Identity management system for ASP.NET Core Identity for use with ASP.NET Core 8 and developed with Blazor United to supersede the following projects:
- Identity Manager - ASP.NET Core 1, 2
- Identity Manager UI - ASP.NET Core 3, 5, 6
- Identity Manager Blazor - ASP.NET Core 7
When creating a new Blazor Web App you have the option to change the authentication type to individual accounts to include the identity system into your project. This includes registration, login and several pages related to user account self management like 2FA and password reset.
The missing piece to the puzzle is user management for the site. For ASP.NET membership there was ASP.NET Website Administration Tool (WSAT) and for ASP.NET Identity there was Identity Manager by Brock Allen. AFAIK there is no solution available for ASP.NET Core Identity so this repo is an effort to remedy that.
When creating a project choose the Blazor Web App template and select the Individual Accounts authentication type and WebAssembly for Interactive render mode.
In ApplicationUser you need to add the following properties.
public class ApplicationUser : IdentityUser
{
public ICollection<IdentityUserRole<string>> Roles { get; set; }
public ICollection<IdentityUserClaim<string>> Claims { get; set; }
}Similarily after creating ApplicationRole you need to add a property.
public class ApplicationRole : IdentityRole
{
public ICollection<IdentityRoleClaim<string>> Claims { get; set; }
}In Program you will have to include references to ApplicationUser and ApplicationRole that were added to the project.
builder.Services.AddIdentityCore<ApplicationUser>(options =>
{
options.SignIn.RequireConfirmedAccount = true;
})
.AddRoles<ApplicationRole>()
.AddEntityFrameworkStores<ApplicationDbContext>();In your ApplicationDbContext you need to define the following navigation properties.
public class ApplicationDbContext(DbContextOptions<ApplicationDbContext> options) : IdentityDbContext<ApplicationUser, ApplicationRole, string>(options)
{
protected override void OnModelCreating(ModelBuilder builder)
{
base.OnModelCreating(builder);
builder.Entity<ApplicationUser>().HasMany(p => p.Roles).WithOne().HasForeignKey(p => p.UserId).IsRequired().OnDelete(DeleteBehavior.Cascade);
builder.Entity<ApplicationUser>().HasMany(e => e.Claims).WithOne().HasForeignKey(e => e.UserId).IsRequired().OnDelete(DeleteBehavior.Cascade);
builder.Entity<ApplicationRole>().HasMany(r => r.Claims).WithOne().HasForeignKey(r => r.RoleId).IsRequired().OnDelete(DeleteBehavior.Cascade);
}
}After adding IdentityController you will need to add the following to Program.
builder.Services.AddControllers();
...
app.MapControllers();Added a reference to bootstrap-icons.min.css in App.razor for Bootstrap icons used in the project.
Sample pages for template did not include AccessDenied.razor so added under Components\Account\Pages folder.
Add the following package references to the project:
Microsoft.Extensions.Http
Microsoft.AspNetCore.Components.QuickGrid
You will also need to add the following to Program:
builder.Services.AddHttpClient("WebAPI", client => client.BaseAddress = new Uri(builder.HostEnvironment.BaseAddress));
builder.Services.AddScoped(sp => sp.GetRequiredService<IHttpClientFactory>().CreateClient("WebAPI"));In addition add the following components to the project:
Modal.razor
Roles.razor
Users.razor
The <_ExtraTrimmerArgs>--keep-metadata parametername</_ExtraTrimmerArgs> option was added to property group in csproj to prevent trimming parameter names for KeyValuePair constructor.
As the example project uses FileBaseContext as the database provider there is no database setup needed since the ASP.NET Identity Core tables are stored in files, however for your own project you should use a Database Provider to store these.
Run the project and you will be able to use the website to manage users, roles and claims. With the provided Identity tables stored as files you can login as admin@example.com with "Password".
The first thing that you will likely do is create a new administrator role to manage additional users.
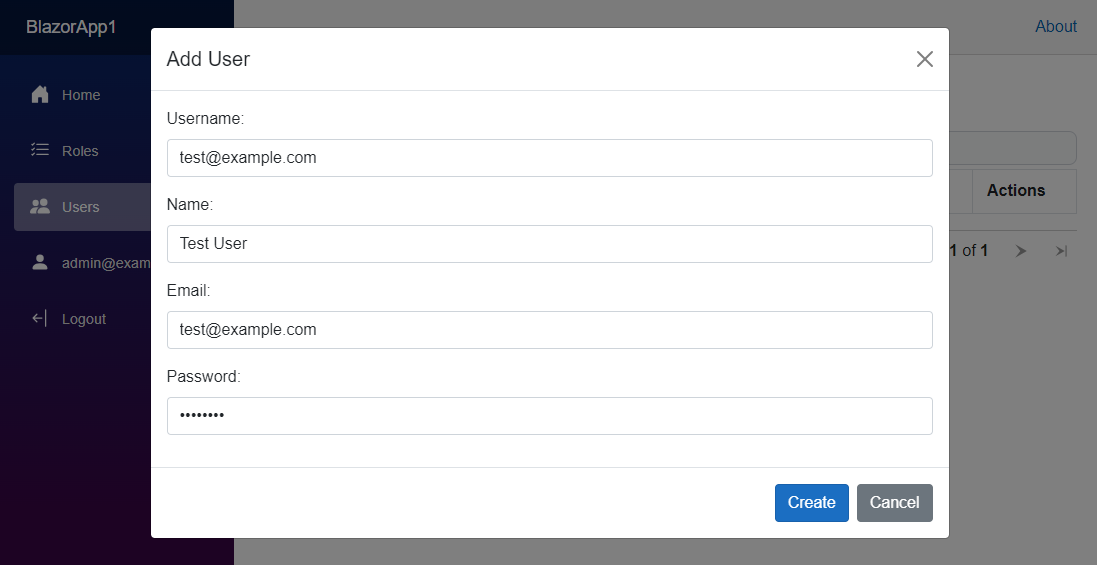
Once done you can create a new user by providing basic information like username and password.
