terraform destroy.
Note that this command will delete all the resources previously created by Terraform.
See CONTRIBUTING for more information.
This library is licensed under the MIT-0 License. See the LICENSE file.