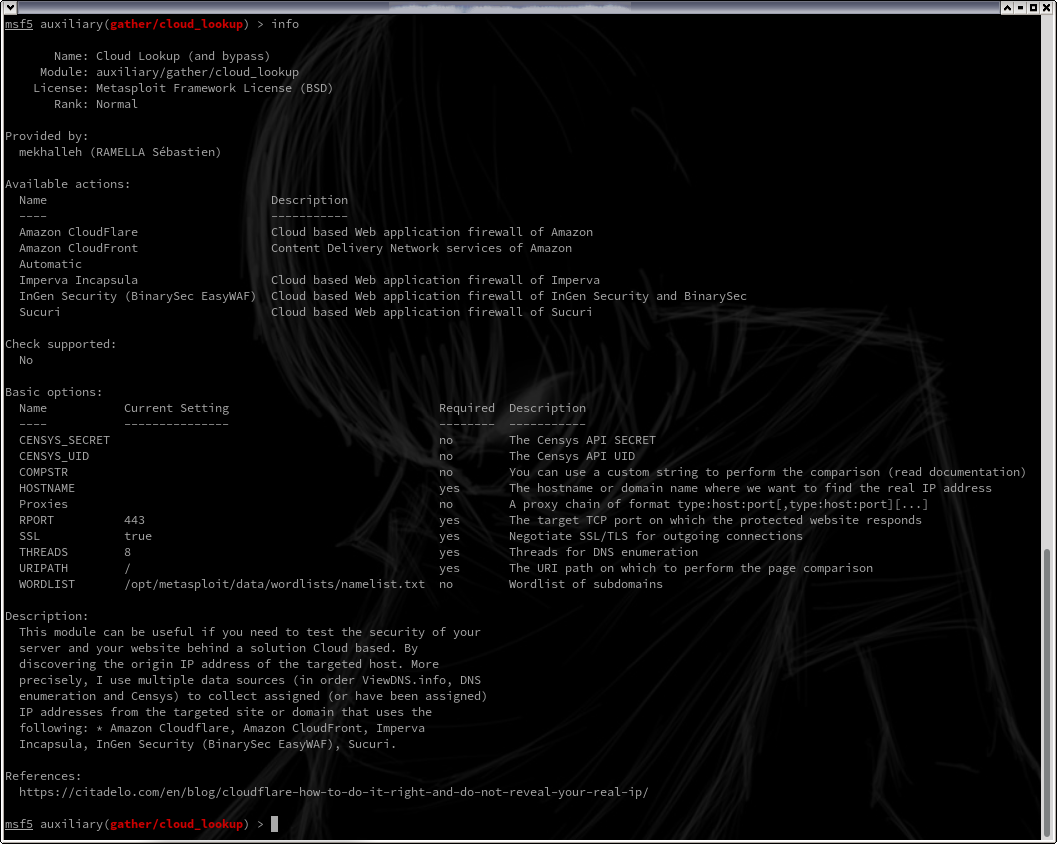
This module can be useful if you need to test the security of your server and your website behind a solution Cloud based. By discovering the origin IP address of the targeted host.
More precisely, this module uses multiple data sources (in order ViewDNS.info, DNS enumeration and Censys) to collect assigned (or have been assigned) IP addresses from the targeted site or domain that uses the following:
- Amazon Cloudflare
- Amazon CloudFront
- ArvanCloud
- Envoy Proxy
- Fastly
- Stackpath Fireblade,
- Stackpath MaxCDN
- Imperva Incapsula
- InGen Security (BinarySec EasyWAF)
- KeyCDN
- Netlify
- Sucuri
You can now use the 'NoWAFBypass' action to retrieve all occurence of the websites without any detections methods.
Of course this requires a manual check, but it is very useful ...
TODO:
- Get Stackpath IP addresses for blacklist that and improve detection
- Obtain Microsoft AzureCloud IP addresses directly from Microsoft rather than the current source
- Grab/Parse SPF value from DNS query for extract IP addresses :)
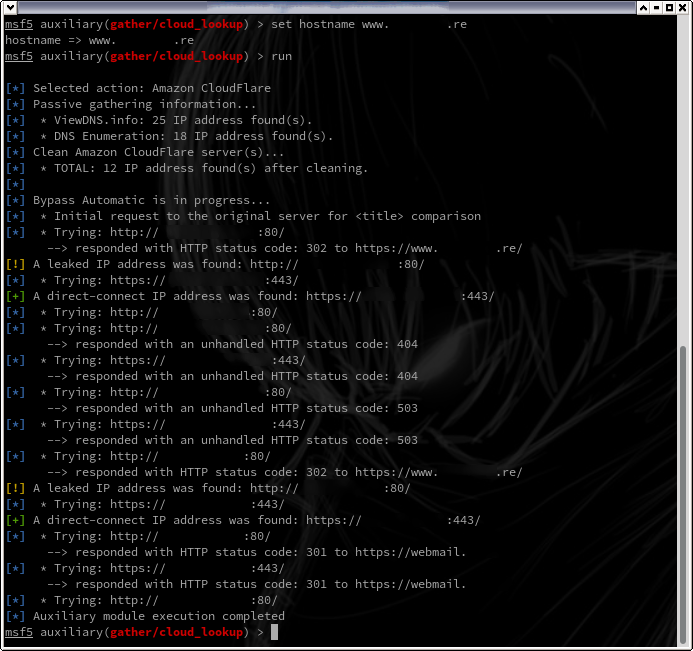
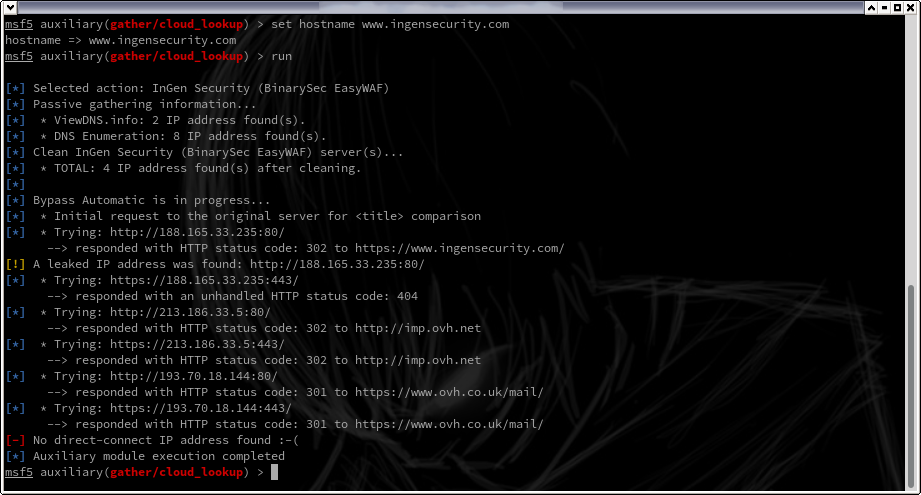
If successful, you must be able to obtain the IP(s) address of the website as follows:
In this case 'A direct-connect IP address was found' is reported.
However, some disreputable administrators used a simple redircetion (301 and 302) to force the passage through the WAF. This makes the IP address leak in the 'location' parameter of the HTTP header.
In this case 'A leaked IP address was found' is displayed but the bypass is NOT effective.