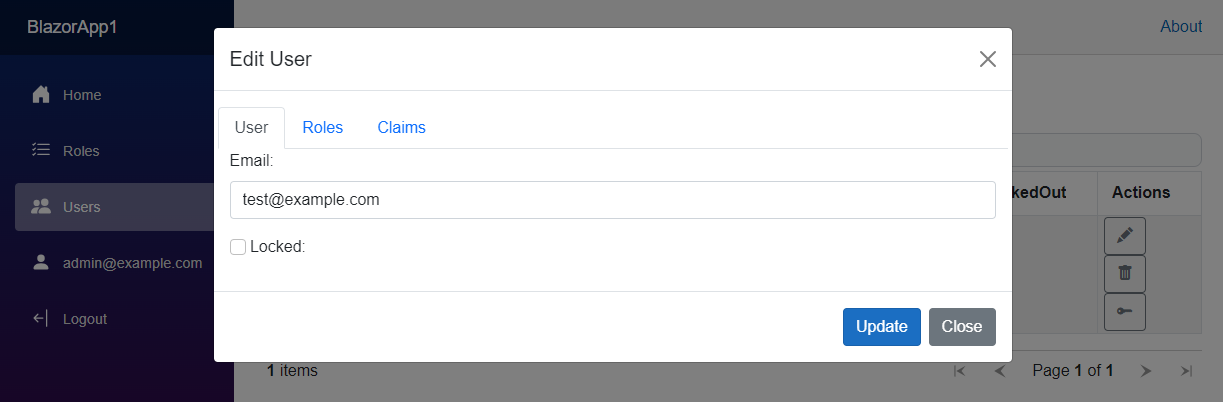
After the user has been created you can then edit email address and lock account if required.
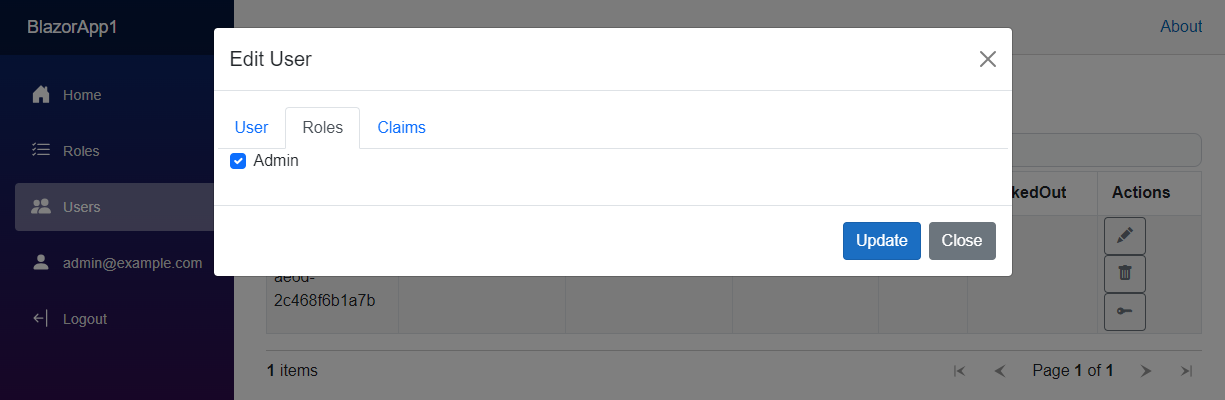
In the user edit dialog you can select the Roles tab to assign user to previously defined roles.
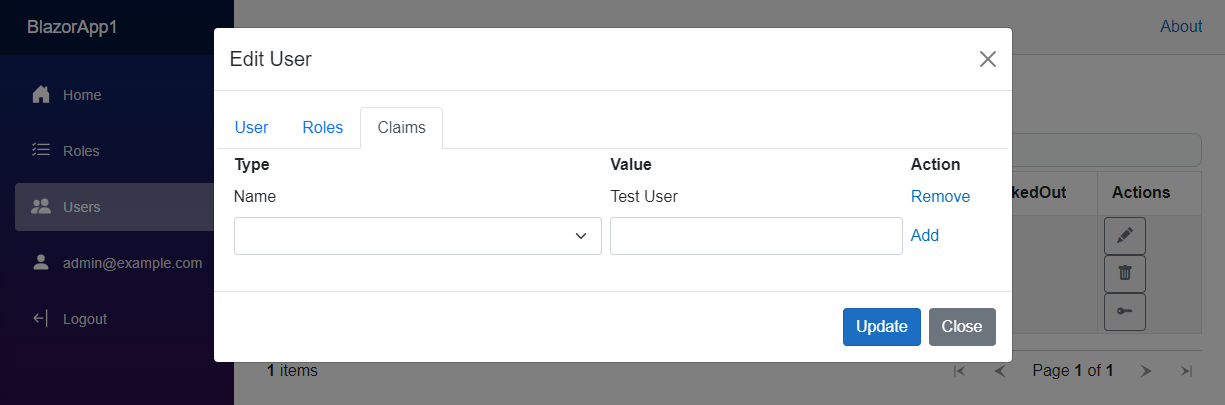
In addition you can also select the Claims tab to add or remove claims to the user being edited.